一、靶机介绍
https://github.com/Orange-Cyberdefense/GOAD
GOAD is a pentest active directory LAB project. The purpose of this lab is to give pentesters a vulnerable Active directory environment ready to use to practice usual attack techniques.
二、搭建过程
| 靶场基于的虚拟机 | vmware |
|---|---|
| 操作系统 | ubuntu 23.10 |
| 分配的内存 | 24G |
| 磁盘空间 | 200G |
https://mirrors.tuna.tsinghua.edu.cn/ubuntu-releases/mantic/ubuntu-23.10.1-desktop-amd64.iso
1、安装Vmware-Tools
sudo aot-get install open-vm-tools-desktop2、开始更新系统
sudo apt update
sudo apt upgrade
3、安装virtualbox
sudo apt install virtualbox
4、下载最新版的vagrant
https://releases.hashicorp.com/vagrant/
wget https://releases.hashicorp.com/vagrant/2.4.1/vagrant_2.4.1-1_amd64.deb
sudo apt install ./vagrant_2.4.1-1_amd64.deb
vagrant --version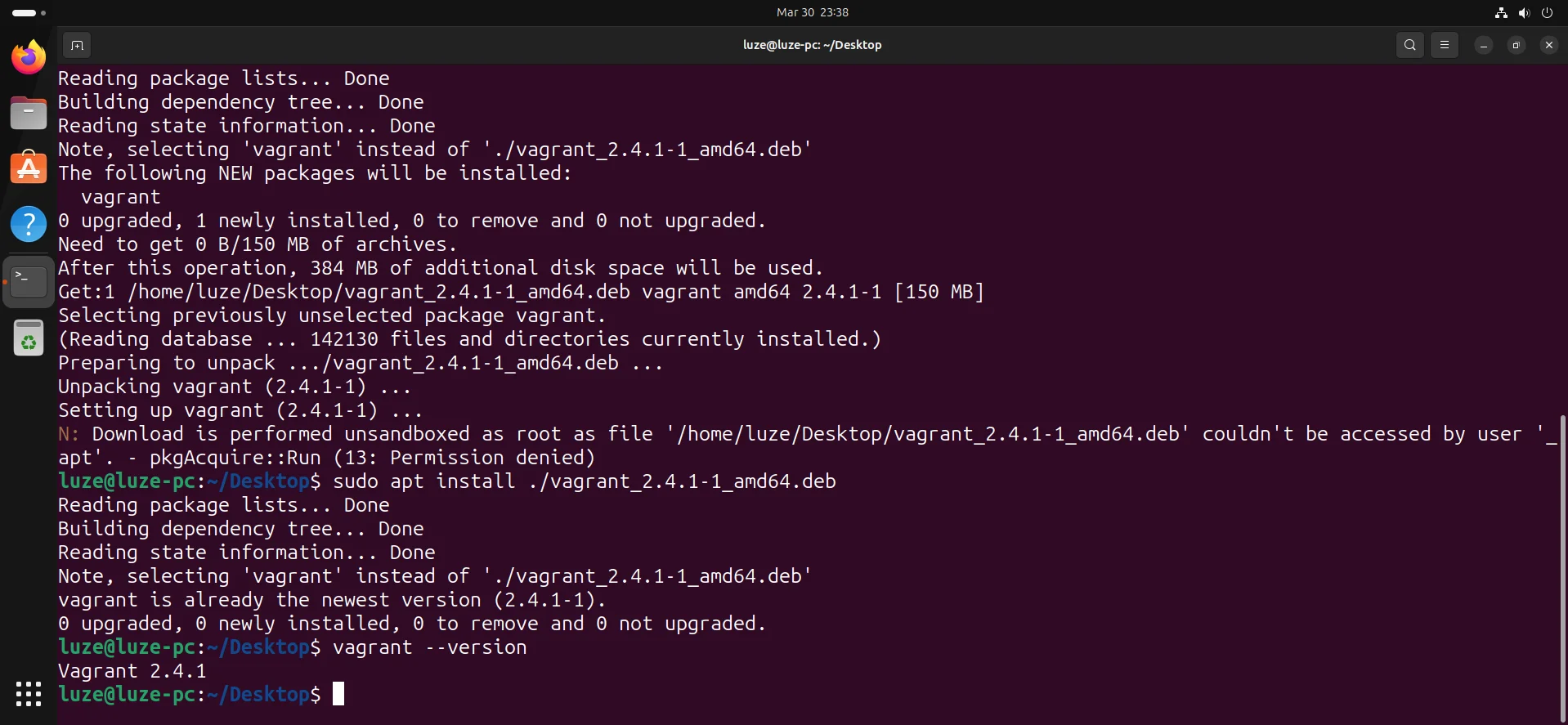
5、安装python3环境
sudo apt install python3-pip
pip3 --version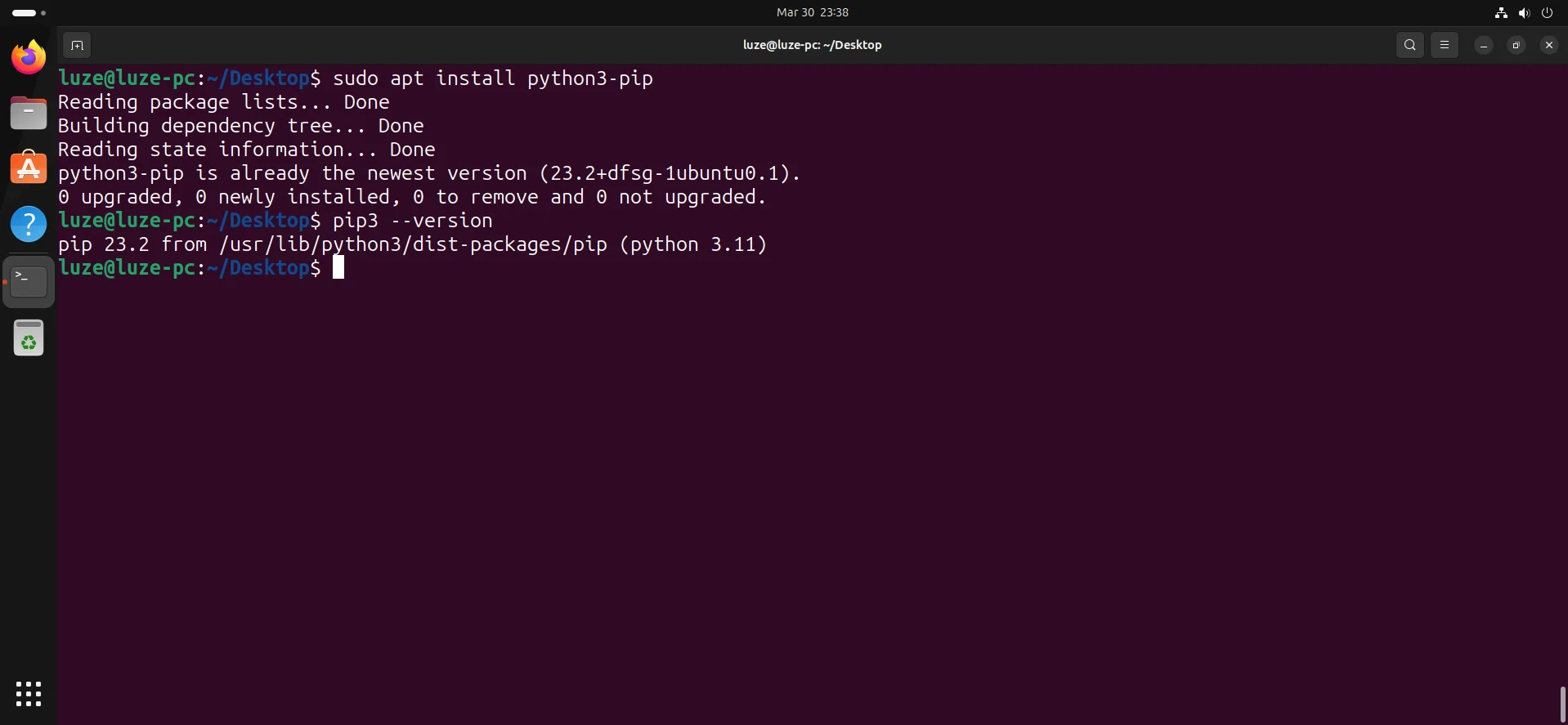
6、安装python3的虚拟环境
sudo apt install python3-venv
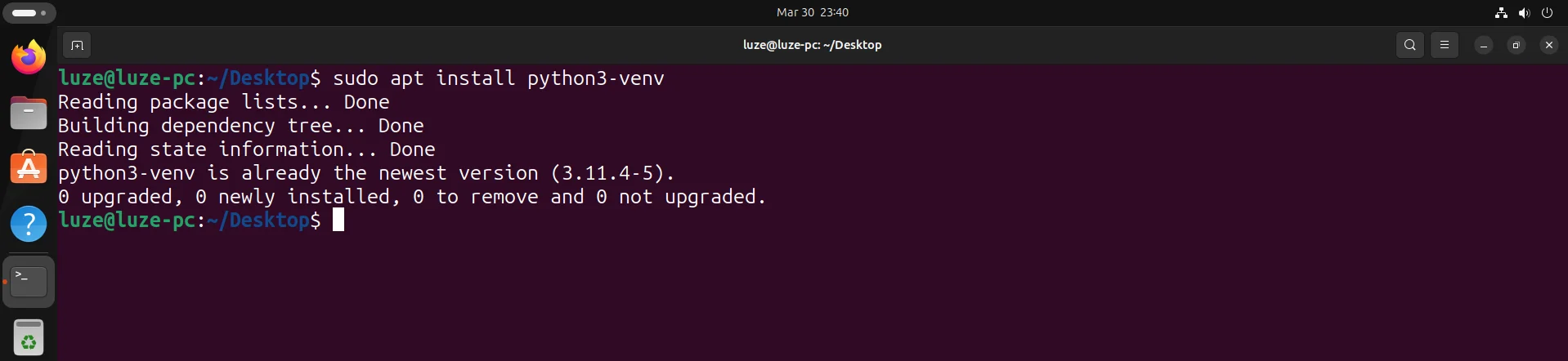
7、安装git
sudo apt-get install git-all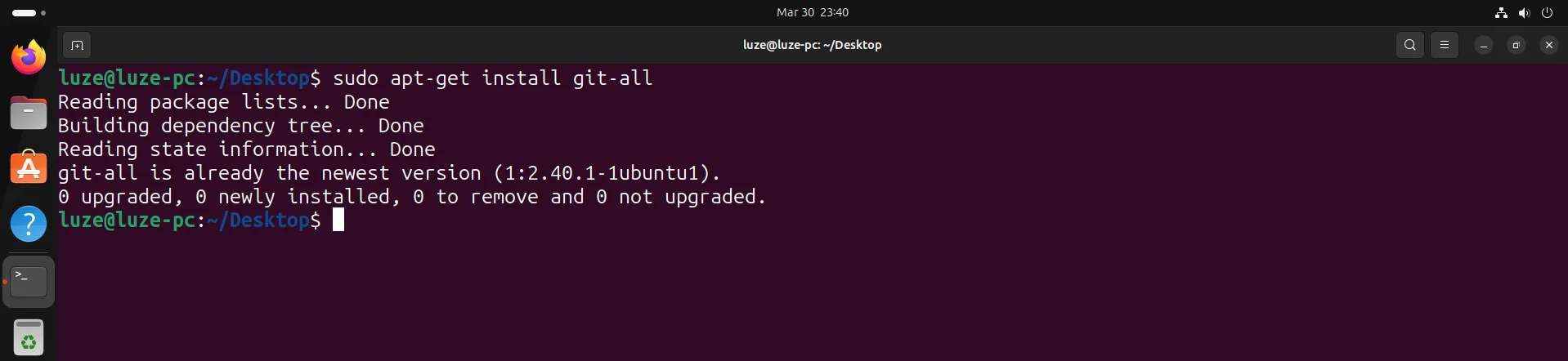
8、下载源码到用户家目录
cd ~/
git clone https://github.com/Orange-Cyberdefense/GOAD.git9、创建python的虚拟环境
python3 -m venv venvGOAD
10、启动虚拟环境
cd GOAD/ansible
source ~/venvGOAD/bin/activate
11、安装 ansible 模块
python3 -m pip install ansible-core==2.12.6
12、安装pywinrm
python3 -m pip install pywinrm
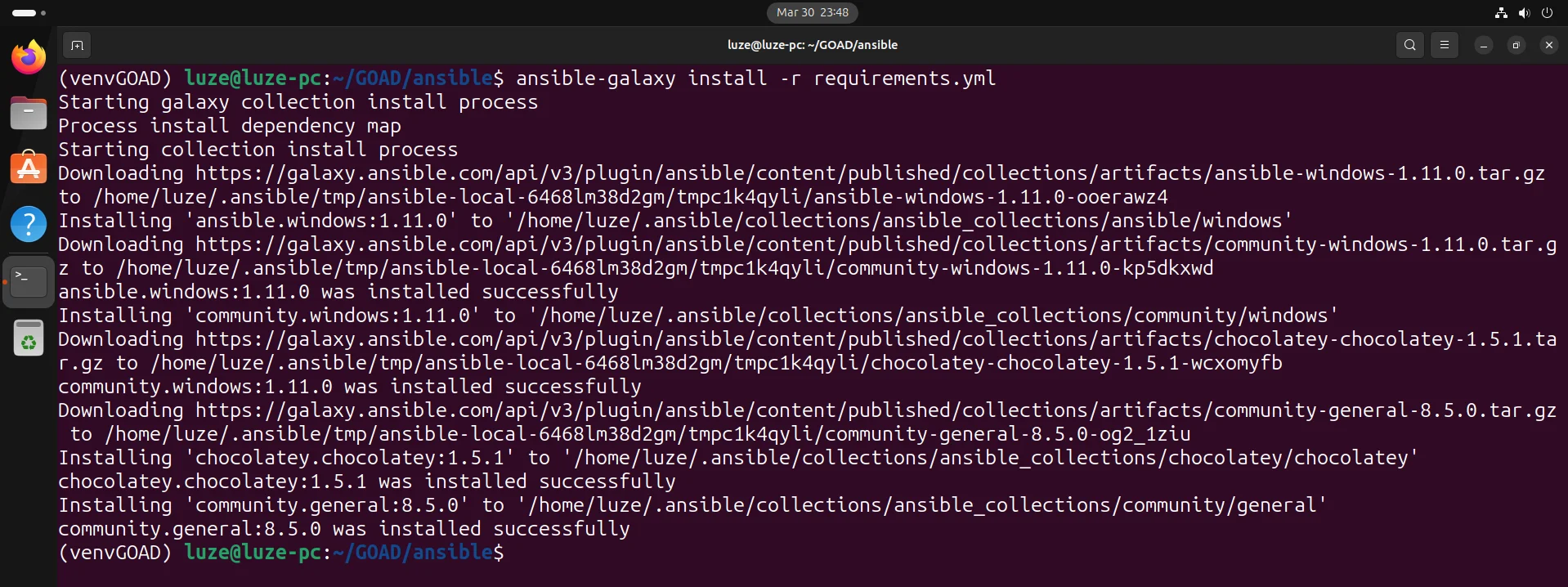
13、安装galaxy依赖
ansible-galaxy install -r requirements.yml
14、测试环境是否安装完毕
cd ..
./goad.sh -t check -l GOAD -p virtualbox -m local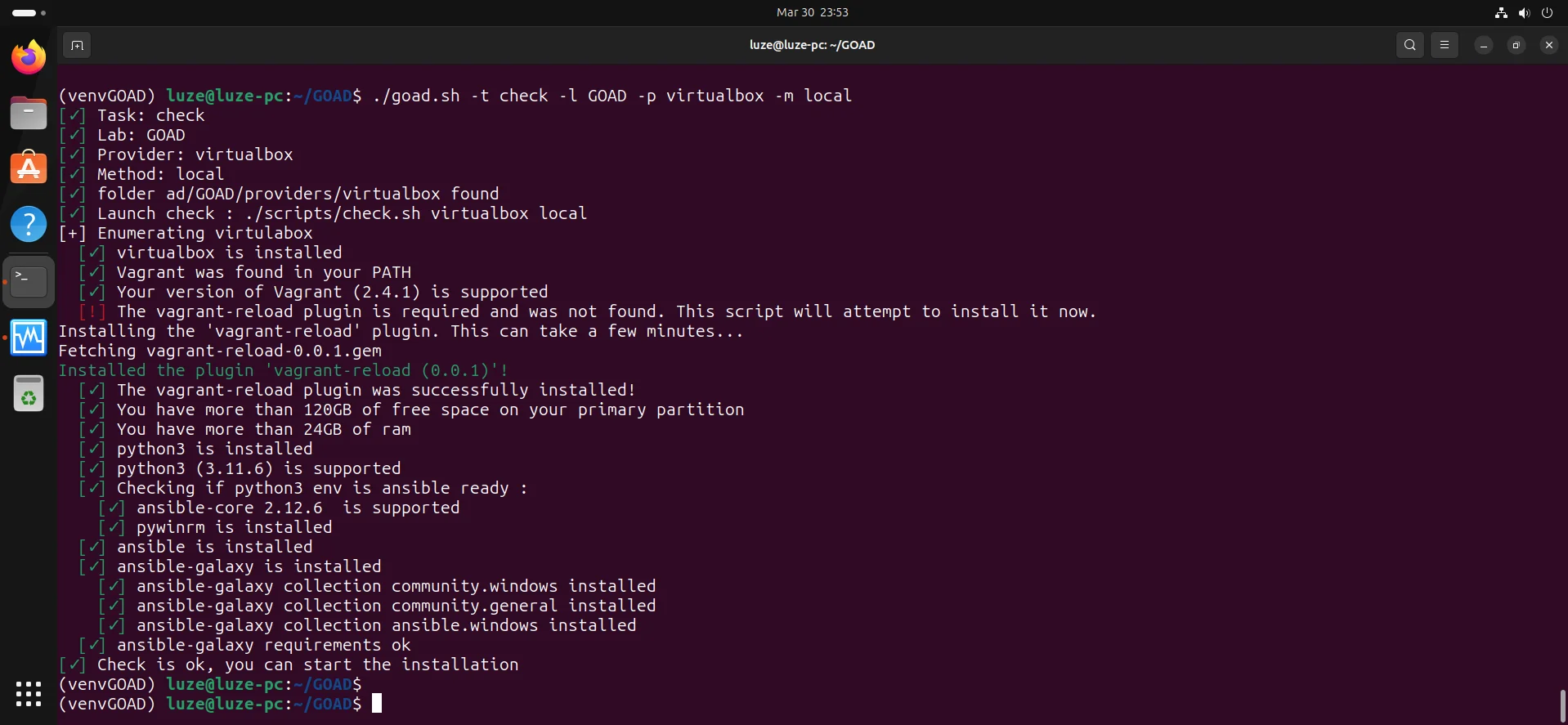
检查没问题
15、安装镜像
进入 ad/GOAD/provider/virtualbox
cd ad/GOAD/providers/virtualbox/
vagrant upGOAD-DC01
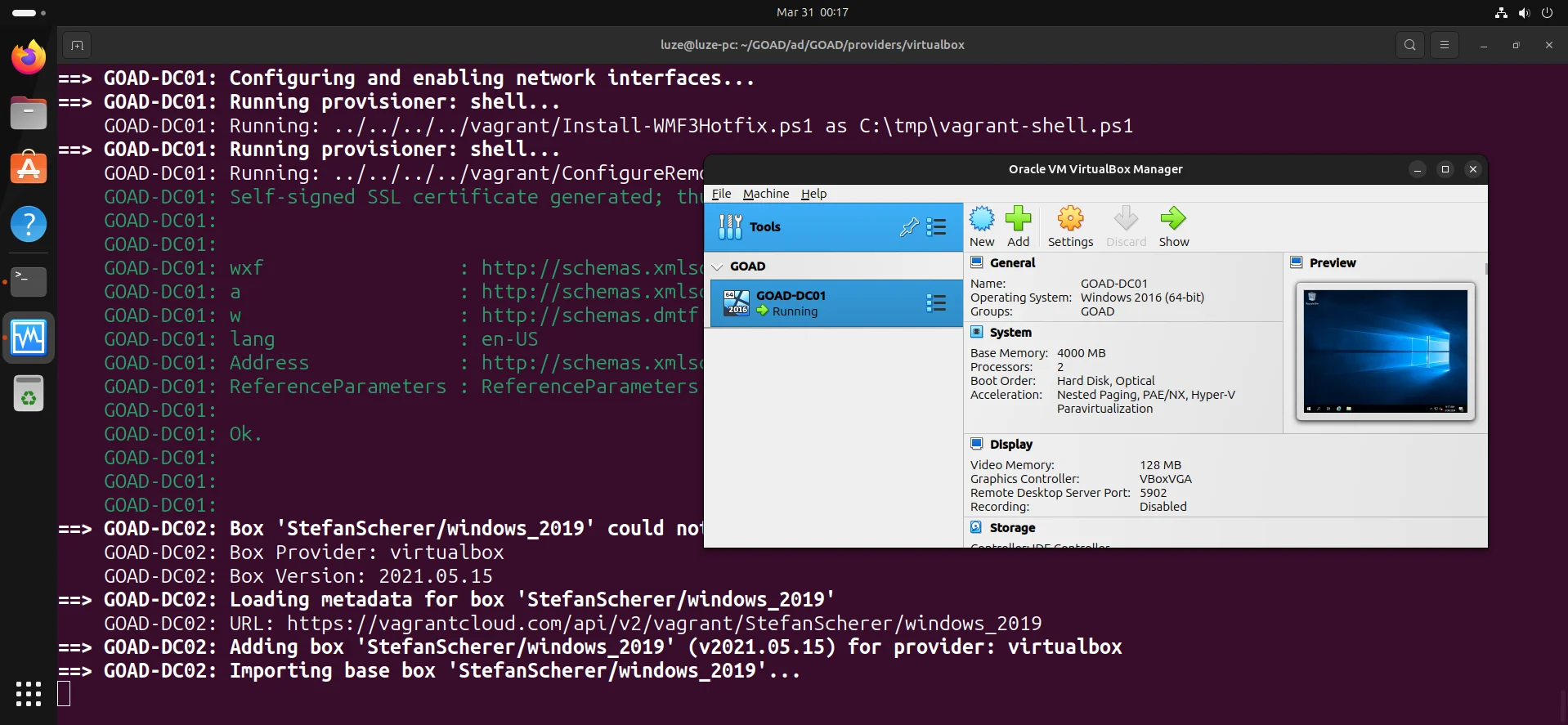
GOAD-DC02
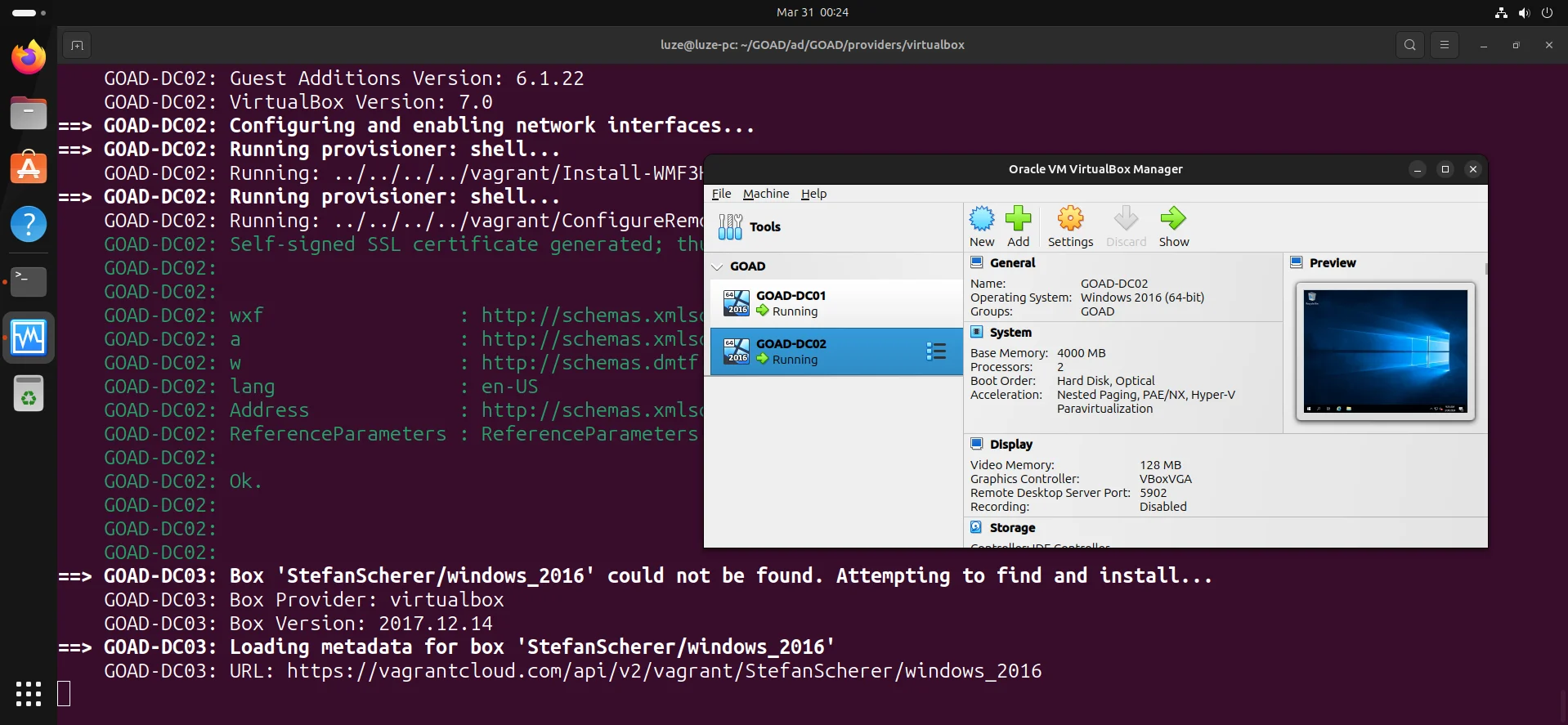
GOAD-DC03
GOAD-SRV02
GOAD-SRV03
16、环境配置
然后继续进入~/GOAD/ansible
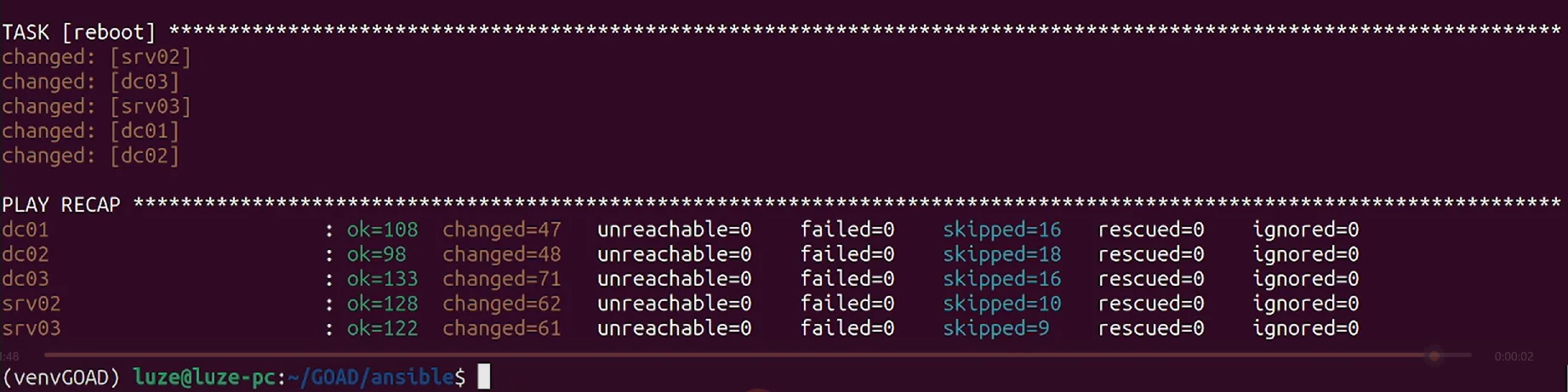
ansible-playbook -i ../ad/GOAD/data/inventory -i ../ad/GOAD/providers/virtualbox/inventory main.yml接下来就是漫长的等待
安装完毕
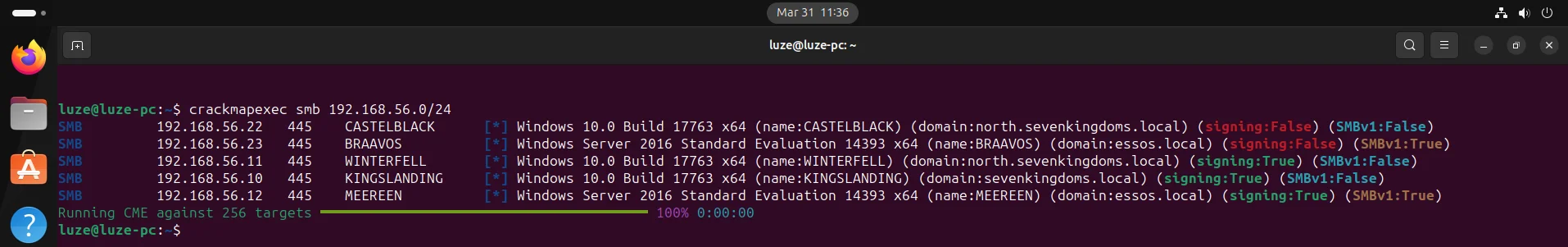
17、验证是否成功
安装cme
sudo apt install snapd
sudo snap install crackmapexec
测试是否成功
crackmapexec smb 192.168.56.0/24